At minimum two study institutes located in Russia and a third probably target in Belarus have been at the acquiring finish of an espionage attack by a Chinese country-condition state-of-the-art persistent danger (APT).
The attacks, codenamed “Twisted Panda,” appear in the backdrop of Russia’s armed forces invasion of Ukraine, prompting a large variety of danger actors to swiftly adapt their strategies on the ongoing conflict to distribute malware and phase opportunistic attacks.
They have materialized in the type of social engineering techniques with topical war and sanctions-themed baits orchestrated to trick prospective victims into clicking destructive links or opening weaponized documents.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Israeli cybersecurity agency Examine Point, which disclosed aspects of the latest intelligence-collecting procedure, attributed it a Chinese risk actor, with connections to that of Stone Panda (aka APT 10, Cicada, or Potassium) and Mustang Panda (aka Bronze President, HoneyMyte, or RedDelta).
Contacting it a continuation of “a lengthy-functioning espionage operation against Russian-similar entities that has been in procedure given that at minimum June 2021,” most current traces of the activity is mentioned to have been observed as a short while ago as April 2022.
Targets integrated two protection research establishments belonging to the Russian condition-owned defense conglomerate Rostec Company and an unfamiliar entity positioned in the Belarusian town of Minsk.
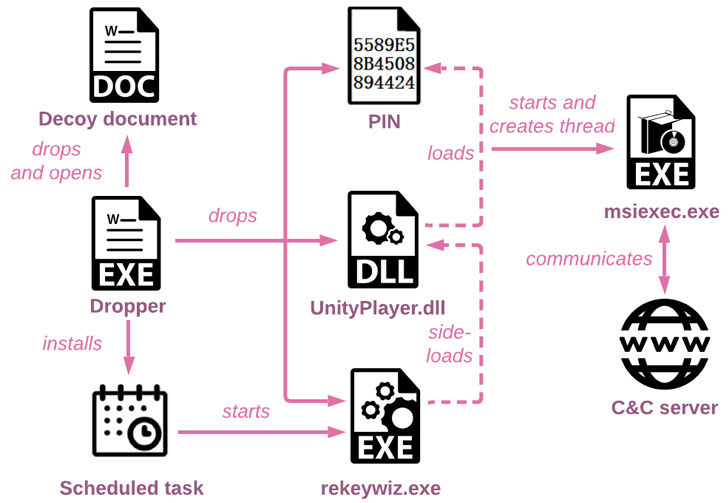
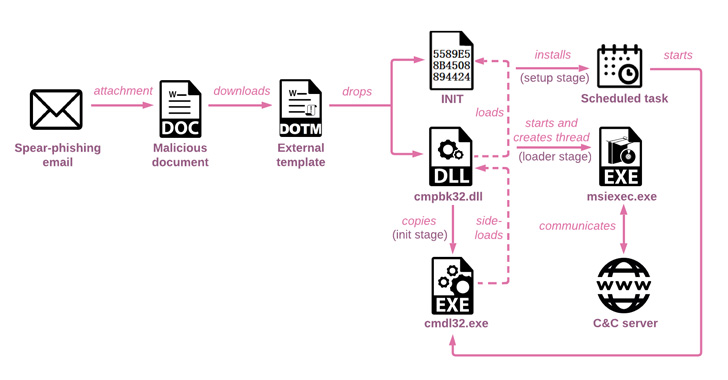
The phishing attacks commenced with emails that have a hyperlink masquerading as the Health Ministry of Russia, but in reality is an attacker-managed domain, as well as a decoy Microsoft Phrase doc built to trigger the infection and fall a loader.
The 32-little bit DLL (“cmpbk32.dll”), aside from establishing persistence by means of a scheduled process, is also accountable for executing a second-stage multi-layered loader, which is subsequently unpacked to operate the last payload in memory.
The injected payload, a beforehand undocumented backdoor named Spinner, can make use of innovative tactics this sort of as manage move flattening to conceal the software move, earlier discovered as put to use by each Stone Panda and Mustang Panda in their attacks.
“These tools are in progress considering that at least March 2021 and use sophisticated evasion and anti-investigation tactics these as multi-layer in-memory loaders and compiler-stage obfuscations,” Look at Place explained.

Inspite of its intricate code composition, Spinner is a barebones implant that’s only equipped to enumerate compromised hosts and operate added payloads retrieved from a distant server.
Test Place noted that its investigation also discovered an before variant of the backdoor which is dispersed in a equivalent trend, indicating that the marketing campaign has been energetic since June 2021 dependent on the compilation timestamps of the executables.
But in an attention-grabbing twist, when the older edition doesn’t incorporate the anti-reverse engineering strategies, it helps make up for it by sporting added capabilities lacking from Spinner, which include the ability to record and manipulate data files, exfiltrate precious details, and run functioning program instructions and arbitrary downloaded payloads.
“In less than a yr, the actors considerably improved the infection chain and produced it far more advanced,” the researchers stated. “All the operation from the outdated campaign was preserved, but it was break up amongst various factors earning it harder to review or detect just about every phase.”
“The evolution of the applications and approaches all through this time period indicates that the actors at the rear of the marketing campaign are persistent in achieving their plans in a stealthy way.”
Discovered this report intriguing? Observe THN on Facebook, Twitter and LinkedIn to browse a lot more special written content we publish.
Some parts of this posting are sourced from:
thehackernews.com

 Why don’t we ever hear about ransomware demands in the tens of millions of dollars?
Why don’t we ever hear about ransomware demands in the tens of millions of dollars?