A new ChromeLoader malware campaign has been noticed staying dispersed via virtual challenging disk (VHD) information, marking a deviation from the ISO optical disc picture structure.
“These VHD files are becoming distributed with filenames that make them surface like both hacks or cracks for Nintendo and Steam games,” AhnLab Security Crisis reaction Center (ASEC) mentioned in a report past 7 days.
ChromeLoader (aka Choziosi Loader or ChromeBack) at first surfaced in January 2022 as a browser-hijacking credential stealer but has due to the fact progressed into a far more potent, multifaceted menace able of thieving sensitive knowledge, deploying ransomware, and even dropping decompression bombs.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The principal intention of the malware is to compromise web browsers like Google Chrome, and modify the browser options to intercept and immediate visitors to doubtful promotion websites. What is additional, ChromeLoader has emerged as a conduit to carry out click fraud by leveraging a browser extension to monetize clicks.
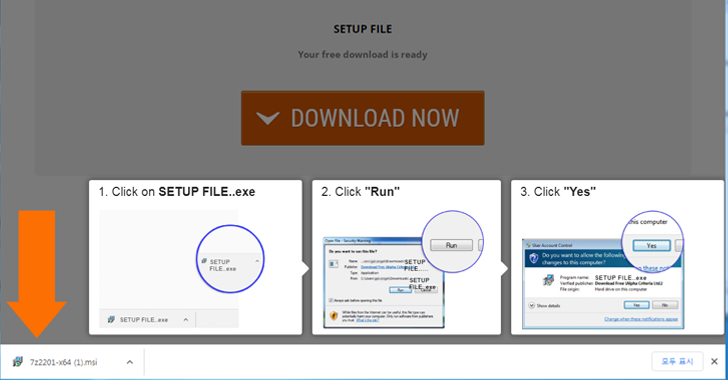
Since arriving on the scene, the malware has gone as a result of several versions, several of them geared up with capabilities to split into the two Windows and macOS techniques. The change to VHD information is still one more signal that the campaign has absent by means of a lot of modifications around the previous number of months.
The infection chain suggests that customers wanting for pirated program and movie activity cheats are the main targets, leading to the obtain of VHD data files from fraudulent websites showing on look for success internet pages.
Some of the recreation titles and preferred computer software made use of are Elden Ring, Dark Souls III, Pink Dead Redemption 2, Need for Speed, Simply call of Duty, The Legend of Zelda: Breath of the Wild, Mario Kart 8 Deluxe, Tremendous Mario Odyssey, Microsoft Office environment, and Adobe Photoshop.
“When a VHD file is downloaded through this course of action, the person can simply blunder the malicious VHD file for a game-associated program,” ASEC scientists reported. “Disguising malware as match hacks and crack applications is a system employed by many menace actors.”
To mitigate these types of challenges, it is really advised that end users chorus from adhering to suspicious backlinks and down load software package only from official sources.
Discovered this post appealing? Comply with us on Twitter and LinkedIn to examine far more exceptional information we article.
Some parts of this short article are sourced from:
thehackernews.com


 North Carolina Business Magnate Indicted in $2bn Fraud Case
North Carolina Business Magnate Indicted in $2bn Fraud Case