The U.S. Cybersecurity and Infrastructure Security Company (CISA) and Federal Bureau of Investigation (FBI) have revealed a joint advisory with regards to the energetic exploitation of a just lately disclosed critical flaw in Development Software’s MOVEit Transfer application to drop ransomware.
“The Cl0p Ransomware Gang, also identified as TA505, reportedly commenced exploiting a beforehand not known SQL injection vulnerability in Progress Software’s managed file transfer (MFT) resolution regarded as MOVEit Transfer,” the companies explained.
“Internet-going through MOVEit Transfer web programs were being infected with a web shell named LEMURLOOT, which was then applied to steal info from fundamental MOVEit Transfer databases.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The prolific cybercrime gang has considering the fact that issued an ultimatum to numerous impacted companies, urging them to get in touch by June 14, 2023, or risk getting all their stolen information released.

Microsoft is tracking the activity below the moniker Lace Tempest (aka Storm-0950), which has also been implicated in the exploitation of a critical security vulnerability in PaperCut servers.
Active because at minimum February 2019, the adversary has been connected to a broad range of pursuits in the cybercrime ecosystem, which includes working a ransomware-as-a-company (RaaS) and performing as an affiliate for other RaaS techniques.
It has also been noticed acting as an first entry broker (IAB) to gain off entry to compromised business networks and also as a buyer of other IABs, underscoring the interconnected character of the menace landscape.
 Resource: Kroll
Resource: Kroll
The abuse of CVE-2023-34362, an SQL injection flaw in MOVEit Transfer, is a sign of the adversary repeatedly looking for zero-day exploits in internet-struggling with programs and using them to their advantage in order to extort victims.
It really is worthy of noting that Cl0p carried out equivalent mass exploitation attacks on other managed file transfer purposes this kind of as Accellion FTA and GoAnywhere MFT in excess of the earlier calendar year.
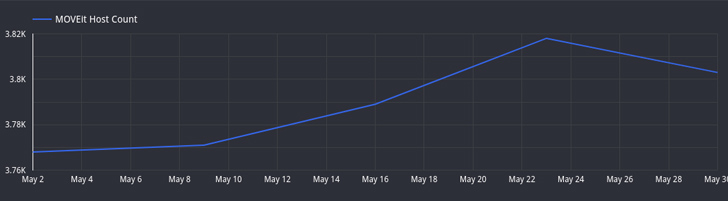
Attack surface administration business Censys claimed it has noticed a drop in the number of hosts operating uncovered MOVEit Transfer situations from above 3,000 hosts to tiny extra than 2,600.
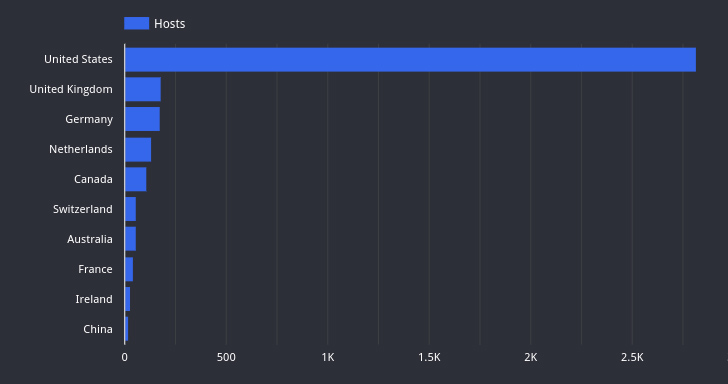
“Various of these hosts are related with higher-profile organizations, such as multiple Fortune 500 companies and each state and federal authorities agencies,” Censys observed, highlighting finance, technology, and health care as the sectors with the most exposures.
Future WEBINAR🔐 Mastering API Security: Comprehension Your Correct Attack Area
Discover the untapped vulnerabilities in your API ecosystem and get proactive methods in direction of ironclad security. Be part of our insightful webinar!
Join the Session.wn-button,.wn-label,.wn-label:immediately aftershow:inline-block.check out_two_webinarmargin:20px 10px 30px 0background:#f9fbffcolor:#160755padding: 5%border:2px sound #d9deffborder-radius:10pxtext-align:leftbox-shadow:10px 10px #e2ebff-webkit-border-top-remaining-radius:25px-moz-border-radius-topleft:25px-webkit-border-base-correct-radius:25px-moz-border-radius-bottomright:25px.wn-labelfont-size:13pxmargin:20px 0font-excess weight:600letter-spacing:.6pxcolor:#596cec.wn-label:soon afterwidth:50pxheight:6pxcontent:”border-top rated:2px strong #d9deffmargin: 8px.wn-titlefont-size:21pxpadding:10px 0font-body weight:900text-align:leftline-peak:33px.wn-descriptiontextual content-align:leftfont-measurement:15.6pxline-height:26pxmargin:5px !importantcolor:#4e6a8d.wn-buttonpadding:6px 12pxborder-radius:5pxbackground-shade:#4469f5font-dimension:15pxcolor:#fff!importantborder:0line-height:inherittext-decoration:none!importantcursor:pointermargin:15px 20pxfloat:leftfont-pounds:500letter-spacing:.2px
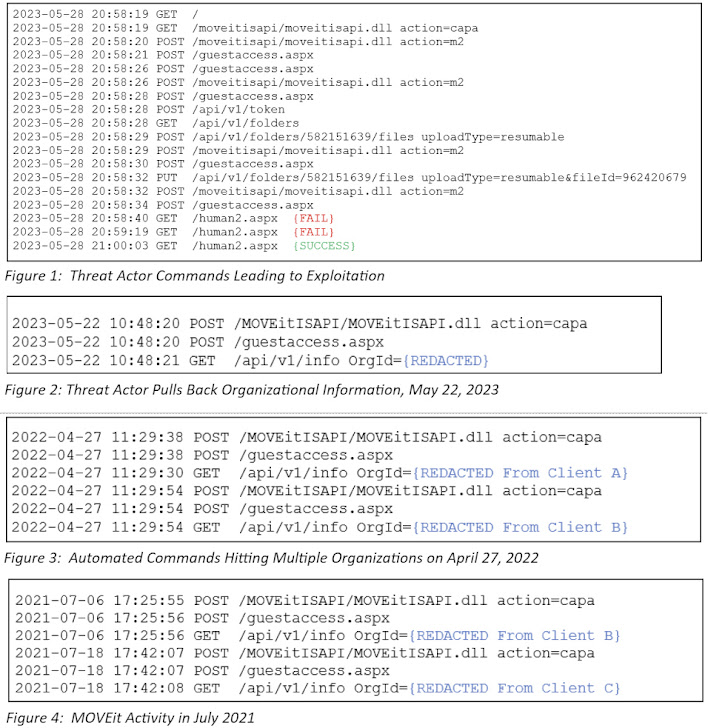
Kroll, in an analysis shared with The Hacker News, stated it determined exercise indicating that the Clop threat actors ended up probable experimenting with approaches to exploit this specific flaw in April 2022 and as considerably back again as July 2021.
The acquiring is notably considerable as it serves to illustrate the attacker’s technical experience and the organizing that has absent into staging the intrusions significantly ahead of the recent wave of exploitations commenced.
“Commands in the course of the July 2021 time body appeared to be run about a extended volume of time, suggesting that screening may perhaps have been a manual course of action at that issue prior to the team produced an automated resolution that it began testing in April 2022,” Kroll stated.
The July 2021 exploitation is reported to have originated from an IP address (45.129.137[.]232) that was formerly attributed to the Cl0p actor in connection with attempts to exploit flaws in SolarWinds Serv-U product or service all around the exact time.
“This is the third time Cl0p ransomware group have applied a zero day in webapps for extortion in three several years,” security researcher Kevin Beaumont claimed. “In all a few situations they ended up merchandise with security in the branding.”
Uncovered this report exciting? Comply with us on Twitter and LinkedIn to read through far more exclusive written content we post.
Some pieces of this write-up are sourced from:
thehackernews.com


 Interpol: Human Trafficking is Fueling Fraud Epidemic
Interpol: Human Trafficking is Fueling Fraud Epidemic