Poorly managed Microsoft SQL (MS SQL) servers are the concentrate on of a new marketing campaign that’s built to propagate a category of malware termed CLR SqlShell that eventually facilitates the deployment of cryptocurrency miners and ransomware.
“Related to web shell, which can be put in on web servers, SqlShell is a malware strain that supports a variety of functions soon after staying installed on an MS SQL server, these kinds of as executing instructions from menace actors and carrying out all kinds of destructive actions,” AhnLab Security Unexpected emergency response Center (ASEC) mentioned in a report revealed past 7 days.
A saved process is a subroutine that is made up of a established of Structured Query Language (SQL) statements for use across several applications in a relational database management technique (RDBMS).

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
CLR (quick for prevalent language runtime) saved techniques – accessible in SQL Server 2005 and later – refer to stored techniques that are written in a .NET language these kinds of as C# or Visual Standard.

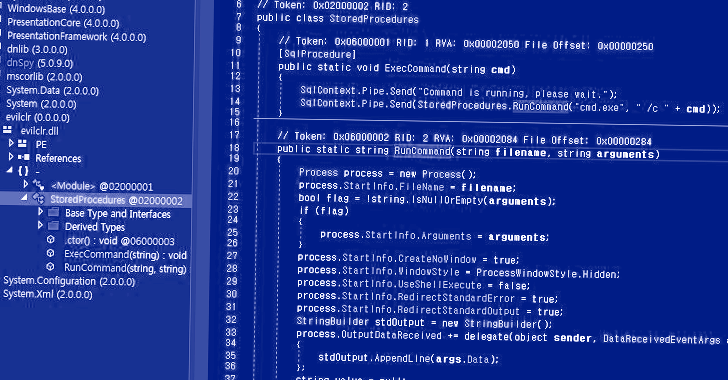
The attack technique learned by the South Korean cybersecurity business entails the use of CLR stored technique to set up the malware in MS SQL servers using the xp_cmdshell command, which spawns a Windows command shell and passes an instruction as input for execution.
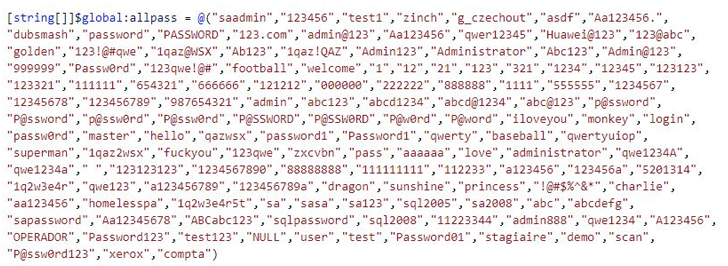
Some of the tactics used by menace actors, together with people linked with LemonDuck, MyKings (aka DarkCloud or Smominru), and Vollgar, issue the exploitation of internet-uncovered MS SQL servers by means of brute-power and dictionary attacks to operate xp_cmdshell commands and OLE saved strategies and execute malware.
The use of CLR saved procedures is the hottest addition to this checklist, with attackers using edge of SqlShell routines to obtain following-stage payloads these types of as Metasploit and cryptocurrency miners like MrbMiner, MyKings, and LoveMiner.
Upcoming WEBINARLearn to Quit Ransomware with Genuine-Time Defense
Be part of our webinar and learn how to end ransomware attacks in their tracks with real-time MFA and company account protection.
Save My Seat!
What is far more, SqlShells named SqlHelper, CLRSQL, and CLR_module have been used by distinct adversaries to escalate privileges on compromised servers and launch ransomware, proxyware, and integrate capabilities to carry out reconnaissance efforts in focused networks.
“SqlShell can install additional malware these types of as backdoors, coin miners, and proxyware, or it can execute destructive commands gained from menace actors in a way similar to WebShell,” ASEC said.
Discovered this write-up attention-grabbing? Abide by us on Twitter and LinkedIn to read far more exceptional content we put up.
Some parts of this short article are sourced from:
thehackernews.com

 Former Ubiquiti Employee Gets 6 Years in Jail for $2 Million Crypto Extortion Case
Former Ubiquiti Employee Gets 6 Years in Jail for $2 Million Crypto Extortion Case