An assessment of leaked chats from the infamous Conti ransomware team earlier this year has uncovered that the syndicate has been functioning on a established of firmware attack approaches that could supply a path to accessing privileged code on compromised devices.
“Handle in excess of firmware provides attackers nearly unmatched powers both of those to immediately induce harm and to empower other extensive-time period strategic aims,” firmware and components security company Eclypsium explained in a report shared with The Hacker Information.
“This kind of degree of access would enable an adversary to trigger irreparable problems to a program or to build ongoing persistence that is just about invisible to the functioning process.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

Specially, this incorporates attacks aimed at embedded microcontrollers such as the Intel Management Engine (ME), a privileged component that is portion of the company’s processor chipsets and which can entirely bypass the working program.
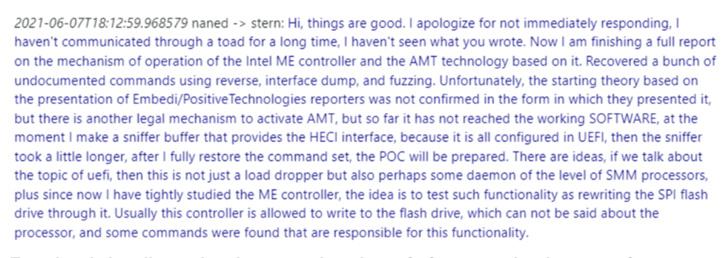
The conversations amongst the Conti members, which leaked after the team pledged its aid to Russia in the latter’s invasion of Ukraine, have drop gentle on the syndicate’s tries to mine for vulnerabilities related to ME firmware and BIOS create defense.
This entailed discovering undocumented commands and vulnerabilities in the ME interface, attaining code execution in the ME to entry and rewrite the SPI flash memory, and dropping Technique Management Manner (SMM)-amount implants, which could be leveraged to even modify the kernel.
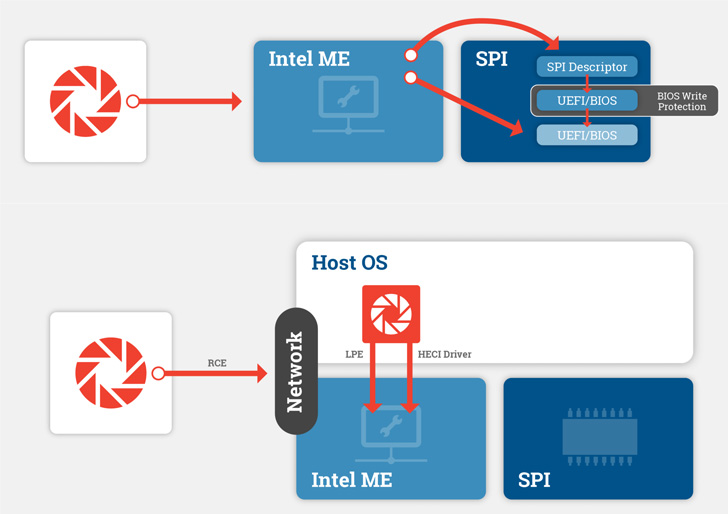
The research in the end manifested in the sort of a proof-of-strategy (PoC) code in June 2021 that can attain SMM code execution by getting manage more than the ME immediately after obtaining initial accessibility to the host by usually means of common vectors like phishing, malware, or a supply chain compromise, the leaked chats demonstrate.

“By shifting emphasis to Intel ME as very well as focusing on equipment in which the BIOS is publish shielded, attackers could effortlessly discover much additional offered target devices,” the researchers explained.
That is not all. Manage around the firmware could also be exploited to get extensive-phrase persistence, evade security remedies, and result in irreparable technique hurt, enabling the menace actor to mount destructive attacks as witnessed through the Russo-Ukrainian war.
“The Conti leaks uncovered a strategic change that moves firmware attacks even additional absent from the prying eyes of traditional security tools,” the researchers explained.
“The shift to ME firmware provides attackers a significantly more substantial pool of potential victims to attack, and a new avenue to achieving the most privileged code and execution modes out there on contemporary methods.”
Located this write-up intriguing? Adhere to THN on Facebook, Twitter and LinkedIn to read additional unique written content we post.
Some parts of this post are sourced from:
thehackernews.com

 Cybercriminals Expand Attack Radius and Ransomware Pain Points
Cybercriminals Expand Attack Radius and Ransomware Pain Points