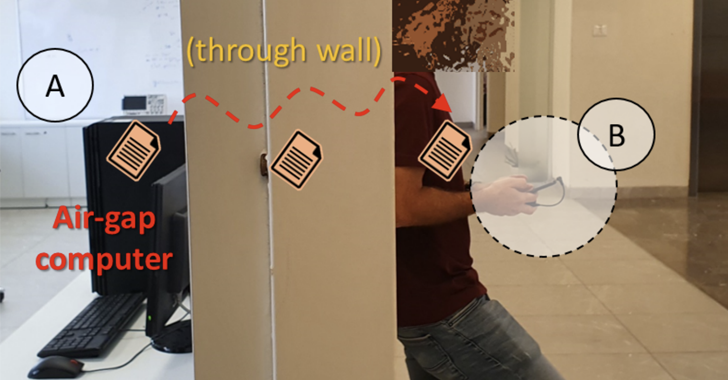
An unconventional details exfiltration method leverages a beforehand undocumented covert channel to leak sensitive data from air-gapped units.
“The data emanates from the air-gapped laptop or computer above the air to a distance of 2 m and more and can be picked up by a close by insider or spy with a cellular phone or notebook,” Dr. Mordechai Guri, the head of R&D in the Cyber Security Exploration Heart in the Ben Gurion College of the Negev in Israel and the head of Offensive-Defensive Cyber Investigation Lab, claimed in a new paper shared with The Hacker News.
The system, dubbed COVID-bit, leverages malware planted on the equipment to make electromagnetic radiation in the -60 kHz frequency band that’s subsequently transmitted and picked up by a stealthy receiving machine in close actual physical proximity.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
This, in flip, is produced possible by exploiting the dynamic electric power consumption of modern computer systems and manipulating the momentary masses on CPU cores.

COVID-bit is the latest procedure devised by Dr. Guri this yr, after SATAn, GAIROSCOPE, and ETHERLED, which are designed to jump above air-gaps and harvest private info.
Air-gapped networks, in spite of their substantial level of isolation, can be compromised by many procedures this kind of as infected USB drives, supply chain attacks, and even rogue insiders.
Exfiltrating the details just after breaching the network, however, is a challenge owing to the absence of internet connectivity, necessitating that attackers concoct distinctive techniques to supply the facts.
The COVID-bit is one particular this sort of covert channel that is utilised by the malware to transmit information and facts by using advantage of the electromagnetic emissions from a component named switched-manner energy offer (SMPS) and employing a mechanism called frequency-change keying (FSK) to encode the binary information.
“By regulating the workload of the CPU, it is doable to govern its electricity consumption and that’s why management the momentary switching frequency of the SMPS,” Dr. Guri clarifies.
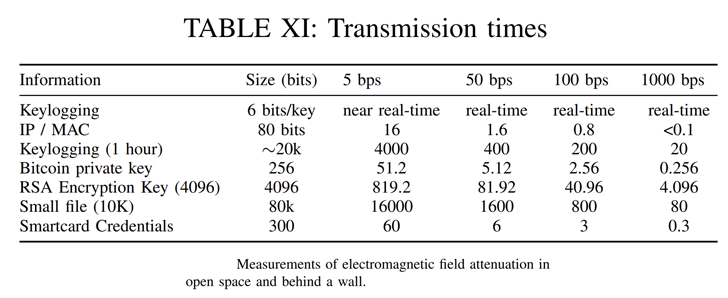
“The electromagnetic radiation produced by this intentional system can be been given from a length applying proper antennas” that price tag as very low as $1 and can be linked to a phone’s 3.5 mm audio jack to seize the very low-frequency alerts at a bandwidth of 1,000 bps.
The emanations are then demodulated to extract the info. The attack is also evasive in that the destructive code isn’t going to demand elevated privileges and can be executed from within just a digital device.
An analysis of the information transmissions reveals that keystrokes can be exfiltrated in in the vicinity of real-time, with IP and MAC addresses taking any where amongst a lot less than .1 seconds to 16 seconds, based on the bitrate.
Countermeasures in opposition to the proposed covert channel consist of carrying out dynamic opcode investigation to flag threats, initiate random workloads on the CPU processors when anomalous exercise is detected, and monitoring or jamming signals in the -60 kHz spectrum.
Observed this write-up exciting? Follow us on Twitter and LinkedIn to go through a lot more exclusive content we write-up.
Some areas of this post are sourced from:
thehackernews.com

 Pet Dog Unmasks Drug Trafficker on Encrypted Chat
Pet Dog Unmasks Drug Trafficker on Encrypted Chat