Several vulnerabilities have been disclosed in Hitachi Vantara’s Pentaho Enterprise Analytics program that could be abused by destructive actors to upload arbitrary facts documents and even execute arbitrary code on the fundamental host program of the application.
The security weaknesses had been reported by researchers Alberto Favero from German cybersecurity organization Hawsec and Altion Malka from Census Labs previously this year, prompting the company to issue required patches to deal with the issues.


Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Pentaho is a Java-centered business enterprise intelligence platform that gives info integration, analytics, on the internet analytical processing (OLAP), and mining capabilities, and counts important businesses and companies like Bell, CERN, Cipal, Logitech, Nasdaq, Telefonica, Teradata, and the Nationwide September 11 Memorial and Museum amongst its consumers.
The listing of flaws, which influence Pentaho Organization Analytics versions 9.1 and decreased, is as follows –
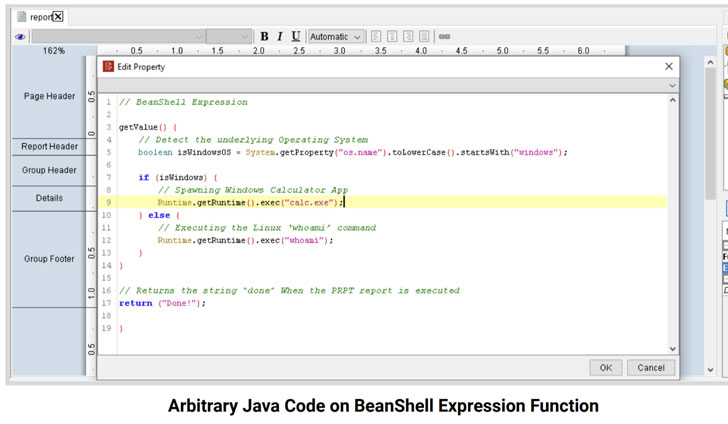
- CVE-2021-31599 (CVSS score: 9.9) – Remote Code Execution as a result of Pentaho Report Bundles
- CVE-2021-31600 (CVSS rating: 4.3) – Jackrabbit Consumer Enumeration
- CVE-2021-31601 (CVSS rating: 7.1) – Inadequate Accessibility Regulate of Data Source Administration
- CVE-2021-31602 (CVSS rating: 5.3) – Authentication Bypass of Spring APIs
- CVE-2021-34684 (CVSS rating: 9.8) – Unauthenticated SQL Injection
- CVE-2021-34685 (CVSS rating: 2.7) – Bypass of Filename Extension Limits
Productive exploitation of the flaws could let authenticated people with sufficient role permissions to add and run Pentaho Report Bundles to run destructive code on the host server and exfiltrate sensitive application details, and circumvent filename extension constraints enforced by the application and add files of any kind.
What is actually more, they could also be leveraged by a reduced-privilege authenticated attacker to retrieve qualifications and connection details of all Pentaho data sources, permitting the party to harvest and transmit knowledge, in addition to enabling an unauthenticated user to execute arbitrary SQL queries on the backend databases and retrieve details.
In gentle of the critical mother nature of the flaws and the risk they pose to the fundamental program, end users of the application are extremely advised to update to the most recent variation.
Found this short article appealing? Observe THN on Fb, Twitter and LinkedIn to browse more special content we article.
Some sections of this report are sourced from:
thehackernews.com


 Securing SaaS Apps — CASB vs. SSPM
Securing SaaS Apps — CASB vs. SSPM