A group of cybersecurity scientists now disclosed details of a new higher-danger vulnerability influencing billions of gadgets worldwide—including servers and workstations, laptops, desktops, and IoT techniques working just about any Linux distribution or Windows method.
Dubbed ‘BootHole’ and tracked as CVE-2020-10713, the reported vulnerability resides in the GRUB2 bootloader, which, if exploited, could likely enable attackers bypass the Secure Boot characteristic and obtain higher-privileged persistent and stealthy obtain to the qualified devices.
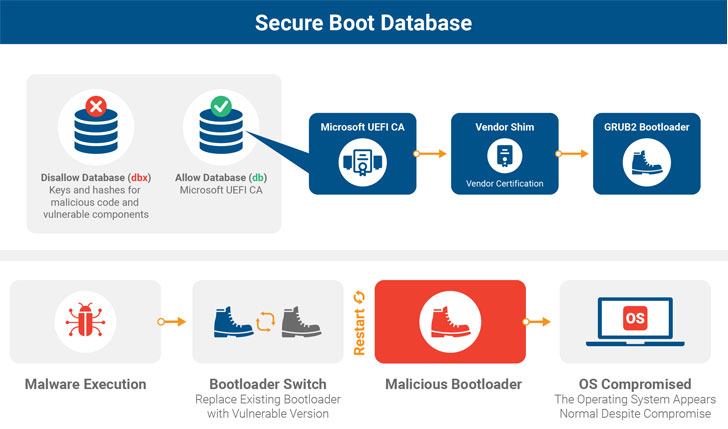
Protected Boot is a security function of the Unified Extensible Firmware Interface (UEFI) that employs a bootloader to load critical factors, peripherals, and the running program though making sure that only cryptographically signed code executes throughout the boot process.
“A person of the specific design and style goals of Secure Boot is to avert unauthorized code, even managing with administrator privileges, from attaining supplemental privileges and pre-OS persistence by disabling Secure Boot or otherwise modifying the boot chain,” the report stated.
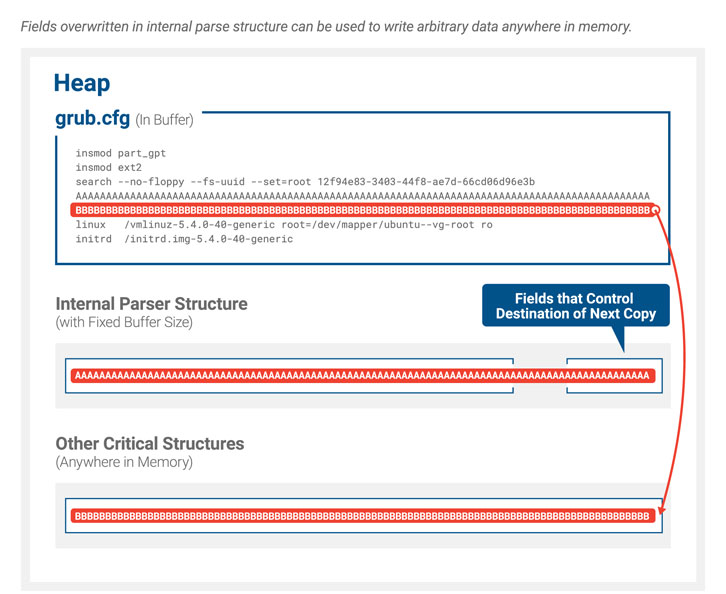
Learned by scientists from Eclypsium, BootHole is a buffer overflow vulnerability that has an effect on all versions of GRUB2 and exists in the way it parses information from the config file, which normally is not signed like other files and executables—leaving an chance for attackers to break the components root of trust mechanism.
To be pointed out, the grub.cfg file is found in the EFI process partition, and so, to modify the file, an attacker however wants an original foothold on the focused technique with admin privileges that would finally offer the attacker with an added escalation of privilege and persistence on the device.
Although GRUB2 is the normal bootloader applied by most Linux techniques, it supports other operating systems, kernels, and hypervisors like XEN as nicely.
“The buffer overflow will allow the attacker to attain arbitrary code execution within just the UEFI execution natural environment, which could be used to run malware, change the boot course of action, directly patch the OS kernel, or execute any quantity of other malicious actions,” researchers reported.
Hence, to exploit BootHole flaw on Windows units, attackers can substitute the default bootloaders mounted on Windows units with a susceptible model of GRUB2 to install the rootkit malware.
“The trouble also extends to any Windows product that employs Safe Boot with the common Microsoft 3rd Bash UEFI Certificate Authority,” the report says.
According to the detailed report researchers shared with The Hacker Information, this vulnerability can lead to major outcomes, and that is mostly mainly because the assault allows hackers to execute malicious code even in advance of the running system boots, generating it tough for security computer software to detect the existence of malware or eliminate it.
Aside from this, the researcher also included that “the UEFI execution surroundings does not have Deal with Space Structure Randomization (ASLR) or Details Execution Avoidance (DEP/NX) or other exploit mitigation systems commonly identified in modern-day running techniques, so generating exploits for this variety of vulnerability is significantly much easier.”
Authorities at Eclypsium have by now contacted connected sector entities, which includes OS vendors and laptop or computer brands, to support them patch the issue.
Having said that, it won’t show up to be an simple job to patch the issue completely. The three-phase mitigation course of action will probable just take a long time for businesses to total patching.
According to Eclypsium, even “mitigation will require new bootloaders to be signed and deployed, and susceptible bootloaders should be revoked to avert adversaries from applying more mature, susceptible variations in an attack.”
In an advisory introduced nowadays, Microsoft acknowledged the issue, informing that it really is “performing to entire validation and compatibility screening of a needed Windows Update that addresses this vulnerability.”
It also suggested people to implement security patches as before long as they are rolled out in the coming months.
In addition to Microsoft, several common Linux distributions have also produced relevant advisories detailing the flaw, feasible mitigations, and timeline on the approaching security patches.
Here’s a checklist for all advisories:

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
- Red Hat (Fedora and RHEL)
- Canonical (Ubuntu)
- SuSE (SLES and OpenSUSE)
- Debian
- VMware
- Microsoft
- HP
Uncovered this post attention-grabbing? Comply with THN on Fb, Twitter and LinkedIn to browse a lot more unique information we publish.


 Rite Aid Drops Facial Recognition Tech
Rite Aid Drops Facial Recognition Tech