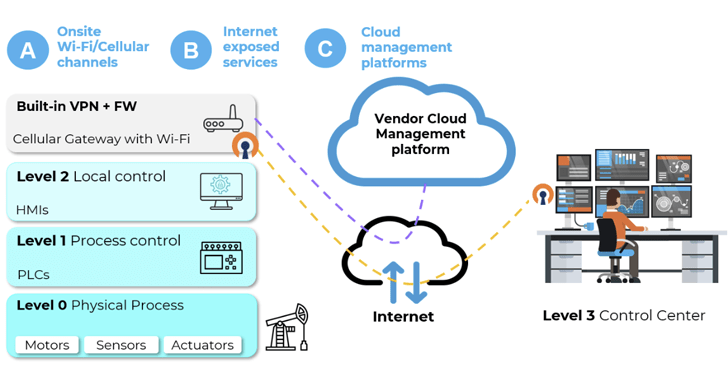
A set of 38 security vulnerabilities has been uncovered in wi-fi industrial internet of items (IIoT) equipment from four distinct vendors that could pose a significant attack floor for risk actors wanting to exploit operational technology (OT) environments.
“Menace actors can exploit vulnerabilities in Wireless IIoT units to acquire first accessibility to inner OT networks,” Israeli industrial cybersecurity firm Otorio explained. “They can use these vulnerabilities to bypass security layers and infiltrate concentrate on networks, putting critical infrastructure at risk or interrupting producing.”
The flaws, in a nutshell, present a distant entry level for attack, enabling unauthenticated adversaries to acquire a foothold and subsequently use it as leverage to spread to other hosts, therefore triggering sizeable injury.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Some of the identified shortcomings could be chained to give an external actor direct accessibility to 1000’s of inside OT networks above the internet, security researcher Roni Gavrilov reported.
Of the 38 defects, 3 influence ETIC Telecom’s Distant Entry Server (RAS) – CVE-2022-3703, CVE-2022-41607, and CVE-2022-40981 – and could be abused to absolutely seize management of susceptible products.
5 other vulnerabilities issue InHand Networks InRouter 302 and InRouter 615 that, if exploited, could final result in command injection, info disclosure, and code execution.
Precisely, it involves taking advantage of issues in the “Gadget Manager” cloud system, which permits operators to carry out remote steps like configuration variations and firmware upgrades, to compromise each individual cloud-managed InRouter unit with root privileges.
Also recognized are two weaknesses in Sierra Wi-fi AirLink Router (CVE-2022-46649 and CVE-2022-46650) that could allow for a reduction of sensitive information and facts and remote code execution. The remaining flaws are even now below accountable disclosure.
The results underscore how OT networks could be place at risk by producing IIoT devices instantly accessible on the internet, proficiently developing a “solitary point of failure” that can bypass all security protections.
Alternatively, area attackers can split into industrial Wi-Fi obtain points and mobile gateways by focusing on on-web site Wi-Fi or cellular channels, leading to adversary-in-the-center (AitM) eventualities with adverse probable influence.
The assaults can array from targeting weak encryption strategies to coexistence attacks aimed at combo chips applied widely in digital equipment.
To pull this off, menace actors can make use of platforms like WiGLE – a database of diverse wi-fi hotspots around the globe – to determine higher-price industrial environments, bodily find them, and exploit the accessibility factors from close proximity, Otorio mentioned.
As countermeasures, it’s encouraged to disable insecure encryption strategies, cover Wi-Fi network names, disable unused cloud administration products and services, and just take techniques to prevent gadgets from staying publicly available.
“The very low complexity of exploit, merged with the wide potential effects, tends to make wi-fi IIoT units and their cloud-dependent administration platforms an enticing concentrate on for attackers on the lookout to breach industrial environments,” the firm explained.
The development also comes as Otorio disclosed details of two substantial-severity flaws in Siemens Automation License Manager (CVE-2022-43513 and CVE-2022-43514) that could be put together to attain distant code execution and privilege escalation. The bugs were being patched by Siemens in January 2023.
Found this short article attention-grabbing? Follow us on Twitter and LinkedIn to go through much more distinctive material we article.
Some components of this posting are sourced from:
thehackernews.com

 THN Webinar – Learn How to Comply with New Cyber Insurance Identity Security Requirements
THN Webinar – Learn How to Comply with New Cyber Insurance Identity Security Requirements