A critical security vulnerability has been disclosed in the Open up Authorization (OAuth) implementation of the software development framework Expo.io.
The shortcoming, assigned the CVE identifier CVE-2023-28131, has a severity ranking of 9.6 on the CVSS scoring procedure. API security firm Salt Labs said the issue rendered expert services applying the framework prone to credential leakage, which could then be applied to hijack accounts and siphon sensitive knowledge.
Less than specified conditions, a threat actor could have taken benefit of the flaw to perform arbitrary steps on behalf of a compromised consumer on various platforms this sort of as Fb, Google, or Twitter.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Expo, equivalent to Electron, is an open supply platform for creating universal indigenous apps that operate on Android, iOS, and the web.
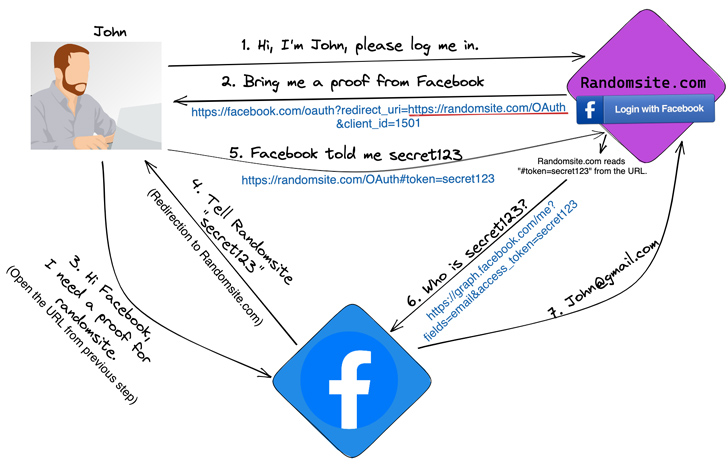
It truly is well worth noting that for the attack to be successful, web sites and apps working with Expo should really have configured the AuthSession Proxy setting for one signal-on (SSO) employing a third-party service provider these as Google and Facebook.
Set in different ways, the vulnerability could be leveraged to send out the key token associated with a indication-in provider (e.g., Fb) to an actor-managed area and use it to seize control of the victim’s account.
This, in transform, is accomplished by tricking the targeted person into clicking on a specifically crafted backlink that could be despatched by using classic social engineering vectors like email, SMS messages, or a doubtful web page.
Expo, in an advisory, stated it deployed a hotfix within just hrs of liable disclosure on February 18, 2023. It is really also advisable that end users migrate from making use of AuthSession API proxies to directly registering deep website link URL strategies with third-party authentication vendors to help SSO functions.
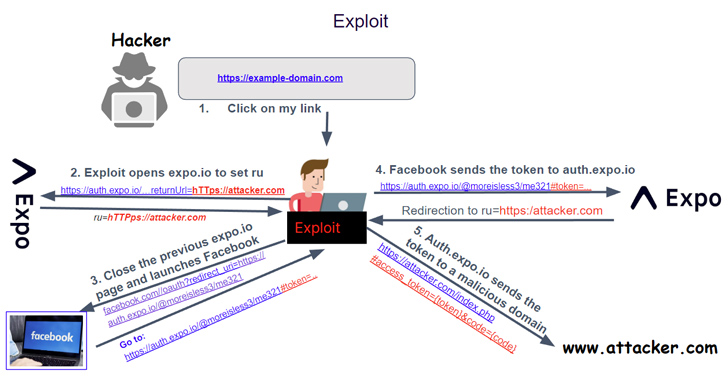
“The vulnerability would have permitted a probable attacker to trick a person into browsing a destructive link, logging in to a third-party auth service provider, and inadvertently revealing their 3rd-party auth credentials,” Expo’s James Ide reported.
“This was due to the fact auth.expo.io utilised to shop an app’s callback URL before the user explicitly verified they believe in the callback URL.”
Forthcoming WEBINARZero Believe in + Deception: Learn How to Outsmart Attackers!
Discover how Deception can detect state-of-the-art threats, quit lateral movement, and improve your Zero Trust system. Join our insightful webinar!
Save My Seat!
The disclosure follows the discovery of equivalent OAuth issues in Reserving.com (and its sister site Kayak.com) that could have been leveraged to acquire manage of a user’s account, gain entire visibility into their private or payment-card details, and conduct actions on the victim’s behalf.
The results also occur weeks after Swiss cybersecurity enterprise Sonar in-depth a route traversal and an SQL injection flaw in the Pimcore enterprise content material management method (CVE-2023-28438) that an adversary can abuse to run arbitrary PHP code on the server with the permissions of the webserver.
Sonar, back in March 2023, also disclosed an unauthenticated, saved cross-web site scripting vulnerability impacting LibreNMS versions 22.10. and prior that could be exploited to acquire remote code execution when Very simple Network Administration Protocol (SNMP) is enabled.
Discovered this posting exciting? Observe us on Twitter and LinkedIn to examine additional unique written content we post.
Some sections of this write-up are sourced from:
thehackernews.com

 Severe Flaw in Google Cloud’s Cloud SQL Service Exposed Confidential Data
Severe Flaw in Google Cloud’s Cloud SQL Service Exposed Confidential Data