Researchers have disclosed 3 security vulnerabilities influencing Pascom Cloud Phone Technique (CPS) that could be mixed to accomplish a full pre-authenticated remote code execution of affected programs.
Kerbit security researcher Daniel Eshetu claimed the shortcomings, when chained together, can lead to “an unauthenticated attacker attaining root on these devices.”
Pascom Cloud Phone Technique is an built-in collaboration and conversation alternative that permits businesses to host and established up private telephone networks throughout unique platforms as effectively as facilitate the monitoring, upkeep, and updates associated with the digital phone devices.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The established of a few flaws incorporates individuals stemming from an arbitrary route traversal in the web interface, a server-aspect ask for forgery (SSRF) owing to an outdated 3rd-party dependency (CVE-2019-18394), and a submit-authentication command injection working with a daemon service (“exd.pl”).
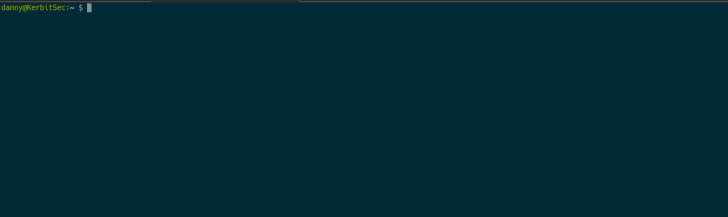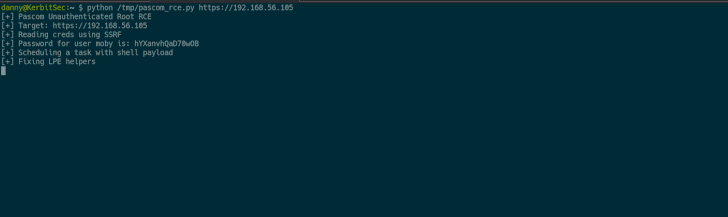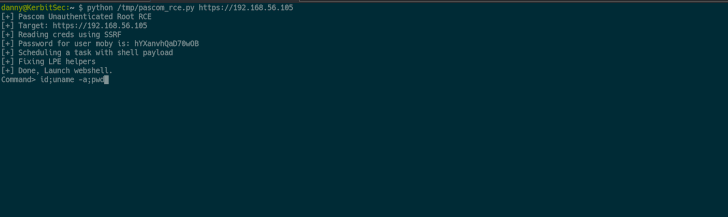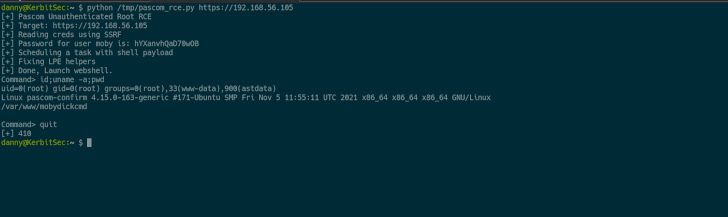
In other text, the vulnerabilities can be stringed in a chain-like trend to access non-uncovered endpoints by sending arbitrary GET requests to obtain the administrator password, and then use it to attain distant code execution working with the scheduled undertaking.
The exploit chain can be applied “to execute instructions as root,” Eshetu said, introducing, “this offers us whole control of the equipment and an simple way to escalate privileges.” The flaws ended up noted to Pascom on January 3, 2022, subsequent which patches have been produced.
Customers who are self-hosting CPS as opposed to on the cloud are encouraged to update to the most recent model (pascom Server 19.21) as before long as attainable to counter any possible threats.
Located this article appealing? Stick to THN on Fb, Twitter and LinkedIn to go through far more exceptional content material we write-up.
Some areas of this short article are sourced from:
thehackernews.com




 Critical Security Patches Issued by Microsoft, Adobe and Other Major Software Firms
Critical Security Patches Issued by Microsoft, Adobe and Other Major Software Firms