
IT assistance management application platform ConnectWise has launched Computer software patches for a critical security vulnerability in Get better and R1Smooth Server Backup Supervisor (SBM).
The issue, characterized as a “neutralization of Particular Components in Output Applied by a Downstream Element,” could be abused to consequence in the execution of remote code or disclosure of delicate info.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
ConnectWise’s advisory notes that the flaw influences Get well v2.9.7 and before, as nicely as R1Gentle SBM v6.16.3 and previously, are impacted by the critical flaw.
At its core, the issue is tied to an upstream authentication bypass vulnerability in the ZK open supply Ajax web application framework (CVE-2022-36537), which was in the beginning patched in May well 2022.
“Affected ConnectWise Recover SBMs have immediately been current to the hottest edition of Recover (v2.9.9),” the corporation reported, urging clients to improve to SBM v6.16.4 delivered on Oct 28, 2022.
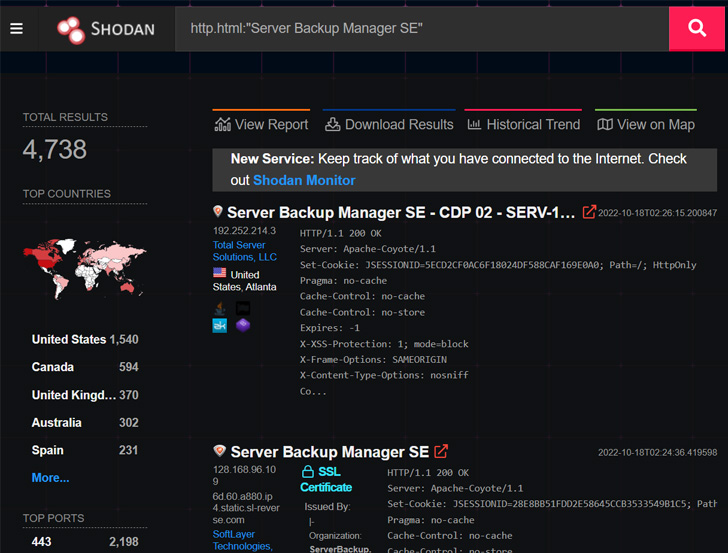
Cybersecurity agency Huntress claimed it determined “upwards of 5,000 exposed server manager backup cases,” potentially exposing businesses to provide chain threats.
Though there is no evidence of energetic exploitation of the vulnerability in the wild, a evidence-of-idea devised by Huntress researchers John Hammond and Caleb Stewart displays that it can be abused to bypass authentication, achieve remote code execution on SBM, and thrust LockBit 3. ransomware to all downstream endpoints.

“It is critical to note that the upstream ZK vulnerability not only has an effect on R1Smooth, but also any software using an unpatched version of the ZK framework,” the researchers stated.
“The accessibility an attacker can get by utilizing this authentication bypass vulnerability is certain to the application staying exploited, nevertheless there is critical possible for other applications to be afflicted in a identical way to R1Delicate Server Backup Manager.”
Uncovered this posting exciting? Comply with THN on Fb, Twitter and LinkedIn to study additional exclusive articles we submit.
Some elements of this posting are sourced from:
thehackernews.com


 NCSC Issued 34 Million Cyber Alerts in Past Year
NCSC Issued 34 Million Cyber Alerts in Past Year