A substantial-severity security flaw has been disclosed in the open source jsonwebtoken (JWT) library that, if correctly exploited, could lead to distant code execution on a concentrate on server.
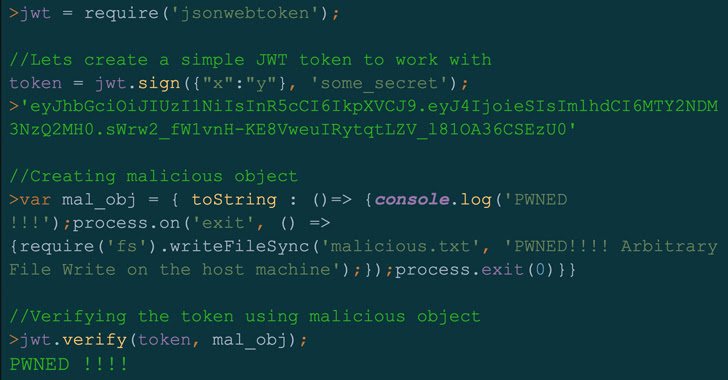
“By exploiting this vulnerability, attackers could achieve remote code execution (RCE) on a server verifying a maliciously crafted JSON web token (JWT) request,” Palo Alto Networks Unit 42 researcher Artur Oleyarsh reported in a Monday report.
Tracked as CVE-2022-23529 (CVSS score: 7.6), the issue impacts all versions of the library, like and beneath 8.5.1, and has been addressed in edition 9.. transported on December 21, 2022. The flaw was reported by the cybersecurity organization on July 13, 2022.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
jsonwebtoken, which is produced and preserved by Okta’s Auth0, is a JavaScript module that enables people to decode, confirm, and generate JSON web tokens as a indicates of securely transmitting info in between two parties for authorization and authentication. It has in excess of 10 million weekly downloads on the npm software package registry and is made use of by around 22,000 assignments.
Hence, the skill to operate malicious code on a server could break confidentiality and integrity assures, probably enabling a poor actor to overwrite arbitrary documents on the host and perform any motion of their deciding upon working with a poisoned magic formula critical.
“With that becoming said, in order to exploit the vulnerability explained in this write-up and command the secretOrPublicKey benefit, an attacker will need to have to exploit a flaw within just the top secret administration system,” Oleyarsh spelled out.
As open up supply software more and more emerges as a worthwhile original accessibility pathway for risk actors to phase provide chain attacks, it is essential that vulnerabilities in these types of instruments are proactively determined, mitigated, and patched by downstream consumers.
Producing matters worse is the reality that cybercriminals have turn out to be significantly more quickly at exploiting recently exposed flaws, considerably shrinking the time concerning a patch release and exploit availability. In accordance to Microsoft, it only will take 14 days on ordinary for an exploit to be detected in the wild right after public disclosure of a bug.
To battle this challenge of vulnerability discovery, Google, last thirty day period, introduced the release of OSV-Scanner, an open supply utility that aims to discover all transitive dependencies of a challenge and emphasize applicable shortcomings impacting it.
Located this article appealing? Adhere to us on Twitter and LinkedIn to study more distinctive content material we publish.
Some pieces of this report are sourced from:
thehackernews.com

 Freejacking Campaign By PurpleUrchin Bypasses Captchas
Freejacking Campaign By PurpleUrchin Bypasses Captchas