Security vulnerabilities have been disclosed in Netcomm and TP-Url routers, some of which could be weaponized to reach distant code execution.
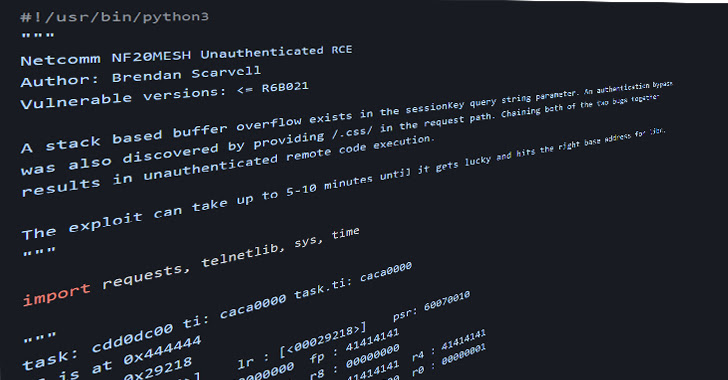
The flaws, tracked as CVE-2022-4873 and CVE-2022-4874, problem a case of stack-primarily based buffer overflow and authentication bypass and impression Netcomm router versions NF20MESH, NF20, and NL1902 jogging software program versions before than R6B035.
“The two vulnerabilities, when chained with each other, permit a remote, unauthenticated attacker to execute arbitrary code,” the CERT Coordination Heart (CERT/CC) claimed in an advisory published Tuesday.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
“The attacker can first attain unauthorized accessibility to influenced products, and then use these entry details to gain accessibility to other networks or compromise the availability, integrity, or confidentiality of information becoming transmitted from the inner network.”
Security researcher Brendan Scarvell has been credited with finding and reporting the issues in October 2022.
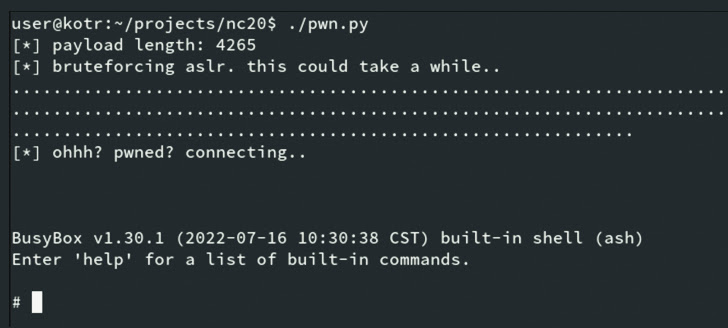
In a relevant development, CERT/CC also thorough two unpatched security vulnerabilities affecting TP-Backlink routers WR710N-V1-151022 and Archer-C5-V2-160201 that could direct to information and facts disclosure (CVE-2022-4499) and remote code execution (CVE-2022-4498).
CVE-2022-4499 is also a side-channel attack targeting a function employed to validate the entered credentials. “By measuring the response time of the vulnerable approach, every single byte of the username and password strings may possibly be less difficult to guess,” CERT/CC said.
Microsoft researcher James Hull has been acknowledged for disclosing the two bugs. The Hacker News has attained out to TP-Backlink for a comment, and we will update the story if we hear back again.
Found this post attention-grabbing? Abide by us on Twitter and LinkedIn to browse far more unique articles we article.
Some elements of this short article are sourced from:
thehackernews.com

 FinServ Firms See 81% Surge in Attacks Since Russia-Ukraine War
FinServ Firms See 81% Surge in Attacks Since Russia-Ukraine War