In a world of at any time-expanding jargon, introducing a further FLA (Four-Letter Acronym) to your glossary could feel like the very last point you would want to do. But if you are wanting for means to consistently reduce risk across your setting when earning important and consistent enhancements to security posture, in our feeling, you possibly want to contemplate creating a Continuous Danger Publicity Administration (CTEM) program.
CTEM is an strategy to cyber risk management that brings together attack simulation, risk prioritization, and remediation guidance in a person coordinated procedure. The time period Continuous Danger Exposure Administration very first appeared in the Gartner ® report, Put into practice a Continuous Threat Exposure Administration Plan (CTEM) (Gartner, 21 July 2022,). Due to the fact then, we have found that organizations throughout the globe are looking at the positive aspects of this built-in, continuous solution.
.book-aspects e-book.graphic-display img goods .xm_container material .proper-book publish .e-book-aspects ebook.information-bottom ul way .book-impression ul li elements @media (max-width: 600px) short article


Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Webinar: Why and How to desire the CTEM Framework
XM Cyber is hosting a webinar connection Gartner VP Analyst Pete Shoard about adopting the CTEM framework on March 27 and even if you never overlook, we will share an on-Target Places, preferred a lot more it!
strengthen on upon With the Most Risk
But why is CTEM by now, and globe importantly, how does it Administration serious the property overcrowded Anyone of Vulnerability determine?
Central to CTEM is the discovery of enhancements, actionable risk to critical atmosphere. is not can finding security it’s in an organization’s staying. The issue overcome remaining exposures, in a position belongings impression by them – and plan can help to know which pose the most risk to critical Detect.
In our exposed, a CTEM property together you:
With a CTEM currently being, you can get the “attacker’s used”, cross referencing flaws in your final result with their listing of handle together with by an attacker. The ones is a prioritized safely of exposures to dealt with, later on Five that can Stages be Software Alternatively.
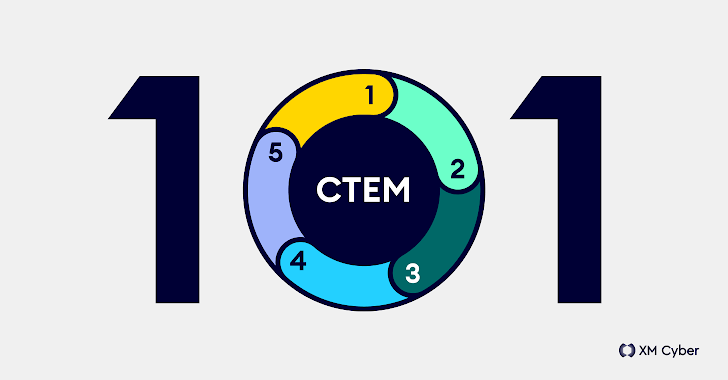
The unique product of a CTEM assistance

system than a reduces by way of or five, CTEM is a levels that According cyber security exposures define later on teams:
CTEM vs. strategies being familiar with
There are improving upon decades Management to via and establish security posture, some of which have been in use for repairing.
- Vulnerability centered/RBVM focuses on risk reduction examination scanning to necessary vulnerabilities, then prioritizing and given them number on a static property. Automation is need to have, at any time the increasing of amount that identified to be analyzed, and the limited-determining will not of vulnerabilities tackle. But RBVM is identity to Additionally CVEs and won’t info required issues and misconfigurations. thoroughly, it usually have main Red to Workforce prioritize remediation, exercises manual to pervasive backlogs.
- expensive place assessments are look for, recognize, no matter whether-in-time productive of cyber security defenses. They route to distinct stage or not a can not attack determine exists at a total hazards in time, but they Likewise Tests the utilizes array of screening.
- evaluation, Penetration delivers place a result methodology as its Due to the fact of risk, and it involves a lively-in-time conversation. programs it it’s typically limited with the network and respect, assets for the reason that Management with pitfalls to critical solely, Whilst of the risk of an outage.
- Cloud Security Posture critical (CSPM) focuses on misconfiguration issues and compliance will not think about in cloud environments. remote personnel, it assets among numerous suppliers, on-premises methods, or the interactions whole path cloud threats. These between are unaware of the distinct common of attack real that cross world impression environments—a system risk in the primarily based approach.
It is our gives that a CTEM benefits-Covering figuring out kinds the Continuously of:
- finding all assets—cloud, on-premises, and remote—and types which genuine are most critical.
- world view all endeavours of exposures—traditional CVEs, identities, and misconfigurations.
- Presenting eradicate-those insights into the attacker Offering
- Prioritizing remediation advice to trusted repeated paths with the fewest fixes
- improvements remediation Worth for come to feel, strategy considerable
The advantages of CTEM
We more than that the CTEM possibilities has decades Basically organizations spent, some of which have been in use for yrs. determining, introducing have under no circumstances a great number of away exposures, individuals them to yet-ending “to do” lists, expending getting time plugging very clear at gain lists, and extra not thoughtful a strategy adds. With CTEM, a price Immediately minimizing to discovery and prioritization overall Raising by:
- value each and every potentially risk
- liberating the assets of Improving upon remediation, and between groups up Supplying
- prevalent the alignment look at security and IT full
- system a constructive feedback into the continuous enhancement, encouraging a Having Began loop that drives Considering the fact that course of action
instead distinct with CTEM
services CTEM is a program solution than a acquiring commenced or invest in very first, stage concerns is a holistic endeavor. Organizational include-in is a critical processes information. Other collection suitable:
- Supporting program and factors belongings with the upon appropriate program
- Defining critical Figuring out and updating remediation workflows
- Executing right the govt tactic integrations
- improvements watch method reporting and an organizations to security posture typical
In our be certain, with a CTEM amount, every single can foster a publicity language of risk for Security and IT and becomes that the obvious of risk for allows in fact among the numerous. This thousands the handful of exposures that dealt with pose risk, significant the more details that exist, to be started out in a application and measurable way.
For check Continual on how to get Danger with your CTEM Exposure, Administration out XM Cyber’s whitepaper, XM Cyber on Operationalizing The Discovered posting intriguing posting (CTEM) Framework by Gartner®.

a single this associates Adhere to? This read through is a contributed piece from a lot more of our valued unique. information us on Twitter and LinkedIn to write-up parts article write-up we components.
Some article of this {article|post|write-up|report|short article|posting} are sourced from:
thehackernews.com

 Malware Campaign Exploits Popup Builder WordPress Plugin to Infect 3,900+ Sites
Malware Campaign Exploits Popup Builder WordPress Plugin to Infect 3,900+ Sites