A previously undocumented cyber espionage-focused threat actor named LilacSquid has been linked to targeted attacks spanning various sectors in the United States (U.S.), Europe, and Asia as part of a data theft campaign since at least 2021.
“The campaign is geared toward establishing long-term access to compromised victim organizations to enable LilacSquid to siphon data of interest to attacker-controlled servers,” Cisco Talos researcher Asheer Malhotra said in a new technical report published today.
Targets include information technology organizations building software for the research and industrial sectors in the U.S, energy companies in Europe, and the pharmaceutical sector in Asia, indicating a broad victimology footprint.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
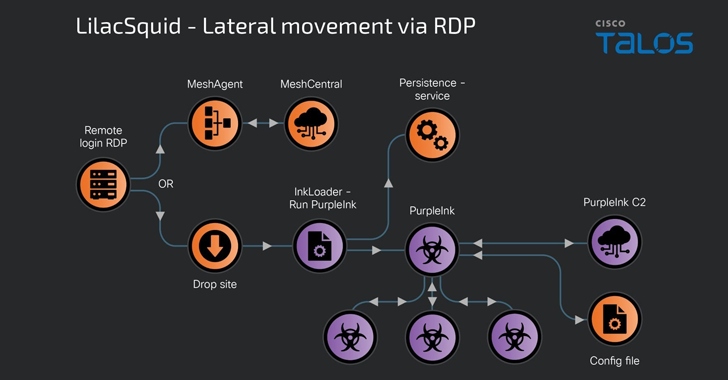
Attack chains are known to exploit either publicly known vulnerabilities to breach internet-facing application servers or make use of compromised remote desktop protocol (RDP) credentials to deliver a mix of open-source tools and custom malware.

The campaign’s most distinctive feature is the use of an open-source remote management tool called MeshAgent, which serves as a conduit to deliver a bespoke version of Quasar RAT codenamed PurpleInk.
Alternate infection procedures leveraging compromised RDP credentials exhibit a slightly different modus operandi, wherein the threat actors choose to either deploy MeshAgent or drop a .NET-based loader dubbed InkLoader to drop PurpleInk.

“A successful login via RDP leads to the download of InkLoader and PurpleInk, copying these artifacts into desired directories on disk and the subsequent registration of InkLoader as a service that is then started to deploy InkLoader and, in turn, PurpleInk,” Malhotra said.
PurpleInk, actively maintained by LilacSquid since 2021, is both heavily obfuscated and versatile, allowing it to run new applications, perform file operations, get system information, enumerate directories and processes, launch a remote shell, and connect to a specific remote address provided by a command-and-control (C2) server.
Talos said it identified another custom tool called InkBox that’s said to have been used by the adversary to deploy PurpleInk prior to InkLoader.

The incorporation of MeshAgent as part of their post-compromise playbooks is noteworthy in part due to the fact that it’s a tactic previously adopted by a North Korean threat actor named Andariel, a sub-cluster within the infamous Lazarus Group, in attacks targeting South Korean companies.
Another overlap concerns the use of tunneling tools to maintain secondary access, with LilacSquid deploying Secure Socket Funneling (SSF) to create a communication channel to its infrastructure.
“Multiple tactics, techniques, tools, and procedures (TTPs) utilized in this campaign bear some overlap with North Korean APT groups, such as Andariel and its parent umbrella group, Lazarus,” Malhotra said.
Found this article interesting? Follow us on Twitter and LinkedIn to read more exclusive content we post.
Some parts of this article are sourced from:
thehackernews.com

 Protecting Your Saas Stack from Cyber Threats – What Works and What Doesn'tAdaptive ShieldSaaS Security / Identity SecurityRead the SaaS survey to learn how enterprises are better positioned to prevent SaaS breaches and threats.
Protecting Your Saas Stack from Cyber Threats – What Works and What Doesn'tAdaptive ShieldSaaS Security / Identity SecurityRead the SaaS survey to learn how enterprises are better positioned to prevent SaaS breaches and threats.