A financially inspired danger actor has been outed as an first accessibility broker (IAB) that sells obtain to compromised corporations for other adversaries to carry out observe-on attacks these types of as ransomware.
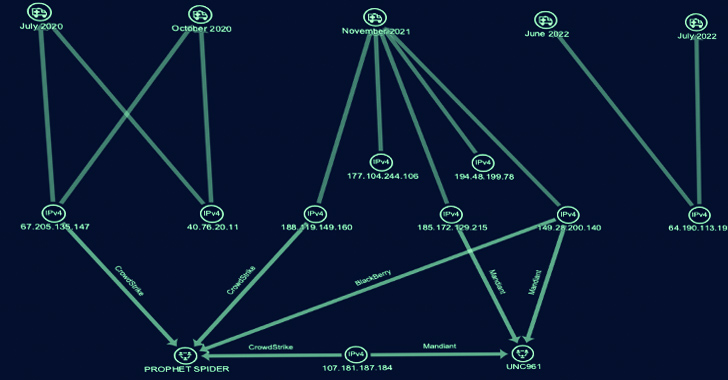
SecureWorks Counter Menace Unit (CTU) has dubbed the e-crime team Gold Melody, which is also recognised by the names Prophet Spider (CrowdStrike) and UNC961 (Mandiant).
“This economically inspired team has been lively because at minimum 2017, compromising corporations by exploiting vulnerabilities in unpatched internet-dealing with servers,” the cybersecurity company claimed.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
“The victimology indicates opportunistic attacks for economical obtain relatively than a specific marketing campaign conducted by a state-sponsored danger group for espionage, destruction, or disruption.”

Gold Melody has been previously connected to attacks exploiting security flaws in JBoss Messaging (CVE-2017-7504), Citrix ADC (CVE-2019-19781), Oracle WebLogic (CVE-2020-14750 and CVE-2020-14882), GitLab (CVE-2021-22205), Citrix ShareFile Storage Zones Controller (CVE-2021-22941), Atlassian Confluence (CVE-2021-26084), ForgeRock AM (CVE-2021-35464), and Apache Log4j (CVE-2021-44228) servers.
The cybercrime group has been noticed increasing its victimology footprint to strike retail, wellbeing care, power, financial transactions, and large-tech organizations in North America, Northern Europe, and Western Asia as of mid-2020.
Mandiant, in an analysis released in March 2023, said that “in a number of scenarios, UNC961 intrusion exercise has preceded the deployment of Maze and Egregor ransomware from distinctive abide by-on actors.”
It even more explained the group as “resourceful in their opportunistic angle to original entry functions” and observed it “employs a price tag-efficient approach to achieve first access by exploiting recently disclosed vulnerabilities applying publicly obtainable exploit code.”
Apart from relying on a assorted arsenal comprising web shells, designed-in working procedure software package, and publicly readily available utilities, it is recognised to hire proprietary remote entry trojans (RATs) and tunneling equipment these as GOTROJ (aka MUTEPUT), BARNWORK, HOLEDOOR, DARKDOOR, AUDITUNNEL, HOLEPUNCH, LIGHTBUNNY, and HOLERUN to execute arbitrary commands, get system information and facts, and set up a reverse tunnel with a tough-coded IP handle.
Secureworks, which connected Gold Melody to five intrusions amongst July 2020 and July 2022, reported these attacks entailed the abuse of a unique set of flaws, which include individuals impacting Oracle E-Company Suite (CVE-2016-0545), Apache Struts (CVE-2017-5638), Sitecore XP (CVE-2021-42237), and Flexera FlexNet (CVE-2021-4104) to acquire initial accessibility.
Future WEBINARLevel-Up SaaS Security: A Thorough Tutorial to ITDR and SSPM
Remain ahead with actionable insights on how ITDR identifies and mitigates threats. Understand about the indispensable purpose of SSPM in guaranteeing your id continues to be unbreachable.
Supercharge Your Abilities
A thriving foothold is succeeded by the deployment of web shells for persistence, adopted by developing directories in the compromised host to phase the resources made use of in the an infection chain.
“Gold Melody conducts a appreciable amount of scanning to recognize a victim’s ecosystem,” the company explained. “Scanning commences shortly following attaining entry but is repeated and ongoing all through the intrusion.”
The reconnaissance period paves the way for credential harvesting, lateral motion, and knowledge exfiltration. That claimed, all five attacks in the end proved to be unsuccessful.
“Gold Melody functions as a financially enthusiastic IAB, marketing entry to other menace actors,” the firm concluded. “The potential buyers subsequently monetize the entry, possible as a result of extortion by way of ransomware deployment.”
“Its reliance on exploiting vulnerabilities in unpatched internet-experiencing servers for access reinforces the great importance of robust patch management.”
Discovered this posting appealing? Adhere to us on Twitter and LinkedIn to study more exceptional information we post.
Some parts of this write-up are sourced from:
thehackernews.com

 Ukrainian Hacker Suspected to be Behind “Free Download Manager” Malware Attack
Ukrainian Hacker Suspected to be Behind “Free Download Manager” Malware Attack