Cybersecurity researchers have warned of a new malicious Python package that has been found in the Python Offer Index (PyPI) repository to aid cryptocurrency theft as part of a broader marketing campaign.
The package in question is pytoileur, which has been downloaded 316 times as of crafting. Apparently, the bundle creator, who goes by the title PhilipsPY, has uploaded a new edition of the bundle (1..2) with equivalent functionality soon after a prior version (1..1) was yanked by PyPI maintainers on May possibly 28, 2024.
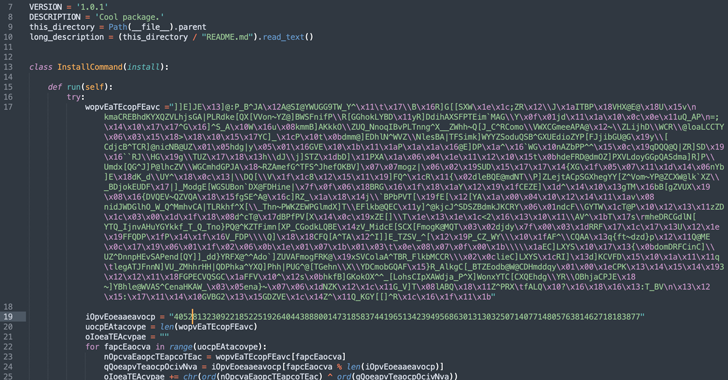
In accordance to an investigation launched by Sonatype, the destructive code is embedded in the package’s set up.py script, making it possible for it to execute a Foundation64-encoded payload which is dependable for retrieving a Windows binary from an exterior server.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

“The retrieved binary, ‘Runtime.exe,’ is then operate by leveraging Windows PowerShell and VBScript instructions on the technique,” security researcher Ax Sharma stated.
Once set up, the binary establishes persistence and drops more payloads, like spy ware and a stealer malware able of collecting knowledge from web browsers and cryptocurrency services.
Sonatype explained it also discovered a recently created StackOverflow account identified as “EstAYA G” responding to users’ queries on the question-and-answer system, directing them to set up the rogue pytoileur bundle as a meant option to their issues.
“When definitive attribution is tough when examining pseudonymous person accounts on internet platforms with no obtain to logs, the the latest age of both equally of these consumer accounts and their sole purpose of publishing and marketing the destructive Python bundle provides us a superior indicator that these are joined to the exact same threat actor(s) behind this campaign,” Sharma instructed The Hacker News.

The advancement marks a new escalation in that it abuses a credible platform as a propagation vector for malware.
“The unprecedented open abuse of this sort of a credible platform, using it as a breeding floor for malicious campaigns, is a big warning sign for builders globally,” Sonatype more mentioned in a statement shared with The Hacker Information.

“StackOverflow’s compromise is specially relating to supplied the significant quantity of beginner builders it has, who are nonetheless finding out, inquiring issues, and might fall for destructive information.”
A closer assessment of the package metadata and its authorship history has disclosed overlaps with a prior campaign involving bogus Python packages these types of as Pystob and Pywool, which was disclosed by Checkmarx in November 2023.
The results are one more instance of why open-supply ecosystems proceed to be a magnet for risk actors wanting to compromise numerous targets all at as soon as with data stealers like Bladeroid and other malware by signifies of what is actually known as a supply chain attack.
Uncovered this short article intriguing? Stick to us on Twitter and LinkedIn to read through a lot more exclusive content we publish.
Some elements of this write-up are sourced from:
thehackernews.com

 Check Point Warns of Zero-Day Attacks on its VPN Gateway Products
Check Point Warns of Zero-Day Attacks on its VPN Gateway Products