An lively fiscally determined campaign is targeting susceptible SSH servers to covertly ensnare them into a proxy network.
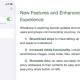
“This is an active campaign in which the attacker leverages SSH for distant access, jogging malicious scripts that stealthily enlist victim servers into a peer-to-peer (P2P) proxy network, this sort of as Peer2Income or Honeygain,” Akamai researcher Allen West stated in a Thursday report.
Unlike cryptojacking, in which a compromised system’s means are applied to illicitly mine cryptocurrency, proxyjacking delivers the capacity for threat actors to leverage the victim’s unused bandwidth to covertly run distinctive products and services as a P2P node.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
This features two-fold benefits: It not only allows the attacker to monetize the further bandwidth with a drastically minimized source load that would be important to have out cryptojacking, it also lowers the likelihood of discovery.

“It is a stealthier alternate to cryptojacking and has serious implications that can enhance the head aches that proxied Layer 7 attacks now provide,” West claimed.
To make matters worse, the anonymity furnished by proxyware providers can be a double-edged sword in that they could be abused by destructive actors to obfuscate the resource of their attacks by routing targeted traffic through intermediary nodes.
Akamai, which identified the most current marketing campaign on June 8, 2023, stated the activity is developed to breach prone SSH servers and deploy an obfuscated Bash script that, in flip, is equipped to fetch important dependencies from a compromised web server, which include the curl command-line instrument by camouflaging it as a CSS file (“csdark.css”).
The stealthy script further more actively queries for and terminates competing situations functioning bandwidth-sharing solutions, prior to launching Docker services that share the victim’s bandwidth for revenue.
A further more evaluation of the web server has uncovered that it is also staying utilised to host a cryptocurrency miner, suggesting that the menace actors are dabbling in both of those cryptojacking and proxyjacking attacks.

Whilst proxyware is not inherently nefarious, Akamai famous that “some of these firms do not effectively confirm the sourcing of the IPs in the network, and even often counsel that people today install the computer software on their work desktops.”
But such functions transcend into the realm of cybercrime when the apps are set up without having the users’ know-how or consent, thus permitting the risk actor to handle quite a few techniques and generate illegitimate profits.
“Old strategies stay helpful, specially when paired with new outcomes,” West explained. “Regular security practices remain an productive prevention mechanism, which include powerful passwords, patch administration, and meticulous logging.”
Found this write-up intriguing? Follow us on Twitter and LinkedIn to read through more exceptional articles we submit.
Some components of this report are sourced from:
thehackernews.com

 MITRE Unveils Top 25 Most Dangerous Software Weaknesses of 2023: Are You at Risk?
MITRE Unveils Top 25 Most Dangerous Software Weaknesses of 2023: Are You at Risk?