Distant access trojans these kinds of as StrRAT and Ratty are currently being distributed as a mixture of polyglot and destructive Java archive (JAR) files, when again highlighting how danger actors are consistently acquiring new strategies to fly underneath the radar.
“Attackers now use the polyglot technique to confuse security options that don’t thoroughly validate the JAR file structure,” Deep Instinct security researcher Simon Kenin mentioned in a report.
Polyglot information are information that merge syntax from two or extra various formats in a way these that just about every format can be parsed with no raising any mistake.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
One these kinds of 2022 marketing campaign spotted by the cybersecurity business is the use of JAR and MSI formats – i.e., a file which is valid both of those as a JAR and an MSI installer – to deploy the StrRAT payload. This also usually means that the file can be executed by both Windows and Java Runtime Setting (JRE) based mostly on how it is really interpreted.
One more instance will involve the use of Taxi and JAR polyglots to deliver both equally Ratty and StrRAT. The artifacts are propagated making use of URL shortening solutions these as cutt.ly and rebrand.ly, with some of them hosted on Discord.
“What is actually distinctive about ZIP information is that they’re determined by the existence of an finish of central listing report which is positioned at the stop of the archive,” Kenin defined. “This signifies that any ‘junk’ we append in the commencing of the file will be overlooked and the archive is even now valid.”
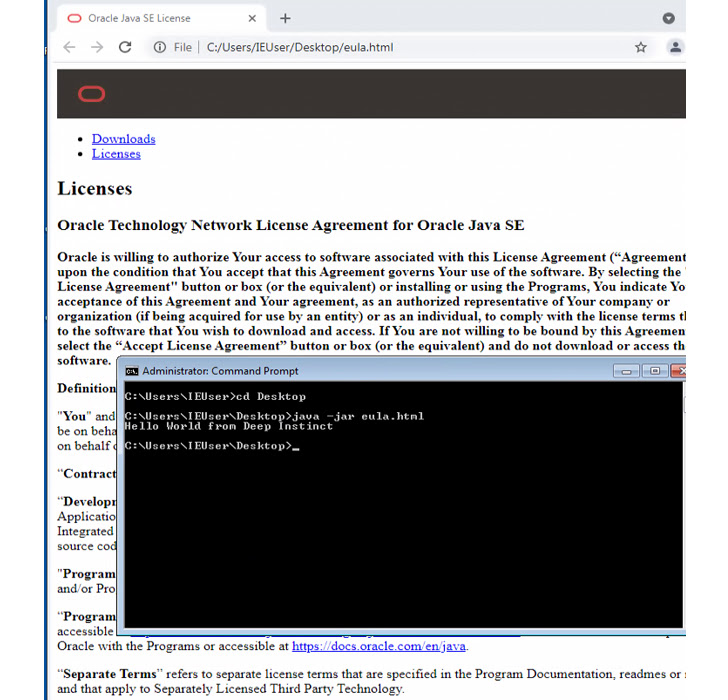
The deficiency of enough validation of the JAR files results in a situation the place malicious appended written content can bypass security software program and keep undetected right until they are executed on the compromised hosts.
This is not the very first time these kinds of malware-laced polyglots have been detected in the wild. In November 2022, Berlin-dependent DCSO CyTec unearthed an data stealer dubbed StrelaStealer that’s distribute as a DLL/HTML polyglot.
“The correct detection for JAR data files must be equally static and dynamic,” Kenin said. “It is inefficient to scan every file for the presence of an end of central listing history at the conclusion of the file.”
“Defenders should really check the two ‘java’ and ‘javaw’ procedures. If these types of a approach has ‘-jar’ as an argument the filename passed as an argument need to be handled as a JAR file regardless of the file extension or the output of the Linux ‘file’ command.”
Observed this short article attention-grabbing? Abide by us on Twitter and LinkedIn to read through much more exclusive written content we put up.
Some parts of this write-up are sourced from:
thehackernews.com


 Royal Mail’s Attackers Linked to Russia-Backed LockBit
Royal Mail’s Attackers Linked to Russia-Backed LockBit