The threat actor recognized as Dark Pink has been joined to 5 new attacks aimed at various entities in Belgium, Brunei, Indonesia, Thailand, and Vietnam between February 2022 and April 2023.
This consists of instructional entities, federal government businesses, military services bodies, and non-gain corporations, indicating the adversarial crew’s ongoing concentration on large-price targets.
Dark Pink, also referred to as Saaiwc Group, is an superior persistent menace (APT) actor believed to be of Asia-Pacific origin, with attacks focusing on entities largely situated in East Asia and, to a lesser extent, in Europe.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
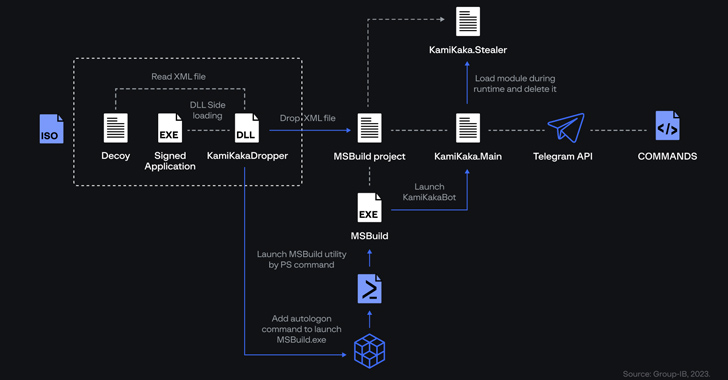
The team employs a established of tailor made malware instruments this kind of as TelePowerBot and KamiKakaBot that deliver numerous features to exfiltrate sensitive details from compromised hosts.
“The group takes advantage of a array of refined tailor made resources, deploys numerous destroy chains relying on spear-phishing email messages,” Group-IB security researcher Andrey Polovinkin reported in a complex report shared with The Hacker Information.
“After the attackers achieve access to a target’s network, they use innovative persistence mechanisms to continue to be undetected and manage management above the compromised process.”
The conclusions also illustrate some essential modifications to the Dark Pink attack sequence to impede evaluation as properly as accommodate enhancements to KamiKakaBot, which executes commands from a threat actor-managed Telegram channel by means of a Telegram bot.
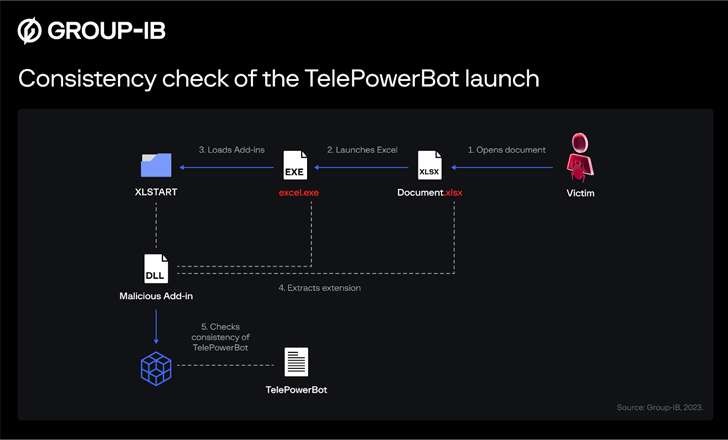
The latest edition, notably, splits its operation into two distinctive sections: One for controlling products and the other for harvesting useful data.
The Singapore-headquartered corporation said it also determined a new GitHub account associated with the account that has PowerShell scripts, ZIP archives, and personalized malware which ended up fully commited amongst January 9, 2023, and April 11, 2023.
Aside from utilizing Telegram for command-and-control, Dark Pink has been observed exfiltrating stolen data above HTTP utilizing a assistance called webhook[.]site. A different noteworthy part is the use of an Microsoft Excel increase-in to be certain the persistence of TelePowerBot inside of the contaminated host.
Approaching WEBINAR Zero Belief + Deception: Learn How to Outsmart Attackers!
Find out how Deception can detect sophisticated threats, quit lateral movement, and improve your Zero Trust strategy. Sign up for our insightful webinar!
Save My Seat!.advert-button,.ad-label,.ad-label:afterdisplay:inline-block.advertisement_two_webinarmargin:20px 10px 30px 0background:#f9fbffcolor:#160755padding: 5%border:2px strong #d9deffborder-radius:10pxtext-align:leftbox-shadow:10px 10px #e2ebff-webkit-border-prime-still left-radius:25px-moz-border-radius-topleft:25px-webkit-border-bottom-correct-radius:25px-moz-border-radius-bottomright:25px.advertisement-labelfont-sizing:13pxmargin:20px 0font-bodyweight:600letter-spacing:.6pxcolor:#596cec.advertisement-label:soon afterwidth:50pxheight:6pxcontent:”border-prime:2px reliable #d9deffmargin: 8px.advertisement-titlefont-size:21pxpadding:10px 0font-weight:900textual content-align:leftline-peak:33px.advert-descriptiontextual content-align:leftfont-sizing:15.6pxline-height:26pxmargin:5px !importantcolor:#4e6a8d.advert-buttonpadding:6px 12pxborder-radius:5pxbackground-colour:#4469f5font-measurement:15pxcolor:#fff!importantborder:0line-height:inherittext-decoration:none!importantcursor:pointermargin:15px 20pxfloat:leftfont-weight:500letter-spacing:.2px
“With webhook[.]internet site, it is doable to established up non permanent endpoints in purchase to seize and look at incoming HTTP requests,” Polovinkin famous. “The danger actor made short term endpoints and sent delicate data stolen from victims.”
Dark Pink, its espionage motives notwithstanding, stays shrouded in mystery. That explained, it truly is suspected that the hacking crew’s victimology footprint could be broader than previously assumed.
The simple fact that the adversary has been connected to only 13 attacks (counting the five new victims) since mid-2021 implies an attempt to maintain a reduced profile for stealthiness. It’s also a indication of the menace actor thoroughly deciding upon their targets and keeping the selection of attacks at a minimal to decrease the probability of exposure.
“The simple fact that two attacks ended up executed in 2023 suggests that Dark Pink stays lively and poses an ongoing risk to organizations,” Polovinkin reported. “Evidence reveals that the cybercriminals guiding these attacks retain updating their present equipment in get to stay undetected.”
Uncovered this report appealing? Stick to us on Twitter and LinkedIn to study a lot more special content material we article.
Some components of this report are sourced from:
thehackernews.com

 Dark Pink APT Group Expands Tooling and Targets
Dark Pink APT Group Expands Tooling and Targets