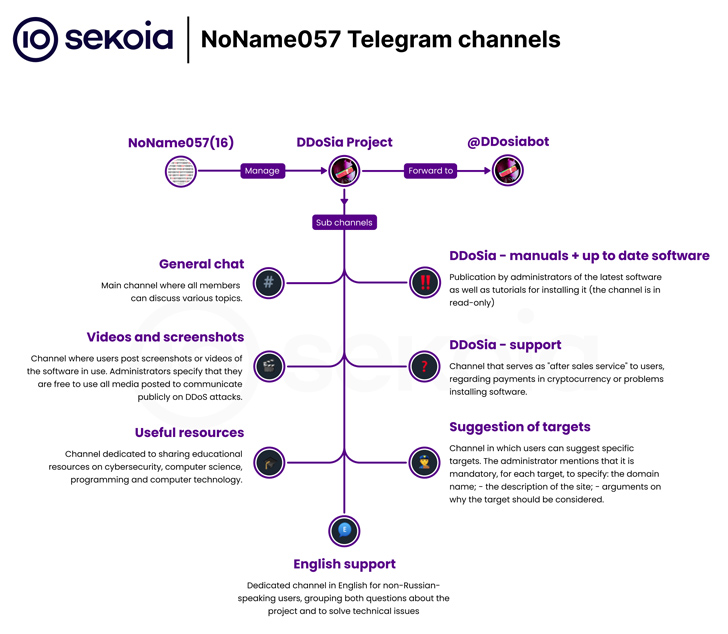
The danger actors guiding the DDoSia attack instrument have come up with a new model that incorporates a new mechanism to retrieve the list of targets to be bombarded with junk HTTP requests in an endeavor to deliver them down.
The updated variant, written in Golang, “implements an extra security system to conceal the record of targets, which is transmitted from the [command-and-control] to the people,” cybersecurity company Sekoia claimed in a technological publish-up.
DDoSia is attributed to a pro-Russian hacker team known as NoName(057)16. Released in 2022 and a successor of the Bobik botnet, the attack software is built for staging dispersed denial-of-provider (DDoS) attacks versus targets mostly located in Europe as perfectly as Australia, Canada, and Japan.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Lithuania, Ukraine, Poland, Italy, Czechia, Denmark, Latvia, France, the U.K., and Switzerland have emerged as the most focused nations around the world about a time period ranging from May possibly 8 to June 26, 2023. A complete of 486 distinctive internet sites have been impacted.
Python and Go-based mostly implementations of DDoSia have been unearthed to day, making it a cross-system plan capable of getting used throughout Windows, Linux, and macOS systems.
“DDoSia is a multi-threaded software that conducts denial-of-assistance attacks against goal websites by continuously issuing network requests,” SentinelOne stated in an assessment published in January 2023. “DDoSia issues requests as instructed by a configuration file that the malware receives from a C2 server when started.”
DDoSia is dispersed as a result of a fully-automated system on Telegram that makes it possible for people to register for the crowdsourced initiative in trade for a cryptocurrency payment and a ZIP archive that contains the attack toolkit.
What is noteworthy about the new model is the use of encryption to mask the record of targets to be attacked, indicating that the software is becoming actively maintained by the operators.
“NoName057(16) is making attempts to make their malware compatible with various running techniques, nearly unquestionably reflecting their intent to make their malware available to a massive selection of users, ensuing in the targeting of a broader set of victims,” Sekoia claimed.
The enhancement comes as the U.S. Cybersecurity and Infrastructure Security Company (CISA) warned of qualified denial-of-provider (DoS) and DDoS attacks from multiple corporations in various sectors.
“These attacks can price an business time and revenue and may possibly impose reputational expenditures even though means and expert services are inaccessible,” the agency stated in a bulletin.
Whilst CISA did not supply any added details, the warning overlaps with promises by Anonymous Sudan on its Telegram channel that it experienced taken down the internet websites of the Section of Commerce, Social Security Administration (SSA), and the Treasury Department’s Digital Federal Tax Payment Technique (EFTPS).
Anonymous Sudan attracted attention previous month for carrying Layer 7 DDoS attacks from several Microsoft providers, like OneDrive, Outlook, and Azure web portals. The tech large is tracking the cluster beneath the name Storm-1359.
The hacking crew has asserted it really is conducting cyber strikes out of Africa on behalf of oppressed Muslims across the entire world. But cybersecurity scientists believe that it to be a pro-Kremlin operation with no ties to Sudan and a member of the KillNet hacktivist collective.
In an analysis launched on June 19, 2023, Australian cybersecurity vendor CyberCX characterised the entity as a “smokescreen for Russian pursuits.” The company’s web site has given that turn out to be inaccessible, greeting visitors with a “403 Forbidden” message. The danger actor claimed duty for the cyber attack.
“The motive for the attack: cease spreading rumors about us, and you must convey to the fact and halt the investigations that we contact the investigations of a dog,” Nameless Sudan explained in a concept posted on June 22, 2023.
Nameless Sudan, in a Bloomberg report very last week, further denied it was related to Russia but acknowledged they share equivalent passions, and that it goes immediately after “anything that is hostile to Islam.”
CISA’s latest advisory has also not absent unnoticed, for the group posted a reaction on June 30, 2023, stating: “A smaller Sudanese group with constrained capabilities forced ‘the most highly effective government’ in the planet to publish content and tweets about our attacks.”
Identified this article exciting? Follow us on Twitter and LinkedIn to read through extra exceptional information we submit.
Some elements of this short article are sourced from:
thehackernews.com

 Mexico-Based Hacker Targets Global Banks with Android Malware
Mexico-Based Hacker Targets Global Banks with Android Malware