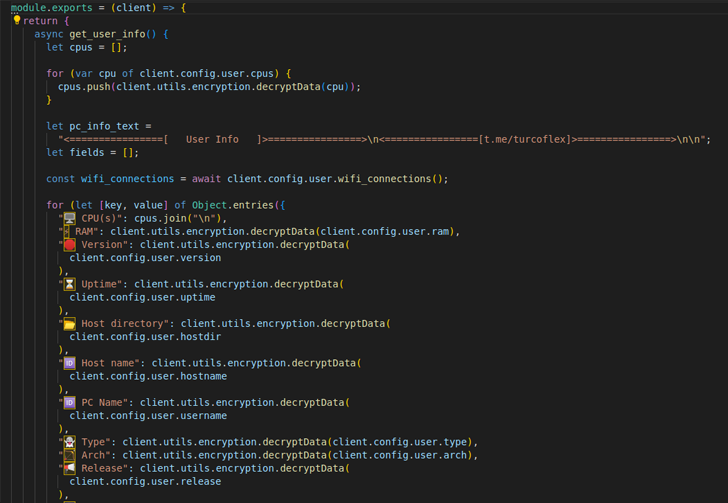
Two malicious packages discovered in the npm deal repository have been identified to conceal an open up supply data stealer malware termed TurkoRat.
The deals – named nodejs-encrypt-agent and nodejs-cookie-proxy-agent – have been collectively downloaded roughly 1,200 moments and had been readily available for extra than two months ahead of they have been determined and taken down.
ReversingLabs, which broke down the facts of the marketing campaign, explained TurkoRat as an facts stealer able of harvesting delicate data this sort of as login credentials, website cookies, and facts from cryptocurrency wallets.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
While nodejs-encrypt-agent came fitted with the malware inside of, nodejs-cookie-proxy-agent was discovered to disguise the trojan as a dependency less than the title axios-proxy.
nodejs-encrypt-agent was also engineered to masquerade as an additional reputable npm module regarded as agent-base, which has been downloaded in excess of 25 million instances to date.
The list of the rogue offers and their affiliated variations are shown under –
- nodejs-encrypt-agent (versions 6..2, 6..3, 6..4, and 6..5)
- nodejs-cookie-proxy-agent (versions 1.1., 1.2., 1.2.1, 1.2.2, 1.2.3, and 1.2.4), and
- axios-proxy (variations 1.7.3, 1.7.4, 1.7.7, 1.7.9, 1.8.9, and 1.9.9)
“TurkoRat is just a single of quite a few open supply malware families that are presented for ‘testing’ applications, but can conveniently be downloaded and modified for malicious use, as nicely,” Lucija Valentić, menace researcher at ReversingLabs, explained.
The findings as soon as once again underscore the ongoing risk of danger actors orchestrating source chain attacks by means of open up resource packages and baiting developers into downloading potentially untrusted code.
“Improvement businesses need to have to scrutinize the functions and behaviors of the open up source, 3rd-party and commercial code they are relying on in order to observe dependencies and detect potential destructive payloads in them,” Valentić explained.
The rising use of destructive npm packages fits in with a broader pattern of surging attacker desire in open up resource computer software offer chains, not to mention highlighting the escalating sophistication of danger actors.
Even more worryingly, scientists from Checkmarx revealed new investigation this thirty day period that showed how danger actors could impersonate authentic npm deals by “utilizing lowercase letters to mimic uppercase letters in the initial deal names” (e.g., memoryStorageDriver vs memorystoragedriver).
“This destructive package deal impersonation usually takes the conventional ‘Typosquatting,’ attack approach to a new level, the place attackers sign-up bundle names that consist of the specific similar letters as the legit ones, with the only variation being capitalization,” scientists Teach Zornstein and Yehuda Gelb said.
“This can make it even more durable for consumers to detect the deception considering the fact that it can be easy to forget about the refined differences in capitalization.”
The provide chain security organization found that 1,900 out of 3,815 packages with funds letters in their titles could have been at risk of copycat attacks if not for a resolve pushed by the npm maintainers to handle the challenge, which, Checkmarx reported, has existed due to the fact December 2017.
The disclosure also follows yet another advisory from Examine Issue, which recognized a few destructive extensions hosted on the VS Code extensions marketplace. They have been purged as of Might 14, 2023.
The add-ons, named prettiest java, Darcula Dark, and python-vscode, were cumulatively downloaded about 46,000 occasions and incorporated functions that permitted the menace actors to steal qualifications, program information and facts, and establish a remote shell on the victim’s equipment.
Future WEBINARZero Have faith in + Deception: Study How to Outsmart Attackers!
Find how Deception can detect superior threats, cease lateral motion, and enhance your Zero Rely on system. Sign up for our insightful webinar!
Preserve My Seat!
It really is not just npm and VS Code market, for a identical set of rogue libraries have been unearthed from the Python Bundle Index (PyPI) computer software repository as perfectly.
Some of these deals have been developed to distribute a cryptocurrency clipper malware dubbed KEKW, even though other typosquatted variations of the well known flask framework incorporated backdoor capabilities to obtain commands from a distant server.
Yet another Python deal uncovered by Israeli company Phylum this week was identified to incorporate a destructive dependency that harbored an encrypted payload to grab Discord tokens and steal clipboard material in get to hijack cryptocurrency transactions.
The package, referred to as chatgpt-api by its developer Patrick Pogoda and obtainable by GitHub, sent on the performance it marketed (i.e., interacting with OpenAI’s ChatGPT instrument) in an endeavor to finish the ruse. The repository is continue to offered as of composing.
“For now this actor seems to be preying on the the latest explosive rise in popularity of [Large Language Models] with this chatgpt-api package deal,” Phylum reported, introducing the menace actor has an automatic mechanism to add new iterations of the malicious dependency each individual time it is really taken down and “sustain a persistent an infection.”
Observed this write-up intriguing? Comply with us on Twitter and LinkedIn to go through additional unique material we put up.
Some pieces of this report are sourced from:
thehackernews.com

 NCSC: It’s Time for CISOs to Prioritize Accessibility
NCSC: It’s Time for CISOs to Prioritize Accessibility