The Laptop Unexpected emergency Response Workforce of Ukraine (CERT-UA) has warned that more than 2,000 pcs in the state have been infected by a pressure of malware identified as DirtyMoe.
The company attributed the marketing campaign to a menace actor it phone calls UAC-0027.
DirtyMoe, energetic considering that at the very least 2016, is able of carrying out cryptojacking and distributed denial-of-services (DDoS) attacks. In March 2022, cybersecurity firm Avast disclosed the malware’s potential to propagate in a worm-like vogue by getting gain of known security flaws.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The DDoS botnet is recognized to be sent by implies of an additional malware referred to as Purple Fox or through bogus MSI installer offers for preferred program these types of as Telegram. Purple Fox is also geared up with a rootkit that permits the danger actors to cover the malware on the machine and make it difficult to detect and remove.

The exact original entry vector employed in the campaign concentrating on Ukraine is at this time unfamiliar. CERT-UA is recommending that businesses keep their devices up-to-date, enforce network segmentation, and keep track of network website traffic for any anomalous activity.
The disclosure comes as Securonix in-depth an ongoing phishing marketing campaign known as Steady#URSA concentrating on Ukrainian navy staff with the intention of delivering a bespoke PowerShell backdoor dubbed Refined-PAWS.
“The exploitation chain is reasonably easy: it entails the target executing a malicious shortcut (.lnk) file which loads and executes a new PowerShell backdoor payload code (discovered inside an additional file contained inside of the identical archive),” security scientists Den Iuzvyk, Tim Peck, and Oleg Kolesnikov reported.
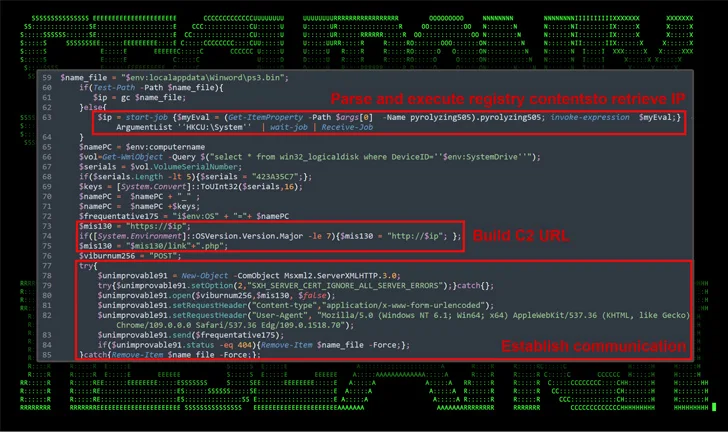
The attack is explained to be associated to a risk actor identified as Shuckworm, which is also recognised as Aqua Blizzard (formerly Actinium), Armageddon, Gamaredon, Iron Tilden, Primitive Bear, Trident Ursa, UNC530, and Winterflounder. Lively considering the fact that at minimum 2013, it really is assessed to be part of Russia’s Federal Security Services (FSB).
Delicate-PAWS, in addition to setting up persistence on the host, makes use of Telegram’s blogging system called Telegraph to retrieve the command-and-manage (C2) info, a approach previously discovered as associated with the adversary because early 2023, and can propagate by way of detachable connected drives.

Gamaredon’s capability to spread by means of USB drives was also documented by Check out Stage in November 2023, which named the PowerShell-centered USB worm LitterDrifter.
“The Subtle-PAWS backdoor uses highly developed strategies to execute malicious payloads dynamically,” the researchers stated.
“They retail store and retrieve executable PowerShell code from the Windows Registry which can guide in evading standard file-based mostly detection strategies. This solution also aids in retaining persistence on the infected method, as the malware can initiate by itself once more immediately after reboots or other interruptions.”
Found this short article attention-grabbing? Abide by us on Twitter and LinkedIn to study a lot more unique articles we put up.
Some components of this report are sourced from:
thehackernews.com


 Former CIA Engineer Sentenced to 40 Years for Leaking Classified Documents
Former CIA Engineer Sentenced to 40 Years for Leaking Classified Documents