As several as 23 new superior severity security vulnerabilities have been disclosed in diverse implementations of Unified Extensible Firmware Interface (UEFI) firmware applied by quite a few distributors, which includes Bull Atos, Fujitsu, HP, Juniper Networks, Lenovo, amongst others.
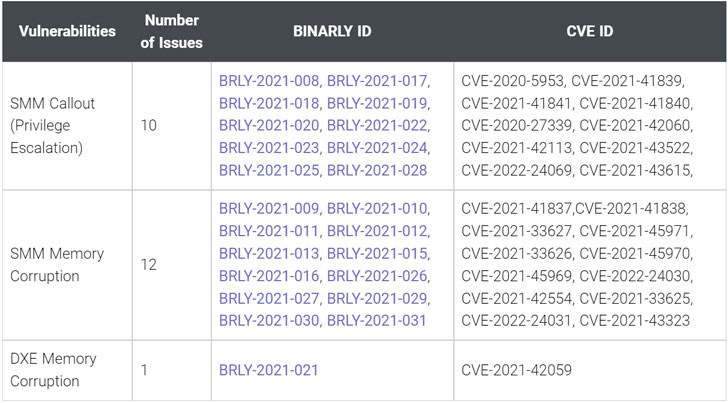
The vulnerabilities reside in Insyde Software’s InsydeH2O UEFI firmware, in accordance to organization firmware security business Binarly, with a greater part of the anomalies identified in the System Management Manner (SMM).
UEFI is a software package specification that delivers a common programming interface connecting a computer’s firmware to its working method during the booting system. In x86 units, the UEFI firmware is typically stored in the flash memory chip of the motherboard.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

“By exploiting these vulnerabilities, attackers can properly install malware that survives operating process re-installations and enables the bypass of endpoint security alternatives (EDR/AV), Secure Boot, and Virtualization-Centered Security isolation,” the scientists explained.
Productive exploitation of the flaws (CVSS scores: 7.5 – 8.2), could let a malicious actor to operate arbitrary code with SMM permissions, a unique-intent execution method in x86-based processors that handles electric power management, components configuration, thermal monitoring, and other features.
“SMM code executes in the optimum privilege stage and is invisible to the OS, which would make it an attractive target for destructive action,” Microsoft notes in its documentation, introducing the SMM attack vector could be abused by a piece of nefarious code to trick an additional code with better privileges into executing unauthorized routines.
Even worse, the weaknesses can also be chained together to bypass security attributes and put in malware in a manner that survives operating program re-installations and attain lengthy-phrase persistence on compromised programs — as noticed in the situation of MoonBounce — while stealthily creating a communications channel to exfiltrate sensitive info.
Insyde has introduced firmware patches that tackle these shortcomings as aspect of the coordinated disclosure course of action. But the truth that the application is utilised in quite a few OEM implementations indicates it could get a appreciable sum of time before the fixes in fact trickle down to afflicted gadgets.
Located this report interesting? Abide by THN on Facebook, Twitter and LinkedIn to read through much more distinctive information we write-up.
Some components of this report are sourced from:
thehackernews.com



 Hacker Group ‘Moses Staff’ Using New StrifeWater RAT in Ransomware Attacks
Hacker Group ‘Moses Staff’ Using New StrifeWater RAT in Ransomware Attacks