A variant of the notorious Dridex banking malware has established its sights on Apple’s macOS operating system applying a previously undocumented an infection technique, in accordance to most current exploration.
It has “adopted a new method to supply files embedded with malicious macros to consumers without the need of obtaining to pretend to be invoices or other business enterprise-linked data files,” Craze Micro researcher Armando Nathaniel Pedragoza reported in a technical report.
Dridex, also termed Bugat and Cridex, is an information stealer that’s acknowledged to harvest delicate knowledge from contaminated devices and supply and execute malicious modules. It is really attributed to an e-crime team acknowledged as Evil Corp (aka Indrik Spider).

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The malware is also thought of to be a successor of Gameover Zeus, itself a comply with-up to one more banking trojan termed Zeus. Prior Dridex strategies concentrating on Windows have leveraged macro-enabled Microsoft Excel paperwork despatched by means of phishing e-mails to deploy the payload.
Trend Micro’s assessment of the Dridex samples entails a Mach-O executable file, the earliest of which was submitted to VirusTotal in April 2019. Given that then, 67 more artifacts have been detected in the wild, some as new as December 2022.
The artifact, for its element, is made up of a destructive embedded document – initially detected way back in 2015 – that incorporates an Auto-Open up macro which is mechanically run upon opening the document.
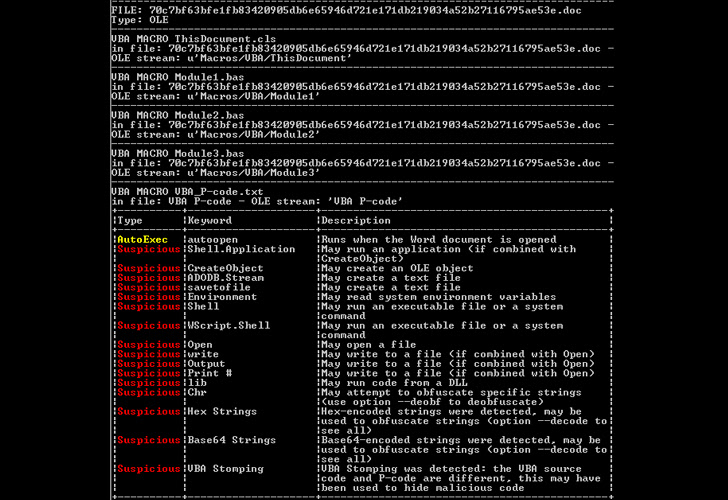
This is accomplished by overwriting all “.doc” information in the recent consumer directory (~/Person/user identify) with the malicious code extracted from the Mach-O executable in the type of a hexadecimal dump.
“When the macro aspect in Microsoft Phrase is disabled by default, the malware will overwrite all the document files for the current consumer, which include the clean data files,” Pedragoza described. “This would make it extra tough for the consumer to determine irrespective of whether the file is malicious due to the fact it does not occur from an exterior resource.”
The macros included in the overwritten document are engineered to get hold of a remote server to retrieve extra data files, which features a Windows executable file that will not operate in macOS, indicating that the attack chain is a perform in development. The binary, in switch, tries to download the Dridex loader on to the compromised device.
When files that contains booby-trapped macros are usually shipped via social engineering attacks, the findings when once again present that Microsoft’s determination to block macros by default has prompted threat actors to refine their methods and find more economical solutions of entry.
“At the moment, the influence on macOS buyers for this Dridex variant is minimized considering the fact that the payload is an exe file (and hence not compatible with MacOS environments),” Pattern Micro explained. “Having said that, it still overwrites document documents which are now the carriers of Dridex’s malicious macros.”
Observed this article fascinating? Abide by us on Twitter and LinkedIn to study a lot more special material we submit.
Some sections of this write-up are sourced from:
thehackernews.com

 Cyber attacks on UK organisations surged 77% in 2022, new research finds
Cyber attacks on UK organisations surged 77% in 2022, new research finds