A new info stealer named ExelaStealer has become the hottest entrant to an presently crowded landscape loaded with different off-the-shelf malware developed to capture sensitive facts from compromised Windows techniques.
“ExelaStealer is a mostly open up-resource infostealer with paid out customizations available from the danger actor,” Fortinet FortiGuard Labs researcher James Slaughter mentioned in a specialized report.
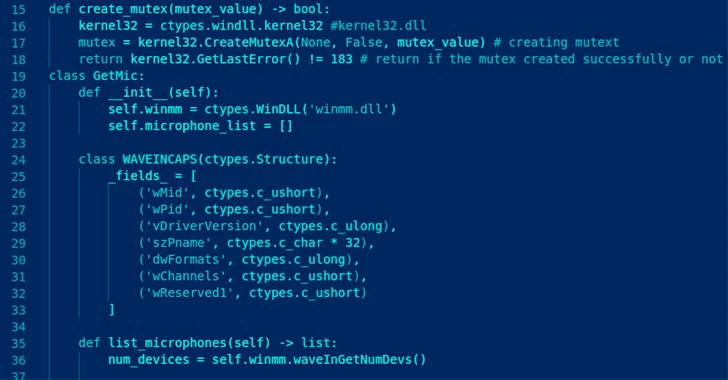
Written in Python and incorporating support for JavaScript, it will come equipped with abilities to siphon passwords, Discord tokens, credit playing cards, cookies and session details, keystrokes, screenshots, and clipboard material.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
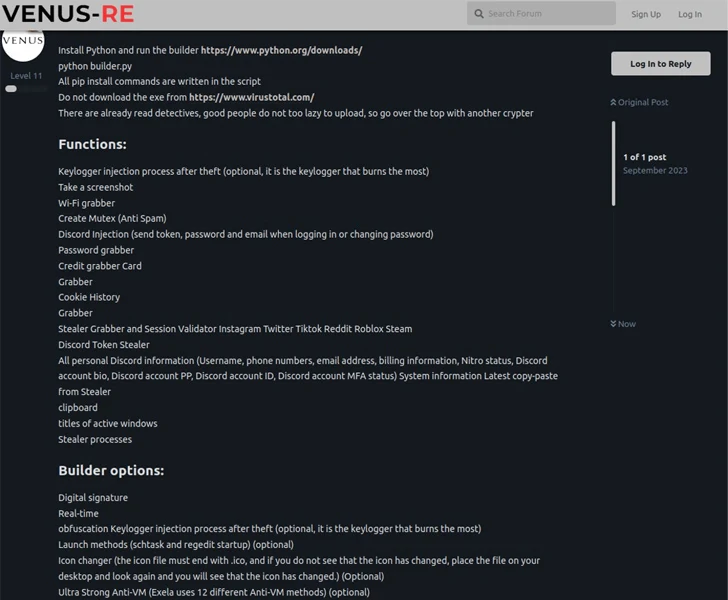
ExelaStealer is presented for sale by means of cybercrime community forums as nicely as a focused Telegram channel established up by its operators who go by the on line alias quicaxd. The compensated-for model costs $20 a thirty day period, $45 for 3 months, or $120 for a life time license.

The small price tag of the commodity malware makes it a perfect hacking resource for rookies, effectively reducing the barrier to entry for pulling off destructive attacks.
The stealer binary, in its current sort, can only be compiled and packaged on a Windows-based technique making use of a builder Python script, which throws needed supply code obfuscation to the combine in an endeavor to resist assessment.
There is evidence to propose that ExelaStealer is becoming distributed by using an executable that masquerades as a PDF doc, indicating that the first intrusion vector could be nearly anything ranging from phishing to watering holes.
Launching the binary displays a entice doc – a Turkish car registration certificate for a Dacia Duster – though stealthily activating the stealer in the qualifications.
“Data has come to be a important forex, and due to the fact of this, tries to assemble it will likely by no means stop,” Slaughter said.
“Infostealer malware exfiltrates knowledge belonging to companies and folks that can be made use of for blackmail, espionage, or ransom. Even with the selection of infostealers in the wild, ExelaStealer demonstrates there is continue to room for new gamers to arise and obtain traction.”

The disclosure will come as Kaspersky disclosed aspects of a campaign that targets government, law enforcement, and non-income organizations to fall many scripts and executables at as soon as to conduct cryptocurrency mining, steal details using keyloggers, and get backdoor obtain to systems.
“The B2B sector stays beautiful to cybercriminals, who request to exploit its assets for income-earning purposes,” the Russian cybersecurity organization reported, noting that most of the attacks had been aimed at corporations in Russia, Saudi Arabia, Vietnam, Brazil, Romania, the U.S., India, Morocco, and Greece.
Previously this week, U.S. cybersecurity and intelligence companies launched a joint advisory outlining the phishing procedures destructive actors normally use to obtain login credentials and deploy malware, highlighting their tries to impersonate a trusted source to comprehend their targets.
Found this write-up exciting? Follow us on Twitter and LinkedIn to go through more unique articles we put up.
Some elements of this write-up are sourced from:
thehackernews.com

 U.S. DoJ Cracks Down on North Korean IT Scammers Defrauding Global Businesses
U.S. DoJ Cracks Down on North Korean IT Scammers Defrauding Global Businesses