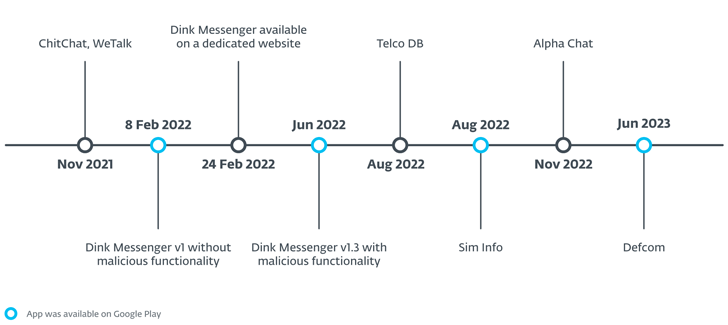
An active Android malware campaign dubbed Exotic Go to has been mainly focusing on customers in South Asia, especially these in India and Pakistan, with malware distributed by using devoted sites and Google Play Store.
Slovak cybersecurity company claimed the activity, ongoing since November 2021, is not connected to any regarded menace actor or team. It really is monitoring the team at the rear of the procedure underneath the name Digital Invaders.
“Downloaded applications provide legit operation, but also include things like code from the open up-source Android XploitSPY RAT,” ESET security researcher Lukáš Štefanko reported in a technological report produced these days.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The campaign is reported to be remarkably qualified in mother nature, with the apps available on Google Perform getting negligible quantity of installs ranging from zero to 45. The applications have given that been taken down.

The phony-but-purposeful apps largely masquerade as messaging companies like Alpha Chat, ChitChat, Defcom, Dink Messenger, Signal Lite, TalkU, WeTalk, Wicker Messenger, and Zaangi Chat. Roughly 380 victims are explained to have downloaded the apps and created accounts to use them for messaging applications.
Also employed as part of Exotic Check out are apps such as Sim Info and Telco DB, both of which declare to offer aspects about SIM proprietors merely by moving into a Pakistan-based phone quantity. Other programs move off as a foodstuff purchasing service in Pakistan as well as a legit Indian healthcare facility called Expert Healthcare facility (now rebranded as Trilife Medical center).
XploitSPY, uploaded to GitHub as early as April 2020 by a person named RaoMK, is related with an Indian cyber security methods organization called XploitWizer. It has also been described as a fork of one more open-resource Android trojan referred to as L3MON, which, in switch, draws inspiration from AhMyth.
It comes with a vast gamut of options that permits it to get delicate information from contaminated devices, this sort of as GPS locations, microphone recordings, contacts, SMS messages, phone logs, and clipboard content extract notification particulars from applications like WhatsApp, Facebook, Instagram, and Gmail obtain and add information watch installed applications and queue commands.
On leading of that, the malicious apps are designed to consider photographs and enumerate data files in a number of directories linked to screenshots, WhatApp, WhatsApp Enterprise, Telegram, and an unofficial WhatsApp mod recognised as GBWhatsApp.

“All through the decades, these menace actors have custom-made their destructive code by including obfuscation, emulator detection, hiding of [command-and-control] addresses, and use of a indigenous library,” Štefanko claimed.
The most important goal of the indigenous library (“defcome-lib.so”) is to continue to keep the C2 server information encoded and hidden from static investigation resources. If an emulator is detected, the application can make use of a phony C2 server to evade detection.
Some of the applications have been propagated by way of web-sites specifically established for this intent (“chitchat.ngrok[.]io”) that provide a url to an Android bundle file (“ChitChat.apk”) hosted on GitHub. It really is presently not crystal clear how victims are directed to these applications.
“Distribution begun on committed sites and then even moved to the official Google Perform keep,” Štefanko concluded. “The objective of the marketing campaign is espionage and probably is concentrating on victims in Pakistan and India.”
Found this post attention-grabbing? Adhere to us on Twitter and LinkedIn to browse far more special content material we post.
Some pieces of this posting are sourced from:
thehackernews.com


 Raspberry Robin Returns: New Malware Campaign Spreading Through WSF Files
Raspberry Robin Returns: New Malware Campaign Spreading Through WSF Files