Cybersecurity researchers have managed to construct a clone of Apple Airtag that circumvents the anti-stalking safety technology constructed into its Find My Bluetooth-based monitoring protocol.
The final result is a stealth AirTag that can successfully monitor an iPhone consumer for above five times without the need of triggering a monitoring notification, Good Security’s co-founder Fabian Bräunlein reported in a deep-dive revealed past 7 days.
Uncover My is Apple’s asset monitoring app that enables users to monitor the GPS location of iOS, iPadOS, macOS, watchOS units, AirPods, AirTags as well as other supported third-party equipment by means of a connected iCloud account. It also enables buyers to perspective the spot of many others who have opted to share their location.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

This is considerably from the to start with time weaknesses have been uncovered in Apple’s Locate My system. In March 2021, the Protected Cell Networking Lab at the Technological University of Darmstadt, Germany (SEEMO) disclosed style and implementation flaws in the protocol that can guide to a site correlation attack and unauthorized obtain to users’ site histories
Then in Might 2021, Bräunlein followed it up by sharing aspects of a conversation protocol created on leading of Discover My that permits arbitrary information to be uploaded from non-internet-connected equipment by sending “Find My” Bluetooth broadcasts to close by Apple gadgets that can have out the facts upload.
The progress also comes as Apple, before this thirty day period, introduced a raft of new anti-stalking actions to AirTags to protect against their misuse involved with tracking unsuspecting folks without having their consent, inserting a warning notifying end users that performing so has prison repercussions.
“If an AirTag, set of AirPods, or Uncover My network accent is uncovered to be unlawfully monitoring a man or woman, regulation enforcement can ask for any readily available info from Apple to assistance their investigation,” Apple spells out in an current help posting.
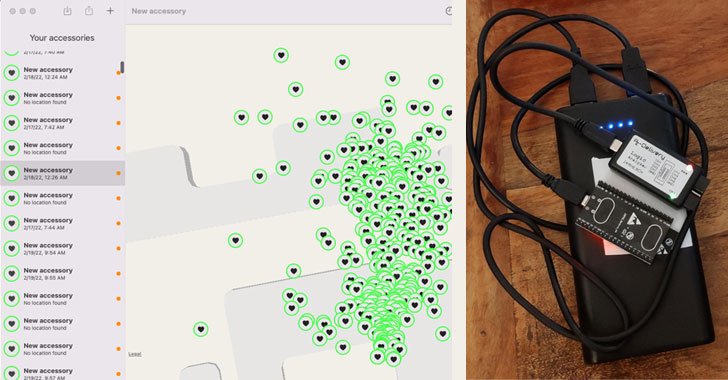
But the “Uncover You” AirTag clone devised by Constructive Security aims to get around “every single present-day and approaching security evaluate.” It truly is also designed working with OpenHaystack, an open-supply framework made by SEEMO researchers for tracking individual Bluetooth equipment by means of Apple’s crowdsourced Locate My network.
By broadcasting new, never ever-witnessed-ahead of public keys each and every 30 seconds from a checklist of 2,000 preloaded community keys via the evidence-of-strategy (PoC) device, it was observed that the mechanism renders the monitoring gadget undetectable, raising no alerts in iOS and Apple’s have Tracker Detect Android application even when undesirable AirTags are present.
Apparently, AirGuard, which was created by SEEMO as a 3rd-party alternate to Tracker Detect, is capable of getting the clone in “guide scan” method, calling into concern the success of the safety and security limitations carried out by Apple to safeguard buyers from the destructive use of AirTags.
“The ubiquitous nature of the Uncover My network, merged with its higher precision and minimal entry price tag, lowers the bar for abuse,” SEEMO researchers Alexander Heinrich, Niklas Bittner, and Matthias Hollick claimed in a new paper, pointing out how “AirGuard observed more precise trackers in various eventualities compared to the iOS tracking detection.”
“Apple desires to incorporate non-genuine AirTags into their menace product, as a result applying security and anti-stalking options into the Uncover My protocol and ecosystem in its place of in the AirTag alone, which can run modified firmware or not be an AirTag at all,” Bräunlein claimed.
Identified this posting exciting? Observe THN on Facebook, Twitter and LinkedIn to go through far more exceptional content material we publish.
Some components of this short article are sourced from:
thehackernews.com


 Iranian Hackers Using New Spying Malware That Abuses Telegram Messenger API
Iranian Hackers Using New Spying Malware That Abuses Telegram Messenger API