Cybersecurity researchers have unmasked a prolific danger actor recognised as farnetwork, who has been connected to 5 distinctive ransomware-as-a-support (RaaS) programs more than the earlier 4 a long time in various capacities.
Singapore-headquartered Team-IB, which tried to infiltrate a non-public RaaS application that employs the Nokoyawa ransomware pressure, reported it underwent a “position interview” process with the risk actor, discovering various beneficial insights into their qualifications and position.
“Through the menace actor’s cybercriminal job, which started in 2019, farnetwork has been associated in numerous linked ransomware projects, together with JSWORM, Nefilim, Karma, and Nemty, as section of which they assisted create ransomware and handle the RaaS applications right before launching their have RaaS program based mostly on Nokoyawa ransomware,” Nikolay Kichatov, threat intelligence analyst at Team-IB, explained.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

The latest disclosure arrives almost 6 months after the cybersecurity firm penetrated the Qilin RaaS gang, uncovering aspects about the affiliates’ payment construction and the inner workings of the RaaS software.
Farnetwork is regarded to function beneath numerous aliases these kinds of as farnetworkit, farnetworkl, jingo, jsworm, piparkuka, and razvrat on distinct underground message boards like RAMP, originally advertising and marketing a remote entry trojan identified as referred to as RazvRAT as a seller.
In 2022, other than shifting focus to Nokoyawa, the Russian-speaking individual is claimed to have launched their own botnet provider to deliver affiliate marketers with access to compromised corporate networks.
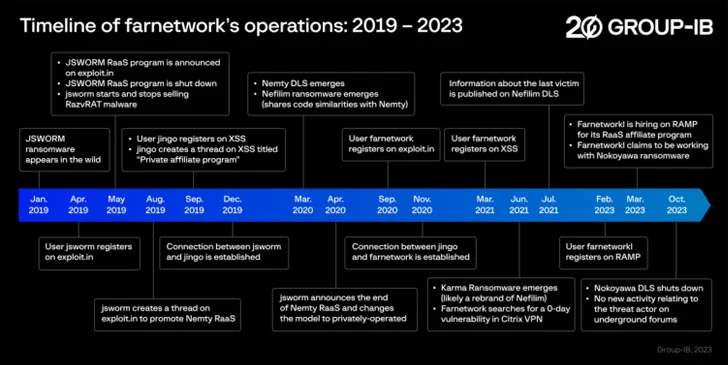
Given that the start off of the yr, farnetwork has been linked to recruitment efforts for the Nokoyawa RaaS system, asking probable candidates to facilitate privilege escalation applying stolen company account qualifications and deploy the ransomware to encrypt a victim’s documents, and then demand payment in return for the decryption important.
The credentials are sourced from info stealer logs bought on underground marketplaces, where in other menace actors get first access to goal endpoints by distributing off-the-shelf stealer malware like RedLine that are, in change, pushed as a result of phishing and malvertising campaigns.

The RaaS product lets affiliate marketers to receive 65% of the ransom amount of money and the botnet proprietor to acquire 20%. The ransomware developer, on the other hand, gets 15% of the overall share, a quantity that could drop additional down to 10%.
Nokoyawa has considering the fact that ceased its operations as of October 2023, though Group-IB mentioned there is a large probability that farnetwork would resurface underneath a diverse name and with a new RaaS application.
“Farnetwork is an expert and very competent danger actor,” Kichatov reported, describing the risk actor as a person of the “most energetic players of the RaaS sector.”
Uncovered this posting appealing? Abide by us on Twitter and LinkedIn to study a lot more special content we publish.
Some areas of this article are sourced from:
thehackernews.com


 N. Korean BlueNoroff Blamed for Hacking macOS Machines with ObjCShellz Malware
N. Korean BlueNoroff Blamed for Hacking macOS Machines with ObjCShellz Malware