Malicious actors can consider advantage of “insufficient” forensic visibility into Google Cloud System (GCP) to exfiltrate delicate facts, a new research has observed.
“Sad to say, GCP does not provide the level of visibility in its storage logs that is desired to make it possible for any productive forensic investigation, making companies blind to potential knowledge exfiltration attacks,” cloud incident response business Mitiga stated in a report.
The attack banks on the prerequisite that the adversary is able to achieve command of an identity and obtain administration (IAM) entity in the targeted corporation by procedures like social engineering to obtain the GCP natural environment.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The crux of the dilemma is that GCP’s storage obtain logs do not present sufficient transparency with regards to potential file entry and read through gatherings, in its place grouping them all as a single “Object Get” exercise.
“The identical occasion is utilized for a broad wide range of sorts of entry, such as: Studying a file, downloading a file, copying a file to an external server, [and] looking at the metadata of the file,” Mitiga researcher Veronica Marinov reported.
This deficiency of difference could permit an attacker to harvest delicate details without the need of becoming detected, generally since there is no way to differentiate among destructive and respectable consumer action.
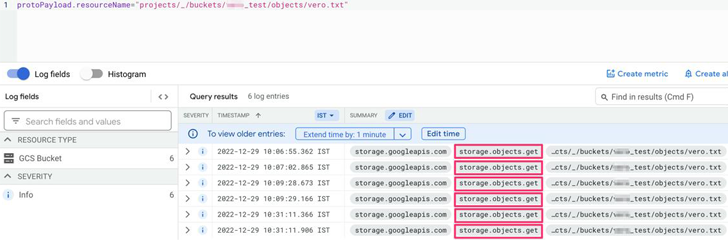
In a hypothetical attack, a threat actor can use Google’s command line interface (gsutil) to transfer worthwhile data from the target organization’s storage buckets to an exterior storage bucket in just the attacker organization.
Find out the Most up-to-date Malware Evasion Ways and Prevention Strategies
Ready to bust the 9 most hazardous myths about file-centered attacks? Join our upcoming webinar and turn into a hero in the struggle versus patient zero bacterial infections and zero-day security gatherings!
RESERVE YOUR SEAT
Google has due to the fact supplied mitigation recommendations, which selection from Virtual Private Cloud (VPC) Support Controls to using organization restriction headers to limit cloud useful resource requests.
The disclosure will come as Sysdig unearthed a subtle attack campaign dubbed SCARLETEEL which is targeting containerized environments to perpetrate theft of proprietary knowledge and software program.
Discovered this article intriguing? Comply with us on Twitter and LinkedIn to read through far more special written content we article.
Some pieces of this short article are sourced from:
thehackernews.com


 City of Oakland Faces Major Data Leak
City of Oakland Faces Major Data Leak