Cybersecurity scientists have lose light on an actively maintained remote obtain trojan called DCRat (aka DarkCrystal RAT) which is supplied on sale for “filth low cost” charges, making it accessible to professional cybercriminal groups and amateur actors alike.
“In contrast to the very well-funded, significant Russian threat groups crafting personalized malware […], this remote access Trojan (RAT) appears to be the work of a lone actor, presenting a astonishingly helpful do-it-yourself device for opening backdoors on a spending plan,” BlackBerry researchers claimed in a report shared with The Hacker News.
“In reality, this risk actor’s business RAT sells at a fraction of the regular price this kind of instruments command on Russian underground boards.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Written in .NET by an individual codenamed “boldenis44” and “crystalcoder,” DCRat is a comprehensive-highlighted backdoor whose functionalities can be additional augmented by 3rd-party plugins designed by affiliate marketers making use of a committed built-in development setting (IDE) referred to as DCRat Studio.
It was to start with introduced in 2018, with version 3. shipping on Could 30, 2020, and model 4. launching almost a calendar year later on March 18, 2021.
Costs for the trojan start out at 500 RUB ($5) for a two-thirty day period license, 2,200 RUB ($21) for a calendar year, and 4,200 RUB ($40) for a lifetime subscription, figures which are even more lowered throughout distinctive promotions.
Though a preceding evaluation by Mandiant in Might 2020 traced the RAT’s infrastructure to information.dcrat[.]ru, the malware bundle is currently hosted on a distinctive area named crystalfiles[.]ru, indicating a change in reaction to public disclosure.
“All DCRat advertising and sales operations are completed by the popular Russian hacking discussion board lolz[.]guru, which also handles some of the DCRat pre-sales queries,” the scientists claimed.
Also actively utilized for communications and sharing information about application and plugin updates is a Telegram channel which has about 2,847 subscribers as of crafting.
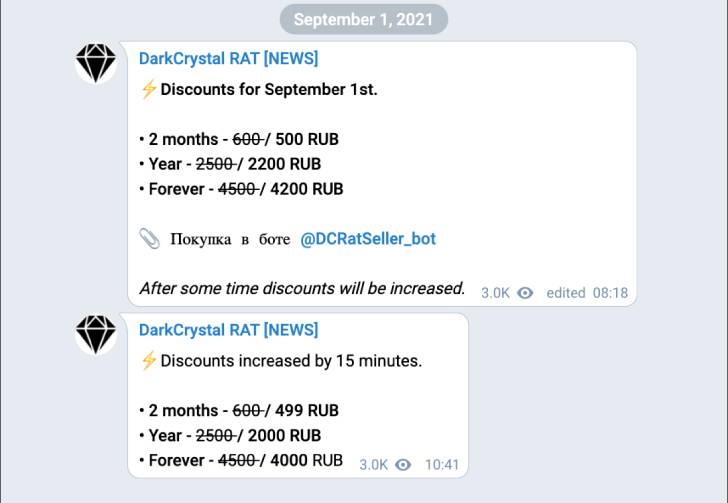
Messages posted on the channel in modern months cover updates to CryptoStealer, TelegramNotifier, and WindowsDefenderExcluder plugins, as very well as “cosmetic modifications/fixes” to the panel.
“Some Fun features have been moved to the typical plugin,” a translated information shared on April 16 reads. “The weight of the develop has slightly diminished. There must be no detects that go precisely to these features.”
Apart from its modular architecture and bespoke plugin framework, DCRat also encompasses an administrator part that is engineered to stealthily induce a eliminate switch, which enables the threat actor to remotely render the instrument unusable.
The admin utility, for its part, enables subscribers to signal in to an lively command-and-handle server, issue instructions to infected endpoints, and post bug stories, among other people.
Distribution vectors employed to infect hosts with DCRat include things like Cobalt Strike Beacons and a targeted traffic course method (TDS) termed Prometheus, a subscription-based mostly crimeware-as-a-assistance (CaaS) alternative utilized to produce a wide range of payloads.
The implant, in addition to collecting process metadata, supports surveillance, reconnaissance, information theft, and DDoS attack abilities. It can also capture screenshots, document keystrokes, and steal articles from clipboard, Telegram, and web browsers.
“New plugins and insignificant updates are announced nearly each day,” the scientists said. “If the threat is remaining designed and sustained by just one particular individual, it appears that it can be a job they are working on total-time.”
Observed this short article intriguing? Follow THN on Fb, Twitter and LinkedIn to browse much more exceptional information we write-up.
Some parts of this write-up are sourced from:
thehackernews.com

 SHIELDS UP in bite sized chunks
SHIELDS UP in bite sized chunks