A number of menace actors have been noticed opportunistically weaponizing a now-patched critical security vulnerability impacting numerous Zoho ManageEngine products considering that January 20, 2023.
Tracked as CVE-2022-47966 (CVSS rating: 9.8), the distant code execution flaw will allow a comprehensive takeover of the inclined methods by unauthenticated attackers.
As quite a few as 24 diverse solutions, like Accessibility Supervisor In addition, ADManager Moreover, ADSelfService As well as, Password Supervisor Pro, Remote Accessibility Additionally, and Distant Checking and Management (RMM), are influenced by the issue.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The shortcoming “makes it possible for unauthenticated remote code execution because of to use of an outdated third-party dependency for XML signature validation, Apache Santuario,” Bitdefender’s Martin Zugec reported in a complex advisory shared with The Hacker Information.
According to the Romanian cybersecurity company, the exploitation attempts are reported to have commenced the working day after penetration screening organization Horizon3.ai introduced a evidence-of-strategy (PoC) last thirty day period.
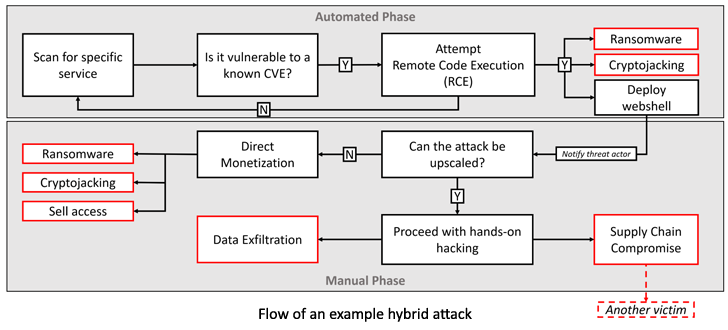
A majority of the attack victims are found in Australia, Canada, Italy, Mexico, the Netherlands, Nigeria, Ukraine, the U.K., and the U.S.
The main goal of the attacks detected to day revolves all-around deploying instruments on vulnerable hosts this sort of as Netcat and Cobalt Strike Beacon.
Some intrusions have leveraged the initial access to set up AnyDesk application for remote obtain, though a number of others have tried to install a Windows version of a ransomware strain recognized as Buhti.
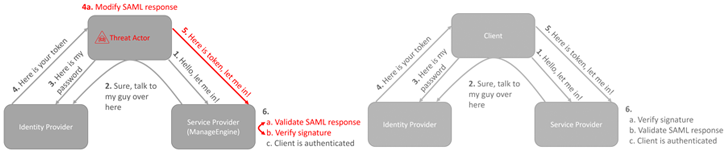
What is actually additional, there is evidence of a qualified espionage operation, with the risk actors abusing the ManageEngine flaw to deploy malware capable of executing following-stage payloads.
“This vulnerability is a different clear reminder of the worth of retaining programs up to date with the newest security patches although also using solid perimeter defense,” Zugec stated.
“Attackers do not require to scour for new exploits or novel tactics when they know that several companies are vulnerable to older exploits because of, in aspect, to the absence of appropriate patch administration and risk management.”
Discovered this write-up appealing? Comply with us on Twitter and LinkedIn to read a lot more distinctive material we submit.
Some parts of this report are sourced from:
thehackernews.com

 The Secret Vulnerability Finance Execs are Missing
The Secret Vulnerability Finance Execs are Missing