A destructive browser extension with 350 variants is masquerading as a Google Translate add-on as part of an adware marketing campaign targeting Russian consumers of Google Chrome, Opera, and Mozilla Firefox browsers.
Mobile security organization Zimperium dubbed the malware family ABCsoup, stating the “extensions are put in onto a victim’s machine by means of a Windows-primarily based executable, bypassing most endpoint security solutions, alongside with the security controls found in the official extension outlets.”
The rogue browser incorporate-ons appear with the identical extension ID as that of Google Translate — “aapbdbdomjkkjkaonfhkkikfgjllcleb” — in an endeavor to trick people into believing that they have mounted a genuine extension.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The extensions are not offered on the formal browser web merchants on their own. Somewhat they are shipped by diverse Windows executables that install the include-on on the victim’s web browser.
In the function the qualified person already has the Google Translate extension put in, it replaces the primary variation with the malicious variant owing to their greater version numbers (30.2.5 vs. 2..10).
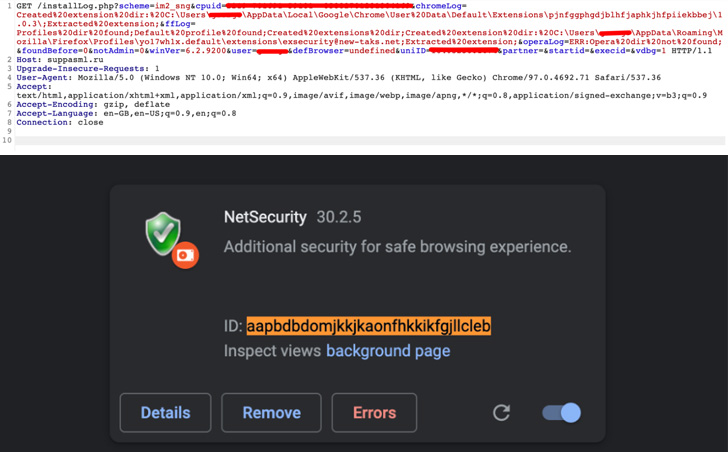
“On top of that, when this extension is put in, Chrome Web Retail outlet assumes that it is Google Translate and not the destructive extension since the Web Retail store only checks for extension IDs,” Zimperium researcher Nipun Gupta said.
All the noticed variants of the extension are geared toward serving pop-ups, harvesting particular data to produce focus on-distinct advertisements, fingerprinting searches, and injecting malicious JavaScript that can even more act as a adware to seize keystrokes and observe web browser activity.
The main perform of ABCsoup involves examining for Russian social networking providers like Odnoklassniki and VK amid the present websites opened in the browser, and if so, get the users’ 1st and previous names, dates of start, and gender, and transmit the data to a distant server.

Not only does the malware use this details to provide personalised adverts, the extension also will come with capabilities to inject personalized JavaScript code dependent on the websites opened. This involves YouTube, Facebook, ASKfm, Mail.ru, Yandex, Rambler, Avito, Brainly’s Znanija, Kismia, and rollApp, suggesting a large Russia target.
Zimperium attributed the campaign to a “very well-arranged team” of Eastern European and Russian origin, with the extensions designed to target Russian users presented the large wide variety of nearby domains focused.
“This malware is purposefully designed to concentrate on all kinds of people and serves its goal of retrieving consumer information and facts,” Gupta said. “The injected scripts can be effortlessly utilized to serve extra malicious habits into the browser session, this sort of as keystroke mapping and knowledge exfiltration.”
Located this write-up attention-grabbing? Observe THN on Fb, Twitter and LinkedIn to read more unique content material we article.
Some sections of this short article are sourced from:
thehackernews.com

 U.S. Healthcare Orgs Targeted with Maui Ransomware
U.S. Healthcare Orgs Targeted with Maui Ransomware