A new attack campaign has focused the gaming and gambling sectors given that at least September 2022, just months prior to the ICE London 2023 gaming sector trade good celebration that’s scheduled up coming 7 days.
Israeli cybersecurity firm Security Joes is tracking the action cluster less than the title Ice Breaker, stating the intrusions utilize intelligent social engineering methods to deploy a JavaScript backdoor.
The attack sequence proceeds as follows: The menace actor poses as a customer although initiating a discussion with a help agent of a gaming web-site and urges the unique on the other end to open a screenshot image hosted on Dropbox.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Security Joes stated that the risk actor is “very well-knowledgeable of the actuality that the customer support is human-operated.”
Clicking the malicious website link despatched in the chat leads to the retrieval of an LNK payload or, alternatively, a VBScript file as a backup solution, the previous of which is configured to obtain and operate an MSI package that contains a Node.js implant.
The JavaScript file has all the capabilities of a standard backdoor, enabling the menace actor to enumerate working procedures, steal passwords and cookies, exfiltrate arbitrary documents, get screenshots, run VBScript imported from a distant server, and even open up a reverse proxy on the compromised host.
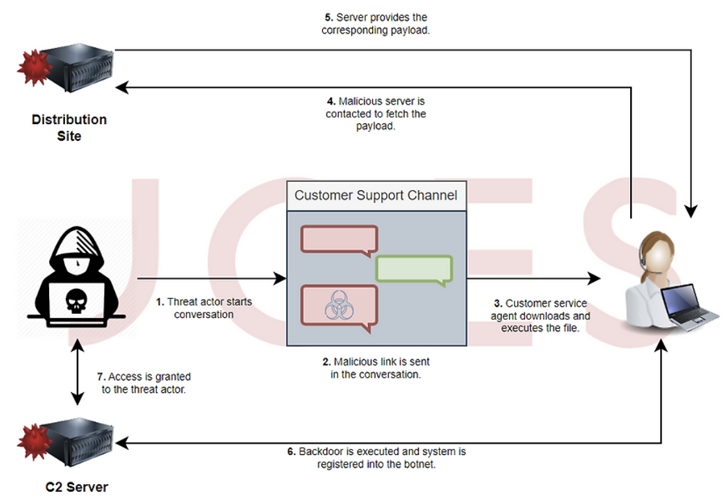
Need to the VBS downloader be executed by the sufferer, the infection culminates in the deployment of Houdini, a VBS-based mostly distant access trojan that dates again to 2013.
The risk actors’ origins are currently mysterious, even though they have been noticed working with damaged English in the course of their conversations with consumer assistance agents. Some indicators of compromise (IoCs) involved with the campaign were formerly shared by the MalwareHunterTeam in Oct 2022.
“This is a remarkably helpful attack vector for the gaming and gambling industry,” Felipe Duarte, senior danger researcher at Security Joes, reported.
“The in no way-found-in advance of compiled JavaScript next stage malware is hugely complex to dissect, showing that we are working with a competent threat actor with the probable of remaining sponsored by an interest operator.”
Discovered this article exciting? Abide by us on Twitter and LinkedIn to read more exclusive articles we article.
Some elements of this write-up are sourced from:
thehackernews.com


 BEC Group Uses Open Source Tactics in Hundreds of Attacks
BEC Group Uses Open Source Tactics in Hundreds of Attacks