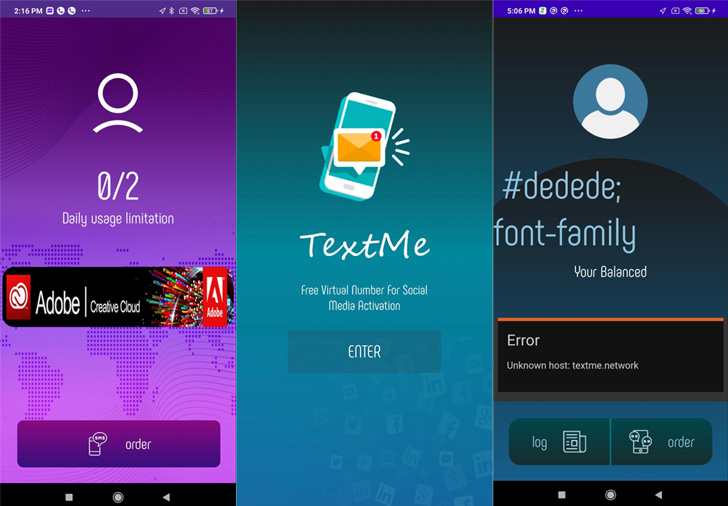
A novel Android malware referred to as RatMilad has been observed concentrating on a Middle Jap business cell device by concealing by itself as a VPN and phone selection spoofing app.
The mobile trojan features as highly developed spyware with abilities that gets and executes instructions to acquire and exfiltrate a broad assortment of facts from the contaminated mobile endpoint, Zimperium claimed in a report shared with The Hacker Information.
Proof gathered by the cellular security business exhibits that the destructive app is dispersed by one-way links on social media and communication tools like Telegram, tricking unsuspecting consumers into sideloading the app and granting it substantial permissions.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

The thought behind embedding the malware in just a bogus VPN and phone variety spoofing services is also clever in that the app promises to allow customers to validate social media accounts by using phone, a approach well known in nations exactly where entry is restricted.
“Once set up and in manage, the attackers could access the digicam to get pics, record online video and audio, get specific GPS spots, view pictures from the machine, and a lot more,” Zimperium researcher Nipun Gupta mentioned.
Other functions of RatMilad make it feasible for the malware to amass SIM information, clipboard knowledge, SMS messages, simply call logs, speak to lists, and even complete file go through and create operations.
Zimperium hypothesized that the operators responsible for RatMilad obtained supply code from an Iranian hacker team dubbed AppMilad and integrated it into a fraudulent application for distributing it to unwitting customers.
The scale of the infections is unidentified, but the cybersecurity business said it detected the spyware through a failed compromise attempt of a customer’s company gadget.

A submit shared on a Telegram channel utilised to propagate the malware sample has been seen over 4,700 instances with additional than 200 external shares, indicating a restricted scope.
“The RatMilad spy ware and the Iranian-based mostly hacker team AppMilad depict a changing environment impacting cell product security,” Richard Melick, director of cellular menace intelligence at Zimperium, explained.
“From Pegasus to PhoneSpy, there is a expanding cellular spy ware market readily available via authentic and illegitimate resources, and RatMilad is just 1 in the blend.”
Located this post attention-grabbing? Follow THN on Fb, Twitter and LinkedIn to read through much more unique content material we submit.
Some elements of this posting are sourced from:
thehackernews.com


 Telstra Telecom Suffers Data Breach Potentially Exposing Employee Information
Telstra Telecom Suffers Data Breach Potentially Exposing Employee Information