Suspected North Korean country-condition actors specific a journalist in South Korea with a malware-laced Android app as aspect of a social engineering marketing campaign.
The findings come from South Korea-centered non-income Interlab, which coined the new malware RambleOn.
The destructive functionalities consist of the “skill to read and leak target’s get in touch with record, SMS, voice connect with written content, site and others from the time of compromise on the goal,” Interlab threat researcher Ovi Liber said in a report published this 7 days.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The spy ware camouflages as a safe chat app termed Fizzle (ch.seme), but in reality, acts as a conduit to deliver a subsequent-phase payload hosted on pCloud and Yandex.
The chat application is claimed to have been despatched as an Android Deal (APK) file in excess of WeChat to the targeted journalist on December 7, 2022, below the pretext of wanting to focus on a sensitive topic.
The main objective of RambleOn is to operate as a loader for a further APK file (com.data.WeCoin) though also requesting for intrusive permissions to acquire information, entry connect with logs, intercept SMS messages, record audio, and locale information.
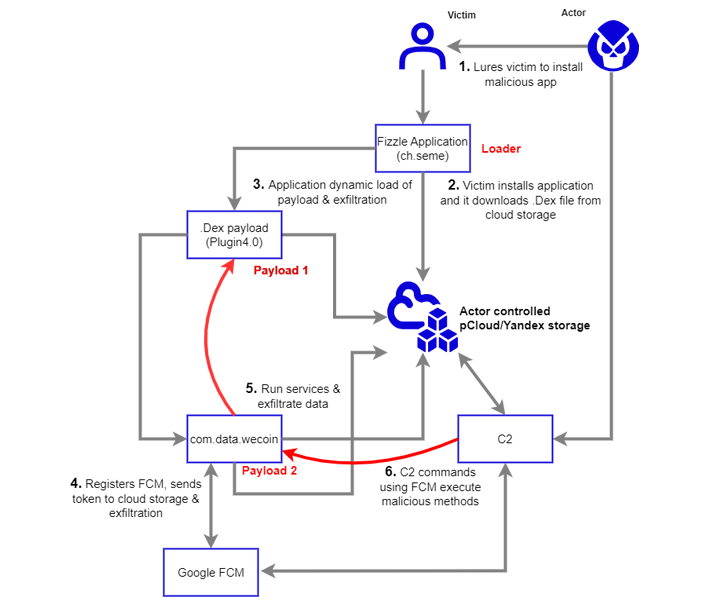
The secondary payload, for its aspect, is intended to deliver an substitute channel for accessing the contaminated Android product applying Firebase Cloud Messaging (FCM) as a command-and-management (C2) system.
Interlab reported it identified overlaps in the FCM functionality involving RambleOn and FastFire, a piece of Android spyware that was attributed to Kimsuky by South Korean cybersecurity business S2W very last calendar year.
“The victimology of this function fits incredibly intently with the modus operandi of groups these types of as APT37 and Kimsuky,” Liber said, pointing out the former’s use of pCloud and Yandex storage for payload shipping and command-and-command.
Observed this short article exciting? Follow us on Twitter and LinkedIn to study far more exceptional content we put up.
Some elements of this posting are sourced from:
thehackernews.com

 Atlassian breach sparks brief blame game with app provider
Atlassian breach sparks brief blame game with app provider