At minimum fifty percent of dozen GitHub accounts from fake researchers associated with a fraudulent cybersecurity company have been noticed pushing malicious repositories on the code hosting services.
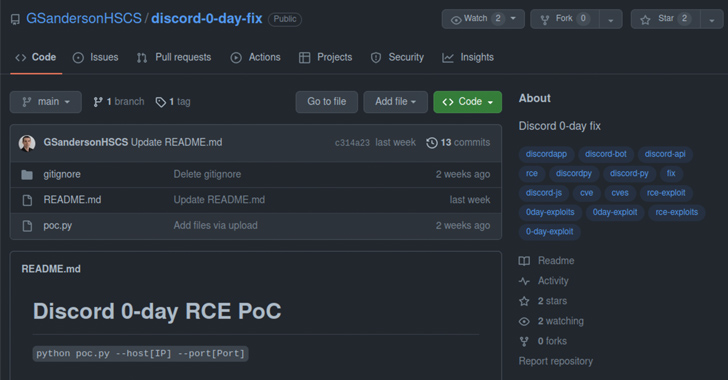
All seven repositories, which are even now out there as of composing, declare to be a proof-of-concept (PoC) exploit for purported zero-working day flaws in Discord, Google Chrome, and Microsoft Exchange.
VulnCheck, which found the activity, claimed, “the persons generating these repositories have place major work into creating them search authentic by producing a network of accounts and Twitter profiles, pretending to be element of a non-existent organization called High Sierra Cyber Security.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

The cybersecurity organization stated it initial came throughout the rogue repositories in early May when they have been observed pushing similar PoC exploits for zero-day bugs in Signal and WhatsApp. The two repositories have considering that been taken down.
Other than sharing some of the purported results on Twitter in an try to build legitimacy, the network of accounts even takes advantage of headshots of precise security scientists from corporations like Speedy7, suggesting that the threat actors place important work into crafting the marketing campaign.
The PoC is a Python script which is built to obtain a malicious binary and execute it on the victim’s running method, be it Windows or Linux.
Future WEBINAR🔐 Mastering API Security: Knowledge Your Real Attack Surface
Find out the untapped vulnerabilities in your API ecosystem and consider proactive steps in the direction of ironclad security. Be a part of our insightful webinar!
Join the Session.wn-button,.wn-label,.wn-label:afterexhibit:inline-block.check out_two_webinarmargin:20px 10px 30px 0background:#f9fbffcolor:#160755padding: 5%border:2px stable #d9deffborder-radius:10pxtext-align:leftbox-shadow:10px 10px #e2ebff-webkit-border-major-left-radius:25px-moz-border-radius-topleft:25px-webkit-border-bottom-correct-radius:25px-moz-border-radius-bottomright:25px.wn-labelfont-size:13pxmargin:20px 0font-fat:600letter-spacing:.6pxcolor:#596cec.wn-label:just afterwidth:50pxheight:6pxcontent:”border-prime:2px strong #d9deffmargin: 8px.wn-titlefont-sizing:21pxpadding:10px 0font-bodyweight:900text-align:leftline-peak:33px.wn-descriptiontext-align:leftfont-size:15.6pxline-top:26pxmargin:5px !importantcolor:#4e6a8d.wn-buttonpadding:6px 12pxborder-radius:5pxbackground-coloration:#4469f5font-dimensions:15pxcolor:#fff!importantborder:0line-top:inherittext-decoration:none!importantcursor:pointermargin:15px 20pxfloat:leftfont-excess weight:500letter-spacing:.2px
“The attacker has produced a large amount of effort and hard work to make all these pretend personas, only to produce quite clear malware,” VulnCheck researcher Jacob Baines explained. “It truly is unclear if they have been thriving, but given that they’ve continued to go after this avenue of attacks, it looks they believe they will be successful.”
It’s presently not acknowledged if this is the work of an amateur actor or an innovative persistent menace (APT). But security scientists have beforehand arrive under the radar of North Korean country-point out teams, as exposed by Google in January 2021.
If something, the conclusions present the have to have for doing exercises caution when it arrives to downloading code from open up resource repositories. It’s also crucial that customers scrutinize the code prior to execution to be certain they will not pose any security challenges.
Discovered this posting attention-grabbing? Stick to us on Twitter and LinkedIn to study far more exceptional written content we article.
Some components of this report are sourced from:
thehackernews.com

 Europol Warns of Metaverse and AI Terror Threat
Europol Warns of Metaverse and AI Terror Threat