An Android voice phishing (aka vishing) malware campaign recognized as FakeCalls has reared its head after all over again to focus on South Korean people below the guise of over 20 well known money applications.
“FakeCalls malware possesses the operation of a Swiss military knife, capable not only to perform its most important intention but also to extract private data from the victim’s system,” cybersecurity agency Check Place mentioned.
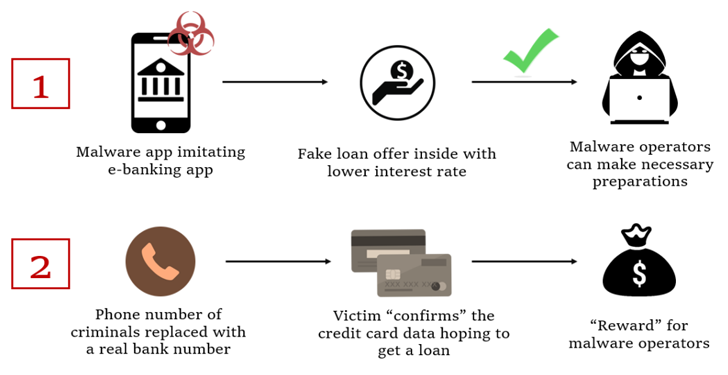
FakeCalls was beforehand documented by Kaspersky in April 2022, describing the malware’s capabilities to imitate phone discussions with a lender shopper support agent.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
In the noticed attacks, people who put in the rogue banking app are enticed into calling the monetary establishment by providing a pretend reduced-interest financial loan.
At the point where by the phone contact actually comes about, a pre-recorded audio with directions from the authentic bank is played. At the identical time, malware also conceals the phone range with the bank’s genuine selection to give the perception that a dialogue is taking place with an true lender staff on the other end.
The final target of the campaign to get the victim’s credit score card details, which the menace actors claim is expected to qualify for the non-existent bank loan.
The destructive application also requests for intrusive permissions so as to harvest sensitive facts, together with dwell audio and movie streams, from the compromised device, which are then exfiltrated to a remote server.
The most current FakeCalls samples even further carry out several strategies to remain underneath the radar. One of the methods entails including a massive amount of documents inside nested directories to the APK’s asset folder, producing the size of the file identify and path to breach the 300-character limit.
“The malware builders took specific treatment with the complex factors of their generation as effectively as applying various special and efficient anti-examination methods,” Test Position reported. “In addition, they devised mechanisms for disguised resolution of the command-and-handle servers guiding the operations.”
When the attack exclusively focuses on South Korea, the cybersecurity enterprise has warned that the very same methods can be repurposed to focus on other locations throughout the planet.
The findings also come as Cyble drop mild on two Android banking trojans dubbed Nexus and GoatRAT that can harvest useful knowledge and carry out economic fraud.
Nexus, a rebranded model of SOVA, also incorporates a ransomware module that encrypts the stored data files and can abuse Android’s accessibility services to extract seed phrases from cryptocurrency wallets.
WEBINARDiscover the Concealed Dangers of 3rd-Party SaaS Applications
Are you mindful of the threats linked with 3rd-party app access to your company’s SaaS applications? Sign up for our webinar to discover about the types of permissions being granted and how to reduce risk.
RESERVE YOUR SEAT
In contrast, GoatRAT is designed to concentrate on Brazilian financial institutions and joins the likes of BrasDex and PixPirate to dedicate fraudulent dollars transfer in excess of the PIX payments system though exhibiting a fake overlay window to conceal the exercise.
The advancement is portion of a escalating trend exactly where menace actors have unleashed progressively advanced banking malware to automate the entire method of unauthorized funds transfers on infected gadgets.
Cybersecurity organization Kaspersky claimed it detected 196,476 new cell banking trojans and 10,543 new mobile ransomware trojans in 2022, with China, Syria, Iran, Yemen, and Iraq emerging as the prime international locations attacked by cell malware, such as adware.
Spain, Saudi Arabia, Australia, Turkey, China, Switzerland, Japan, Colombia, Italy, and India lead the list of best nations around the world contaminated by cell fiscal threats.
“Irrespective of the decline in all round malware installers, the ongoing progress of mobile banking Trojans is a clear indicator that cybercriminals are concentrating on monetary get,” Kaspersky researcher Tatyana Shishkova stated.
Uncovered this posting fascinating? Abide by us on Twitter and LinkedIn to browse a lot more exceptional written content we put up.
Some pieces of this post are sourced from:
thehackernews.com


 Telegram, WhatsApp Trojanized to Target Cryptocurrency Wallets
Telegram, WhatsApp Trojanized to Target Cryptocurrency Wallets