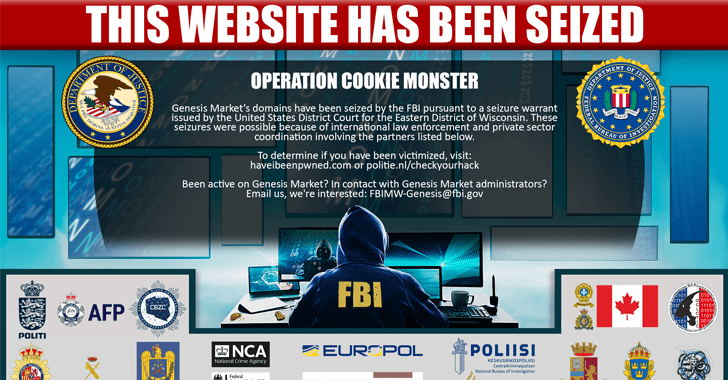
A coordinated global law enforcement operation has dismantled Genesis Sector, an illegal on the web marketplace that specialized in the sale of stolen qualifications associated with email, lender accounts, and social media platforms.
Coinciding with the infrastructure seizure, the important crackdown, which involved authorities from 17 nations around the world, culminated in 119 arrests and 208 home queries in 13 nations. Even so, the .onion mirror of the marketplace seems to be nonetheless up and jogging.
The “unparalleled” law enforcement physical exercise has been codenamed Operation Cookie Monster.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
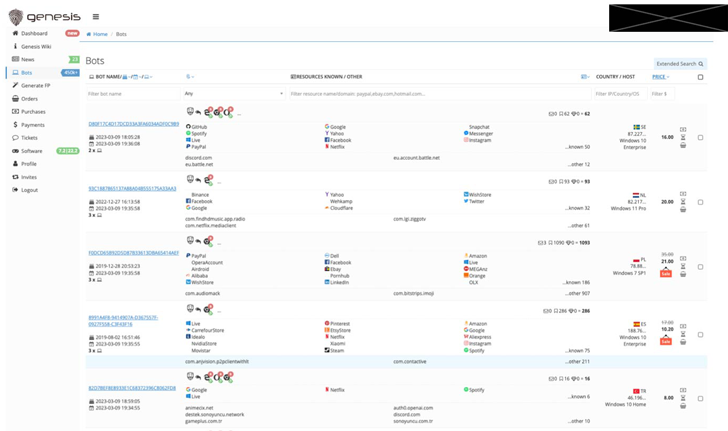
Genesis Market, considering that its inception in March 2018, evolved into a major hub for legal actions, offering accessibility to data stolen from around 1.5 million compromised pcs throughout the environment totaling additional than 80 million credentials.
A greater part of bacterial infections involved with Genesis Market place connected malware have been detected in the U.S., Mexico, Germany, Turkey, Sweden, Italy, France, Spain, Poland, Ukraine, Saudi Arabia, India, Pakistan, and Indonesia, amongst other people, for each data collected by Trellix.
Some of the outstanding malware households dispersed through the company to compromise victims contain AZORult, Raccoon, RedLine, and DanaBot, which are all able of thieving sensitive details from users’ systems. Also shipped by means of DanaBot is a rogue Chrome extension developed to siphon browser facts.
“Account obtain credentials advertised for sale on Genesis Market place integrated those people connected to the economic sector, critical infrastructure, and federal, state, and neighborhood federal government organizations,” the U.S. Department of Justice (DoJ) explained in a assertion.
DoJ identified as Genesis Market a person of the “most prolific preliminary entry brokers (IABs) in the cybercrime entire world.”
Apart from qualifications, Genesis also peddled system fingerprints – which contain one of a kind identifiers and browser cookies – so as to help threat actors circumvent anti-fraud detection techniques utilised by several web-sites.
“The mix of stolen obtain qualifications, fingerprints, and cookies authorized purchasers to believe the identity of the target by tricking 3rd party websites into imagining the Genesis Market place person was the true proprietor of the account,” the DoJ included.
Court paperwork expose that the U.S. Federal Bureau of Investigation (FBI) obtained access to Genesis Market’s backend servers twice in December 2020 and May 2022, enabling the agency to accessibility details pertaining to about 59,000 customers of the cybercrime bazaar.
The packages of stolen details harvested from contaminated computers (aka “bots”) were being marketed for any where in between $.70 to several hundreds of pounds based on the character of the knowledge, in accordance to Europol and Eurojust.
“The most expensive would contain money info which would enable entry to on the web banking accounts,” Europol noted, stating the criminals paying for the knowledge had been also supplied with added equipment to use it without the need of attracting notice.
“Prospective buyers were being provided with a custom browser which would mimic the one particular of their target. This permitted the criminals to entry their victim’s account without the need of triggering any of the security steps from the platform the account was on.”
The proprietary Chromium-primarily based browser, referred to as Genesium browser, is cross-system, with the maintainers proclaiming options these as “nameless browsing” and other advanced functionalities that permit its end users to bypass anti-fraud devices.
Genesis Industry, as opposed to Hydra and other illicit marketplaces, was also obtainable over the clearnet, therefore lowering the barrier of entry for lesser-experienced menace actors searching to receive electronic identities in order to breach personal accounts and business methods.
Approaching WEBINARLearn to Safe the Identity Perimeter – Verified Methods
Strengthen your enterprise security with our impending professional-led cybersecurity webinar: Check out Identity Perimeter procedures!
Will not Miss out on Out – Save Your Seat!
The takedown is envisioned to have a “ripple impact all through the underground financial system” as threat actors look for for alternatives to fill the void remaining by Genesis Market place.
Genesis Market place is the most current in a long line of illegitimate products and services that have been taken down by legislation enforcement. It also comes accurately a 12 months after the dismantling of Hydra, which was felled by regulation enforcement in April 2022 and created a “seismic change in the Russian-language darknet market landscape.”
“Nearly a 12 months soon after Hydra’s takedown, 5 markets — Mega, Blacksprut, Solaris, Kraken, and OMG!OMG! Market — have emerged as the largest players based mostly on the quantity of delivers and the number of sellers,” Flashpoint explained in a new report.
The enhancement also follows the launch of a new dark web marketplace identified as STYX which is mostly geared towards financial fraud, cash laundering, and identity theft. It really is stated to have opened its doorways all-around January 19, 2023.
“Some illustrations of the particular service offerings marketed on STYX include things like cash-out products and services, info dumps, SIM playing cards, DDOS, 2FA/SMS bypass, bogus and stolen ID documents, banking malware, and much far more,” Resecurity stated in a in depth writeup.
Like Genesis Market place, STYX also delivers utilities that are designed to get around anti-fraud alternatives and access compromised accounts by working with granular electronic identifiers like stolen cookie files, physical product information, and network settings to spoof authentic purchaser logins.
The emergence of STYX as a new platform in the professional cybercriminal ecosystem is nevertheless a further sign that the industry for illegal solutions continues to be a fruitful small business, permitting undesirable actors to profit from credential theft and payment facts.
“The bulk of STYX Market sellers specialize in fraud and funds laundering providers targeting popular electronic banking platforms, on the web-marketplaces, e-commerce and other payment purposes,” Resecurity noted. “The geographies targeted by these danger actors are world, spanning the U.S., E.U., U.K., Canada, Australia and numerous countries in APAC and Center East.”
Uncovered this posting appealing? Follow us on Twitter and LinkedIn to study much more unique information we submit.
Some parts of this write-up are sourced from:
thehackernews.com

 UK Criminal Records Office Crippled by “Cyber Incident”
UK Criminal Records Office Crippled by “Cyber Incident”