The U.S. authorities is warning about the resurgence of BlackCat (aka ALPHV) ransomware attacks targeting the health care sector as lately as this thirty day period.
“Since mid-December 2023, of the almost 70 leaked victims, the health care sector has been the most normally victimized,” the govt explained in an up to date advisory.
“This is very likely in response to the ALPHV/BlackCat administrator’s write-up encouraging its affiliate marketers to focus on hospitals just after operational motion versus the group and its infrastructure in early December 2023.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The advisory arrives from the Federal Bureau of Investigation (FBI), the Cybersecurity and Infrastructure Security Company (CISA), and the Department of Well being and Human Companies (HHS).
The BlackCat ransomware operation suffered a main blow late previous 12 months following a coordinated legislation enforcement operation led to the seizure of its dark leak internet sites. But the takedown turned out to be a failure right after the team managed to get back handle of the web sites and switched to a new TOR info leak portal that carries on to continue to be lively to date.
It has also ramped up versus critical infrastructure organizations in recent months, owning claimed accountability for attacks on Prudential Monetary, LoanDepot, Trans-Northern Pipelines, and UnitedHealth Team subsidiary Optum.
The growth has prompted the U.S. govt to announce fiscal rewards of up to $15 million for details foremost to the identification of essential members as perfectly as affiliates of the e-crime group.

BlackCat’s ransomware spree coincides with the return of LockBit immediately after identical disruption efforts led by the U.K. Countrywide Criminal offense Company (NCA) final week.
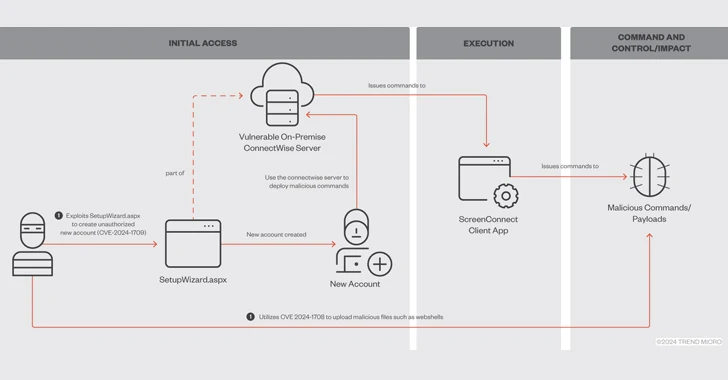
According to a report from SC Journal, threat actors breached Optum’s network by leveraging the not too long ago disclosed critical security flaws in ConnectWise’s ScreenConnect distant desktop and accessibility application.
The flaws, which make it possible for for remote code execution on inclined methods, have also been weaponized by the Black Basta and Bl00dy ransomware gangs as very well as by other danger actors to provide Cobalt Strike Beacons, XWorm, and even other remote management equipment like Atera, Syncro, and a further ScreenConnect client.
Attack area management firm Censys said it noticed far more than 3,400 exposed perhaps vulnerable ScreenConnect hosts online, with most of them situated in the U.S., Canada, the U.K., Australia, Germany, France, India, the Netherlands, Turkey, and Ireland.
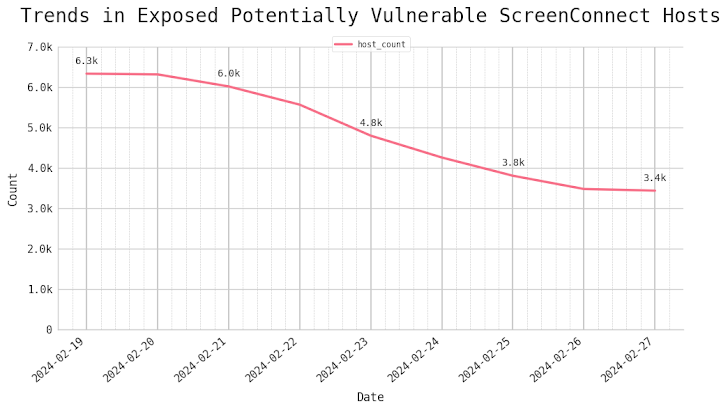
“It is really apparent that distant accessibility computer software like ScreenConnect carries on to be a key focus on for threat actors,” Censys security researcher Himaja Motheram claimed.
The conclusions occur as ransomware teams like RansomHouse, Rhysida, and a Phobos variant termed Backmydata have continued to compromise various companies in the U.S., U.K., Europe, and the Center East.
In a indication that these cybercrime teams are shifting to a lot more nuanced and subtle techniques, RansomHouse has formulated a custom instrument dubbed MrAgent to deploy the file-encrypting malware at scale.

“MrAgent is a binary designed to run on [VMware ESXi] hypervisors, with the sole reason of automating and tracking the deployment of ransomware across significant environments with a substantial range of hypervisor techniques,” Trellix reported. Details of MrAgent to start with came to light in September 2023.
Another significant tactic adopted by some ransomware groups is the sale of immediate network obtain as a new monetization approach by using their own weblogs, on Telegram channels, or information leak internet sites, KELA reported.
It also follows the public launch of a Linux-particular, C-centered ransomware danger recognized as Kryptina, which surfaced in December 2023 on underground community forums and has given that been created accessible for no cost on BreachForums by its creator.
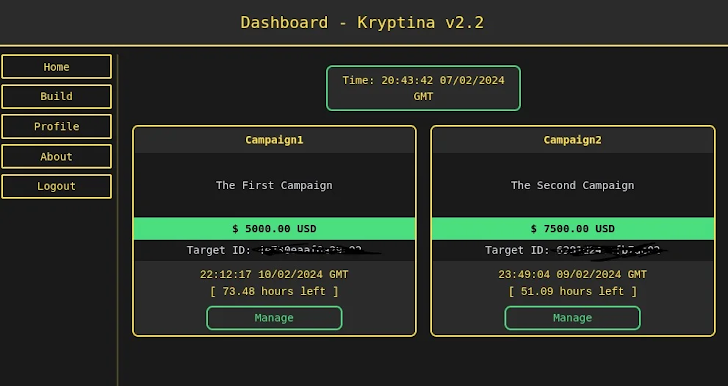
“The launch of the RaaS supply code, finish with in depth documentation, could have significant implications for the spread and effects of ransomware attacks versus Linux devices,” SentinelOne researcher Jim Walter stated.
“It is most likely to increase the ransomware builder’s attractiveness and usability, drawing in nevertheless extra small-competent individuals to the cybercrime ecosystem. There is also substantial risk that it will lead to the growth of a number of spin-offs and an improve in attacks.”
Identified this post attention-grabbing? Comply with us on Twitter and LinkedIn to study a lot more exclusive content material we post.
Some sections of this short article are sourced from:
thehackernews.com

 Building Your Privacy-Compliant Customer Data Platform (CDP) with First-Party Data
Building Your Privacy-Compliant Customer Data Platform (CDP) with First-Party Data