A new pressure of malware developed by risk actors likely affiliated with the FIN7 cybercrime group has been place to use by the users of the now-defunct Conti ransomware gang, indicating collaboration concerning the two crews.
The malware, dubbed Domino, is mainly made to facilitate stick to-on exploitation on compromised programs, including providing a lesser-acknowledged information stealer that has been marketed for sale on the dark web since December 2021.
“Former users of the TrickBot/Conti syndicate […] have been utilizing Domino considering the fact that at minimum late February 2023 to deliver possibly the Undertaking Nemesis details stealer or much more able backdoors this kind of as Cobalt Strike,” IBM Security X-Power security researcher Charlotte Hammond reported in a report published last week.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
FIN7, also named Carbanak and ITG14, is a prolific Russian-talking cybercriminal syndicate that is known to hire an array of custom made malware to deploy added malware and broaden its monetization methods.
Latest analyses by Google-owned Mandiant, SentinelOne, and PRODAFT have revealed the group’s function as a precursor for Maze and Ryuk ransomware attacks, not to point out exposing its connections to Black Basta, DarkSide, REvil, and LockBit households.
The most recent intrusion wave, noticed by IBM Security X-Pressure two months in the past, consists of the use of Dave Loader, a crypter earlier attributed to the Conti team (aka Gold Blackburn, ITG23, or Wizard Spider), to deploy the Domino backdoor.
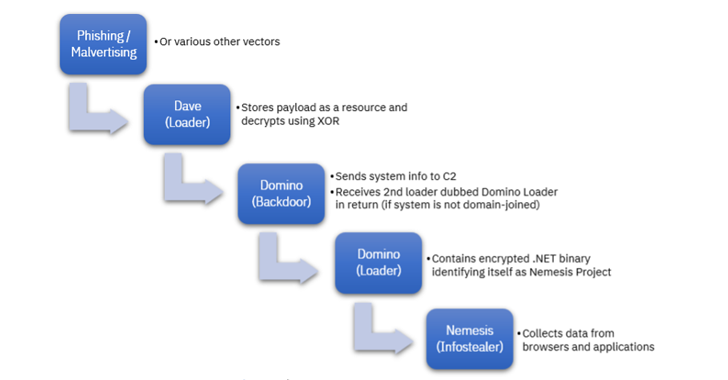
Domino’s probable connections to FIN7 will come from resource code overlaps with DICELOADER (aka Lizar or Tirion), a time-examined malware spouse and children attributed to the group. The malware, for its portion, is designed to get simple sensitive info and retrieve encrypted payloads from a remote server.
This upcoming-phase artifact is a 2nd loader codenamed Domino Loader, which harbors an encrypted .NET information stealer referred to as Task Nemesis that’s capable of amassing delicate information from clipboard, Discord, web browsers, crypto wallets, VPN solutions, and other applications.
“Domino has been lively in the wild considering the fact that at minimum October 2022, which notably is when Lizar observations commenced to lessen,” Hammond pointed out, indicating that the danger actors may perhaps be phasing out the latter.
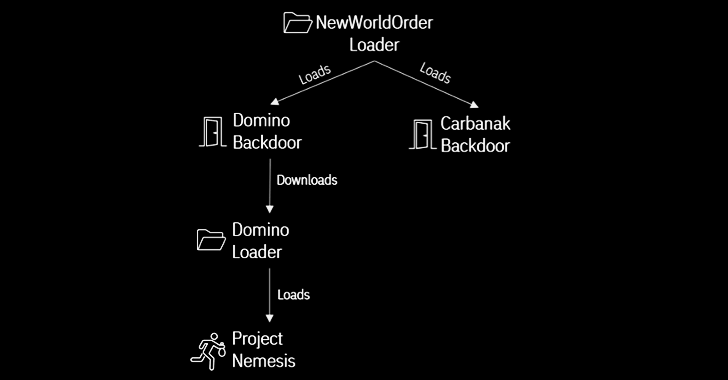
A different important url bridging Domino to FIN7 comes from December 2022 that leveraged a different loader known as NewWorldOrder Loader to produce the two the Domino and Carbanak backdoors.
Upcoming WEBINARMaster the Art of Dark Web Intelligence Accumulating
Learn the art of extracting threat intelligence from the dark web – Be part of this pro-led webinar!
Save My Seat!
The Domino backdoor and loader – equally 64-bit DLLs composed in Visible C++ – are reported to have been utilized to set up Job Nemesis due to the fact at least October 2022, prior to its use by ex-Conti members earlier this year.
The use of stealer malware by ransomware distributors is not without having precedent. In November 2022, Microsoft uncovered intrusions mounted by a menace actor recognised as DEV-0569 that leveraged BATLOADER malware to produce Vidar and Cobalt Strike, the latter of which finally facilitated human-operated ransomware attacks distributing Royal ransomware.
This has raised the probability that details stealers are deployed during decreased precedence bacterial infections (e.g., personal pcs), when these belonging to an Lively Listing domain are served with Cobalt Strike.
“The use of malware with ties to several groups in a solitary campaign — these as Dave Loader, Domino Backdoor and Challenge Nemesis Infostealer — highlights the complexity associated in monitoring risk actors but also supplies insight into how and with whom they operate,” Hammond concluded.
Identified this write-up appealing? Follow us on Twitter and LinkedIn to read through a lot more distinctive content we post.
Some components of this article are sourced from:
thehackernews.com

 What’s the Difference Between CSPM & SSPM?
What’s the Difference Between CSPM & SSPM?