The fiscally enthusiastic risk actor known as FIN7 has been observed leveraging destructive Google advertisements spoofing respectable brand names as a signifies to produce MSIX installers that culminate in the deployment of NetSupport RAT.
“The threat actors applied malicious web sites to impersonate very well-recognized brands, including AnyDesk, WinSCP, BlackRock, Asana, Concur, The Wall Avenue Journal, Workable, and Google Meet,” cybersecurity company eSentire explained in a report posted previously this week.
FIN7 (aka Carbon Spider and Sangria Tempest) is a persistent e-criminal offense group that is been active considering the fact that 2013, to begin with dabbling in attacks targeting place-of-sale (PoS) units to steal payment data, just before pivoting to breaching big corporations by way of ransomware campaigns.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

Over the decades, the menace actor has refined its strategies and malware arsenal, adopting various customized malware families these types of as BIRDWATCH, Carbanak, DICELOADER (aka Lizar and Tirion), POWERPLANT, POWERTRASH, and TERMITE, among the others.
FIN7 malware is usually deployed through spear-phishing campaigns as an entry to the goal network or host, whilst in recent months the team has used malvertising strategies to initiate the attack chains.
In December 2023, Microsoft reported it observed the attackers relying on Google adverts to entice users into downloading destructive MSIX application offers, which in the long run led to the execution of POWERTRASH, a PowerShell-centered in-memory dropper that is used to load NetSupport RAT and Gracewire.
“Sangria Tempest […] is a fiscally motivated cybercriminal group currently focusing on conducting intrusions that usually direct to knowledge theft, adopted by specific extortion or ransomware deployment such as Clop ransomware,” the tech huge famous at the time.
The abuse of MSIX as a malware distribution vector by multiple threat actors — very likely owing to its potential to bypass security mechanisms like Microsoft Defender SmartScreen — has considering that prompted Microsoft to disable the protocol handler by default.
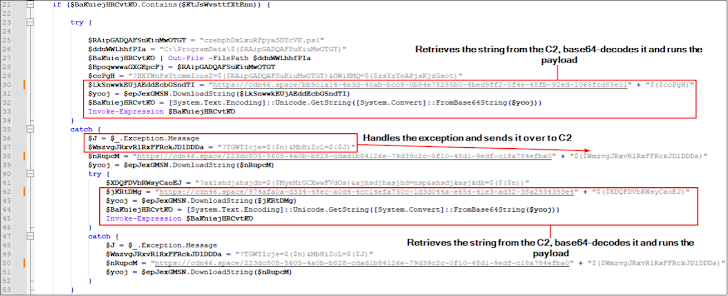
In the attacks noticed by eSentire in April 2024, consumers who go to the bogus web pages by using Google ads are displayed a pop-up information urging them to download a phony browser extension, which is an MSIX file that contains a PowerShell script that, in flip, gathers method data and contacts a distant server to fetch a different encoded PowerShell script.
The second PowerShell payload is employed to obtain and execute the NetSupport RAT from an actor-controlled server.
The Canadian cybersecurity organization reported it also detected the remote accessibility trojan staying applied to produce extra malware, which features DICELOADER by implies of a Python script.
“The incidents of FIN7 exploiting reliable brand name names and working with misleading web advertisements to distribute NetSupport RAT adopted by DICELOADER spotlight the ongoing threat, particularly with the abuse of signed MSIX files by these actors, which has demonstrated productive in their strategies,” eSentire stated.
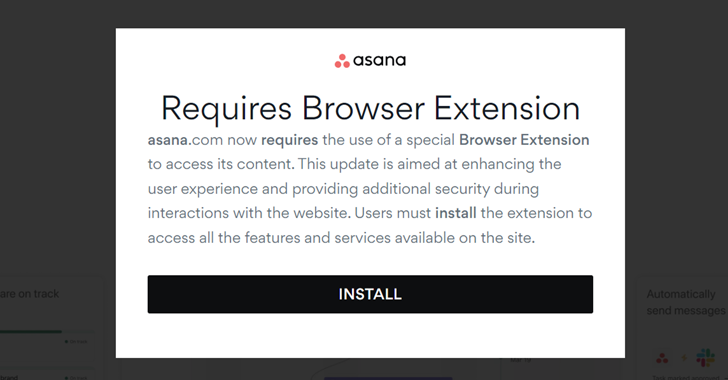
Very similar conclusions have been independently described by Malwarebytes, which characterized the action as singling out corporate end users via malicious advertisements and modals by mimicking substantial-profile manufacturers like Asana, BlackRock, CNN, Google Meet, SAP, and The Wall Avenue Journal. It, nevertheless, did not attribute the marketing campaign to FIN7.

Information of FIN7’s malvertising strategies coincides with a SocGholish (aka FakeUpdates) an infection wave that is intended to target small business partners.
“Attackers employed living-off-the-land approaches to obtain delicate credentials, and notably, configured web beacons in equally email signatures and network shares to map out neighborhood and company-to-company interactions,” eSentire stated. “This behavior would recommend an curiosity in exploiting these relationships to focus on small business friends of desire.”
It also follows the discovery of a malware campaign targeting Windows and Microsoft Workplace customers to propagate RATs and cryptocurrency miners by means of cracks for popular software package.
“The malware, after set up, often registers commands in the process scheduler to preserve persistence, enabling steady set up of new malware even following removing,” Broadcom-owned Symantec mentioned.
Located this write-up exciting? Follow us on Twitter and LinkedIn to browse a lot more exceptional written content we write-up.
Some parts of this short article are sourced from:
thehackernews.com

 North Korean Hackers Deploy New Golang Malware ‘Durian’ Against Crypto Firms
North Korean Hackers Deploy New Golang Malware ‘Durian’ Against Crypto Firms