The economically motivated FIN8 actor, in all chance, has resurfaced with a never-before-observed ransomware strain known as “White Rabbit” that was not long ago deployed from a neighborhood bank in the U.S. in December 2021.
That is in accordance to new results printed by Development Micro, contacting out the malware’s overlaps with Egregor, which was taken down by Ukrainian regulation enforcement authorities in February 2021.
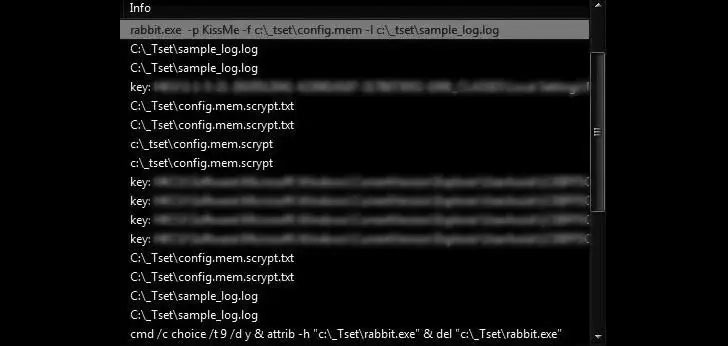
“1 of the most notable factors of White Rabbit’s attack is how its payload binary involves a precise command-line password to decrypt its internal configuration and carry on with its ransomware schedule,” the scientists noted. “This system of hiding destructive action is a trick that the ransomware family members Egregor utilizes to hide malware methods from analysis.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

Egregor, which commenced functions in September 2020 right until its operations took a substantial hit, is extensively considered to be a reincarnation of Maze, which shut down its felony business later that calendar year.
Besides getting a leaf out of Egregor’s playbook, White Rabbit adheres to the double extortion scheme and is believed to have been sent by way of Cobalt Strike, a article-exploitation framework which is put to use by menace actors to reconnoiter, infiltrate, and fall destructive payloads into the affected process.
Double extortion, also regarded as pay-now-or-get-breached, refers to an progressively popular ransomware approach in which useful details from the targets is exfiltrated prior to launching the encryption regime, followed by pressurizing the victims into having to pay up to avert the stolen info from remaining printed on line.
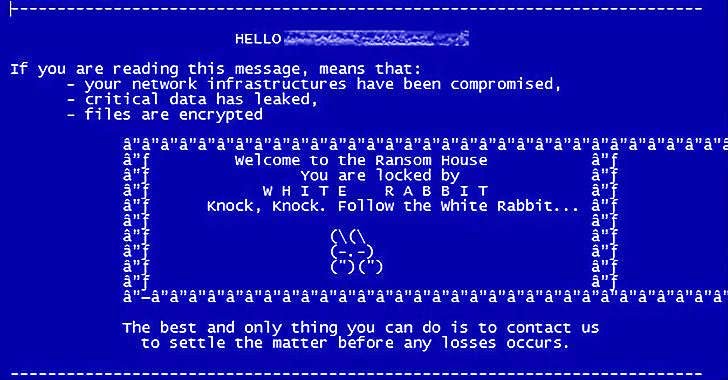
In fact, the ransom notice exhibited after the completion of the encryption course of action warns the victim that their details will be released or bought at the time the 4-working day deadline to satisfy their requires elapses. “We will also deliver the data to all intrigued supervisory organizations and the media,” the take note provides.
Though real-entire world attacks involving White Rabbit have obtained focus only lately, electronic forensic clues piecing with each other its path details to a string of malicious routines commencing as early as July 2021.
What’s more, examination of the ransomware samples dating back again to August 2021 demonstrates that the malware is an updated edition of the Sardonic backdoor, which Bitdefender explained past year as an actively made malware encountered in the aftermath of an unsuccessful attack targeting a monetary institution in the U.S.
“The actual romance concerning the White Rabbit group and FIN8 is at the moment not known,” cybersecurity enterprise Lodestone explained, introducing it located a “selection of TTPs suggesting that White Rabbit, if working independently of FIN8, has a near connection with the extra established threat team or is mimicking them.”
“Offered that FIN8 is recognized generally for its infiltration and reconnaissance resources, the link could be an indicator of how the team is increasing its arsenal to incorporate ransomware,” Pattern Micro stated. “So significantly, White Rabbit’s targets have been several, which could necessarily mean that they are even now testing the waters or warming up for a large-scale attack.”
Located this short article fascinating? Adhere to THN on Fb, Twitter and LinkedIn to go through a lot more distinctive articles we post.
Some components of this report are sourced from:
thehackernews.com


 Cyber incident strikes Gloucester City Council as residents suffer service outages
Cyber incident strikes Gloucester City Council as residents suffer service outages