A new Android subscription malware named Fleckpe has been unearthed on the Google Participate in Retail store, amassing extra than 620,000 downloads in overall considering that 2022.
Kaspersky, which discovered 11 applications on the formal application storefront, said the malware masqueraded as reputable photo enhancing apps, digicam, and smartphone wallpaper packs. The apps have due to the fact been taken down.
The operation generally focused customers from Thailand, whilst telemetry info collected by the Russian cybersecurity company has uncovered victims in Poland, Malaysia, Indonesia, and Singapore.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

The apps give the promised functionality to avoid increasing red flags, but conceal their actual purpose less than the hood. The listing of the offending applications is as follows –
- Elegance Digital camera Furthermore (com.splendor.digital camera.moreover.photoeditor)
- Attractiveness Image Digicam (com.applications.digital camera.images)
- Attractiveness Slimming Photograph Editor (com.beauty.slimming.pro)
- Fingertip Graffiti (com.attract.graffiti)
- GIF Digicam Editor (com.gif.digital camera.editor)
- Hd 4K Wallpaper (com.high definition.h4ks.wallpaper)
- Impressionism Pro Digicam (com.impressionism.prozs.app)
- Microclip Video clip Editor (com.microclip.vodeoeditor)
- Night time Manner Digicam Pro (com.urox.opixe.nightcamreapro)
- Picture Digital camera Editor (com.toolbox.photoeditor)
- Photograph Impact Editor (com.picture.pictureframe)
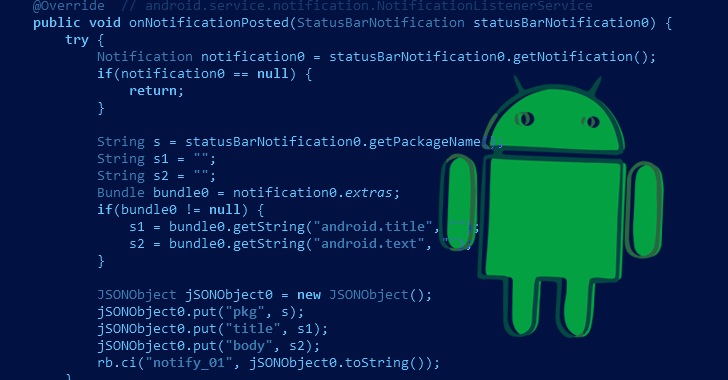
“When the application starts off, it loads a seriously obfuscated native library that contains a malicious dropper that decrypts and runs a payload from the app belongings,” Kaspersky researcher Dmitry Kalinin stated.
The payload, for its aspect, is developed to make contact with a remote server and transmit details about the compromised product (e.g., Cellular State Code and Cellular Network Code), adhering to which the server responds back again with a paid out membership site.
The malware subsequently opens the web site in an invisible web browser window and attempts to subscribe on the user’s behalf by abusing its permissions to accessibility notifications and receive the confirmation code required to entire the phase.
In a indication that Fleckpe is staying actively produced, latest variations of the malware have moved most of the malicious features to the native library in a bid to evade detection by security resources.
Approaching WEBINARLearn to Halt Ransomware with Real-Time Defense
Sign up for our webinar and learn how to prevent ransomware attacks in their tracks with real-time MFA and service account security.
Help save My Seat!
“The payload now only intercepts notifications and views web web pages, acting as a bridge among the native code and the Android components required for purchasing a subscription,” Kalinin pointed out.
“Not like the native library, the payload has following to no evasion abilities, though the malicious actors did add some code obfuscation to the most recent variation.”
This is not the 1st time membership malware has been observed on the Google Engage in Retail outlet. Fleckpe joins other fleeceware households like Joker (aka Bread or Jocker) and Harly, which subscribe contaminated products to undesirable premium services and perform billing fraud.
Even though such apps are not as hazardous as spy ware or financial trojans, they can nevertheless incur unauthorized charges and be repurposed by its operators to harvest a extensive range of sensitive info and serve as entry factors for much more nefarious malware.
If just about anything, the conclusions are nonetheless a further sign that menace actors are continuing to uncover new methods to sneak their apps onto formal app marketplaces to scale their campaigns, demanding that consumers physical exercise warning when downloading applications and granting permissions to them.
“Growing complexity of the trojans has allowed them to efficiently bypass numerous anti-malware checks carried out by the marketplaces, remaining undetected for very long periods of time,” Kalinin explained.
Located this report attention-grabbing? Abide by us on Twitter and LinkedIn to examine much more unique written content we article.
Some areas of this report are sourced from:
thehackernews.com

 Cisco Warns of Vulnerability in Popular Phone Adapter, Urges Migration to Newer Model
Cisco Warns of Vulnerability in Popular Phone Adapter, Urges Migration to Newer Model