An ongoing malvertising marketing campaign is becoming utilized to distribute virtualized .NET loaders that are designed to deploy the FormBook facts-stealing malware.
“The loaders, dubbed MalVirt, use obfuscated virtualization for anti-evaluation and evasion together with the Windows Process Explorer driver for terminating procedures,” SentinelOne researchers Aleksandar Milenkoski and Tom Hegel stated in a technical publish-up.
The change to Google malvertising is the hottest case in point of how crimeware actors are devising alternate shipping and delivery routes to distribute malware at any time due to the fact Microsoft declared plans to block the execution of macros in Place of work by default from information downloaded from the internet.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Malvertising entails positioning rogue research motor advertisements in hopes of tricking consumers exploring for well-known software package like Blender into downloading the trojanized computer software.
The MalVirt loaders, which are executed in .NET, use the genuine KoiVM virtualizing protector for .NET applications for concealing its behavior and are tasked with distributing the FormBook malware relatives.
Moreover incorporating anti-examination and anti-detection methods to evade execution in just a digital device or an application sandbox natural environment, the loaders have been found to utilize a modified version of KoiVM that packs in added obfuscation layers in get to make deciphering even much more challenging.
The loaders also deploy and load a signed Microsoft Process Explorer driver with the aim of carrying out actions with elevated permissions. The privileges, for instance, can be weaponized to terminate processes with security application to steer clear of receiving flagged.
The two FormBook and its successor, XLoader, carry out a large variety of functionalities, this kind of as keylogging, screenshot theft, harvesting of web and other qualifications, and staging of further malware.
The malware strains are also noteworthy for camouflaging their command-and-regulate (C2) traffic among the smokescreen HTTP requests with encoded written content to a number of decoy domains, as formerly revealed by Zscaler and Check Stage very last calendar year.
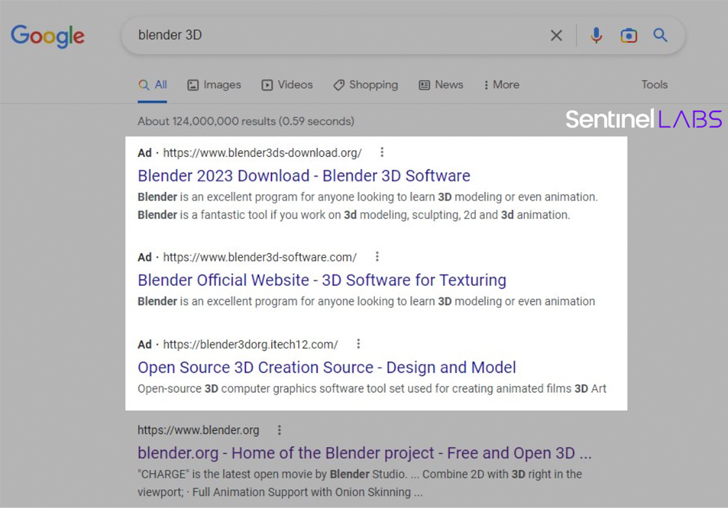
“As a response to Microsoft blocking Place of work macros by default in files from the Internet, threat actors have turned to option malware distribution strategies – most lately, malvertising,” the researchers claimed.
“The MalVirt loaders […] display just how a lot exertion menace actors are investing in evading detection and thwarting assessment.”
It can be pertinent that the method is presently witnessing a spike because of to its use by other criminal actors to thrust IcedID, Raccoon, Rhadamanthys, and Vidar stealers more than the past couple of months.
“It is likely that a threat actor has began to market malvertising as a support on the dark web, and there is a good offer of demand from customers,” Abuse.ch mentioned in a report, pointing out a doable reason for the “escalation.”
The results get there two months just after India-based K7 Security Labs in-depth a phishing campaign that leverages a .NET loader to drop Remcos RAT and Agent Tesla by indicates of a virtualized KoiVM virtualized binary.
It is not all malicious ads, having said that, as adversaries are also experimenting with other file styles like Excel include-ins (XLLs) and OneNote email attachments to sneak earlier security perimeters. Freshly joining this record is the use of Visual Studio Resources for Business (VSTO) add-ins as an attack auto.
“VSTO incorporate-ins can be packaged along with Business office files (Neighborhood VSTO), or, alternatively, fetched from a remote spot when a VSTO-Bearing Office environment document is opened (Distant VSTO),” Deep Instinct disclosed past 7 days. “This, nevertheless, may perhaps have to have bypass of trust-relevant security mechanisms.”
Found this posting fascinating? Stick to us on Twitter and LinkedIn to read more distinctive articles we submit.
Some sections of this posting are sourced from:
thehackernews.com

 PixPirate: New Android Banking Trojan Targeting Brazilian Financial Institutions
PixPirate: New Android Banking Trojan Targeting Brazilian Financial Institutions